Researchers this month uncovered a two-year-old Linux-based distant entry trojan dubbed AVrecon that enslaves Web routers into botnet that bilks on-line advertisers and performs password-spraying assaults. Now new findings reveal that AVrecon is the malware engine behind a 12-year-old service known as SocksEscort, which rents hacked residential and small enterprise gadgets to cybercriminals trying to conceal their true location on-line.
Picture: Lumen’s Black Lotus Labs.
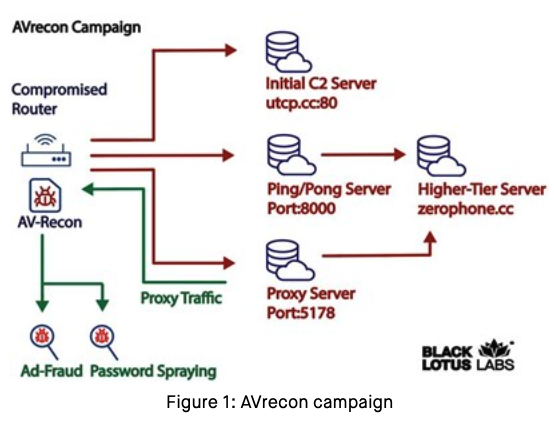
In a report launched July 12, researchers at Lumen’s Black Lotus Labs known as the AVrecon botnet “one of many largest botnets concentrating on small-office/home-office (SOHO) routers seen in latest historical past,” and a criminal offense machine that has largely evaded public consideration since first being noticed in mid-2021.
“The malware has been used to create residential proxy providers to shroud malicious exercise similar to password spraying, web-traffic proxying and advert fraud,” the Lumen researchers wrote.
Malware-based anonymity networks are a serious supply of undesirable and malicious internet site visitors directed at on-line retailers, Web service suppliers (ISPs), social networks, e mail suppliers and monetary establishments. And a terrific many of those “proxy” networks are marketed primarily to cybercriminals in search of to anonymize their site visitors by routing it by an contaminated PC, router or cellular machine.
Proxy providers can be utilized in a professional method for a number of enterprise functions — similar to worth comparisons or gross sales intelligence — however they’re massively abused for hiding cybercrime exercise as a result of they make it tough to hint malicious site visitors to its unique supply. Proxy providers additionally let customers look like getting on-line from almost anyplace on the planet, which is beneficial if you happen to’re a cybercriminal who’s making an attempt to impersonate somebody from a selected place.
Spur.us, a startup that tracks proxy providers, informed KrebsOnSecurity that the Web addresses Lumen tagged because the AVrecon botnet’s “Command and Management” (C2) servers all tie again to a long-running proxy service known as SocksEscort.
SocksEscort[.]com, is what’s often called a “SOCKS Proxy” service. The SOCKS (or SOCKS5) protocol permits Web customers to channel their Net site visitors by a proxy server, which then passes the data on to the meant vacation spot. From a web site’s perspective, the site visitors of the proxy community buyer seems to originate from a rented/malware-infected PC tied to a residential ISP buyer, not from the proxy service buyer.
