The FBI and authorities in The Netherlands this week seized dozens of servers and domains for a vastly widespread spam and malware dissemination service working out of Pakistan. The proprietors of the service, who use the collective nickname “The Manipulaters,” have been the topic of three tales printed right here since 2015. The FBI stated the principle clientele are organized crime teams that attempt to trick sufferer firms into making funds to a 3rd occasion.
Certainly one of a number of present Fudtools websites run by the principals of The Manipulators.
On January 29, the FBI and the Dutch nationwide police seized the technical infrastructure for a cybercrime service marketed below the manufacturers Heartsender, Fudpage and Fudtools (and plenty of different “fud” variations). The “fud” bit stands for “Absolutely Un-Detectable,” and it refers to cybercrime sources that can evade detection by safety instruments like antivirus software program or anti-spam home equipment.
The Dutch authorities said 39 servers and domains overseas have been seized, and that the servers contained hundreds of thousands of information from victims worldwide — together with a minimum of 100,000 information pertaining to Dutch residents.
A statement from the U.S. Division of Justice refers back to the cybercrime group as Saim Raza, after a pseudonym The Manipulaters communally used to advertise their spam, malware and phishing providers on social media.
“The Saim Raza-run web sites operated as marketplaces that marketed and facilitated the sale of instruments similar to phishing kits, rip-off pages and e-mail extractors typically used to construct and keep fraud operations,” the DOJ defined.
The core Manipulaters product is Heartsender, a spam supply service whose homepage brazenly marketed phishing kits concentrating on customers of varied Web firms, together with Microsoft 365, Yahoo, AOL, Intuit, iCloud and ID.me, to call a couple of.
The federal government says transnational organized crime teams that bought these providers primarily used them to run business email compromise (BEC) schemes, whereby the cybercrime actors tricked sufferer firms into making funds to a 3rd occasion.
“These funds would as an alternative be redirected to a monetary account the perpetrators managed, leading to important losses to victims,” the DOJ wrote. “These instruments have been additionally used to accumulate sufferer consumer credentials and make the most of these credentials to additional these fraudulent schemes. The seizure of those domains is meant to disrupt the continued exercise of those teams and cease the proliferation of those instruments throughout the cybercriminal group.”
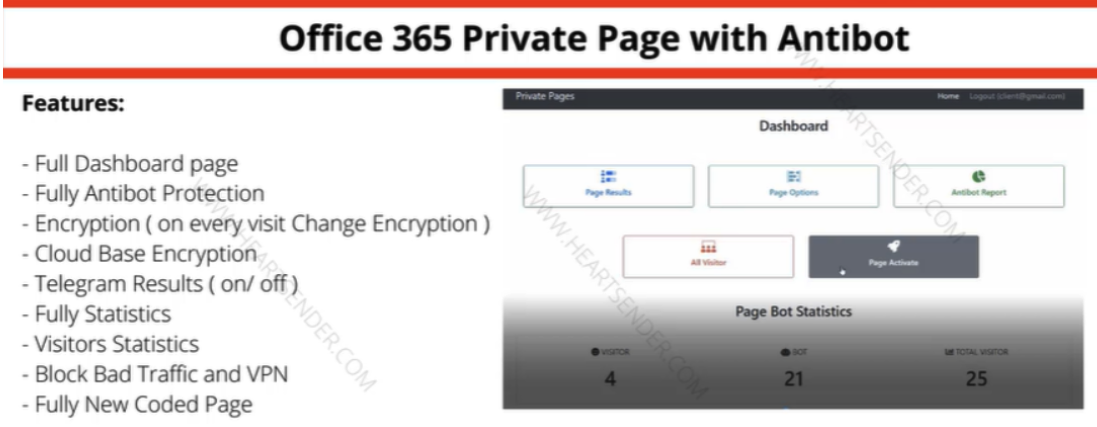
Manipulaters commercial for “Workplace 365 Personal Web page with Antibot” phishing equipment offered by way of Heartsender. “Antibot” refers to performance that makes an attempt to evade automated detection strategies, preserving a phish deployed and accessible so long as attainable. Picture: DomainTools.
KrebsOnSecurity first wrote about The Manipulaters in May 2015, primarily as a result of their adverts on the time have been blanketing quite a lot of widespread cybercrime boards, and since they have been pretty open and brazen about what they have been doing — even who they have been in actual life.
We caught up with The Manipulaters once more in 2021, with a story that discovered the core staff had began an internet coding firm in Lahore referred to as WeCodeSolutions — presumably as a strategy to account for his or her appreciable Heartsender earnings. That piece examined how WeCodeSolutions staff had all doxed themselves on Fb by posting photos from firm events every year that includes a big cake with the phrases FudCo written in icing.
A follow-up story last year about The Manipulaters prompted messages from varied WeCodeSolutions staff who pleaded with this publication to take away tales about them. The Saim Raza identification informed KrebsOnSecurity they have been lately launched from jail after being arrested and charged by native police, though they declined to elaborate on the costs.
The Manipulaters by no means appeared to care a lot about defending their very own identities, so it’s not stunning that they have been unable or unwilling to guard their very own prospects. In an analysis launched final yr, DomainTools.com discovered the web-hosted model of Heartsender leaked a rare quantity of consumer info to unauthenticated customers, together with buyer credentials and e-mail information from Heartsender staff.

Nearly yearly since their founding, The Manipulaters have posted an image of a FudCo cake from an organization occasion celebrating its anniversary.
DomainTools additionally uncovered proof that the computer systems utilized by The Manipulaters have been all contaminated with the identical password-stealing malware, and that huge numbers of credentials have been stolen from the group and offered on-line.
“Satirically, the Manipulaters could create extra short-term threat to their very own prospects than legislation enforcement,” DomainTools wrote. “The information desk ‘Consumer Feedbacks’ (sic) exposes what look like buyer authentication tokens, consumer identifiers, and even a buyer help request that exposes root-level SMTP credentials–all seen by an unauthenticated consumer on a Manipulaters-controlled area.”
Police in The Netherlands stated the investigation into the homeowners and prospects of the service is ongoing.
“The Cybercrime Staff is on the path of quite a lot of patrons of the instruments,” the Dutch nationwide police stated. “Presumably, these patrons additionally embody Dutch nationals. The investigation into the makers and patrons of this phishing software program has not but been accomplished with the seizure of the servers and domains.”
U.S. authorities this week additionally joined legislation enforcement in Australia, France, Greece, Italy, Romania and Spain in seizing quite a lot of domains for a number of long-running cybercrime boards and providers, together with Cracked and Nulled. In line with a statement from the European police company Europol, the 2 communities attracted greater than 10 million customers in complete.
Different domains seized as a part of “Operation Expertise” included Sellix, an e-commerce platform that was continuously utilized by cybercrime discussion board members to purchase and promote illicit items and providers.