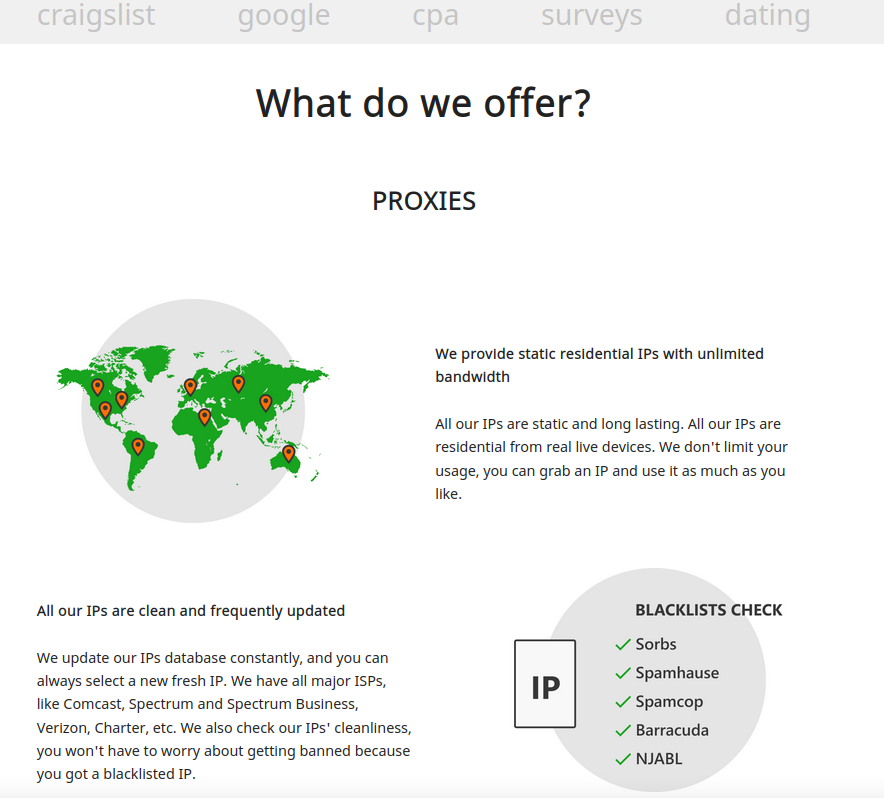
The SocksEscort residence web page says its providers are good for folks concerned in automated on-line exercise that usually leads to IP addresses getting blocked or banned, similar to Craigslist and courting scams, search engine outcomes manipulation, and on-line surveys.
Spur tracks SocksEscort as a malware-based proxy providing, which suggests the machines doing the proxying of site visitors for SocksEscort clients have been contaminated with malicious software program that turns them right into a site visitors relay. Often, these customers do not know their methods are compromised.
Spur says the SocksEscort proxy service requires clients to put in a Home windows primarily based software so as to entry a pool of greater than 10,000 hacked gadgets worldwide.
“We created a fingerprint to determine the call-back infrastructure for SocksEscort proxies,” Spur co-founder Riley Kilmer mentioned. “ community telemetry, we have been in a position to affirm that we noticed victims speaking again to it on numerous ports.”
In response to Kilmer, AVrecon is the malware that provides SocksEscort its proxies.
“When Lumen launched their report and IOCs [indicators of compromise], we queried our system for which proxy service call-back infrastructure overlapped with their IOCs,” Kilmer continued. “The second stage C2s they recognized have been the identical because the IPs we labeled for SocksEscort.”
Lumen’s analysis crew mentioned the aim of AVrecon seems to be stealing bandwidth – with out impacting end-users – so as to create a residential proxy service to assist launder malicious exercise and keep away from attracting the identical degree of consideration from Tor-hidden services or commercially accessible VPN providers.
“This class of cybercrime exercise menace could evade detection as a result of it’s much less seemingly than a crypto-miner to be observed by the proprietor, and it’s unlikely to warrant the amount of abuse complaints that internet-wide brute-forcing and DDoS-based botnets usually draw,” Lumen’s Black Lotus researchers wrote.
Preserving bandwidth for each clients and victims was a major concern for SocksEscort in July 2022, when 911S5 — on the time the world’s largest identified malware proxy community — got hacked and imploded simply days after being exposed in a story here. Kilmer mentioned after 911’s demise, SocksEscort closed its registration for a number of months to stop an inflow of recent customers from swamping the service.
Danny Adamitis, principal info safety researcher at Lumen and co-author of the report on AVrecon, confirmed Kilmer’s findings, saying the C2 information matched up with what Spur was seeing for SocksEscort courting again to September 2022.
Adamitis mentioned that on July 13 — the day after Lumen revealed analysis on AVrecon and began blocking any site visitors to the malware’s management servers — the folks answerable for sustaining the botnet reacted shortly to transition contaminated methods over to a brand new command and management infrastructure.
“They have been clearly reacting and making an attempt to take care of management over elements of the botnet,” Adamitis mentioned. “Most likely, they needed to maintain that income stream going.”
Frustratingly, Lumen was not in a position to decide how the SOHO gadgets have been being contaminated with AVrecon. Some attainable avenues of an infection embody exploiting weak or default administrative credentials on routers, and outdated, insecure firmware that has identified, exploitable safety vulnerabilities.
WHO’S BEHIND SOCKSESCORT?
KrebsOnSecurity briefly visited SocksEscort last year and promised a follow-up on the historical past and attainable identification of its proprietors. A overview of the earliest posts about this service on Russian cybercrime boards suggests the 12-year-old malware proxy community is tied to a Moldovan firm that additionally gives VPN software program on the Apple Retailer and elsewhere.
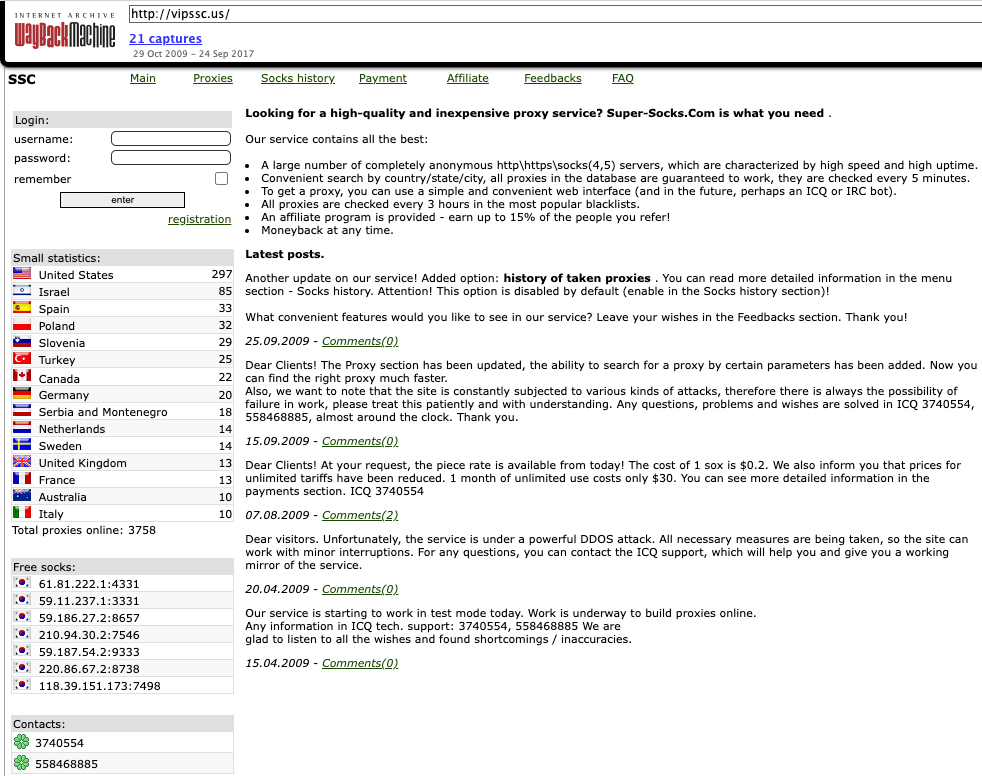
SocksEscort started in 2009 as “super-socks[.]com,” a Russian-language service that bought entry to 1000’s of compromised PCs that could possibly be used to proxy site visitors. Somebody who picked the nicknames “SSC” and “super-socks” and e mail handle “[email protected]” registered on a number of cybercrime boards and commenced selling the proxy service.
In response to DomainTools.com, the apparently associated e mail handle “[email protected]” was used to register SocksEscort[.]com, super-socks[.]com, and some different proxy-related domains, together with ip-score[.]com, segate[.]org seproxysoft[.]com, and vipssc[.]us. Cached variations of each super-socks[.]com and vipssc[.]us present these websites bought the identical proxy service, and each displayed the letters “SSC” prominently on the high of their homepages.
Picture: Archive.org. Web page translation from Russian by way of Google Translate.
In response to cyber intelligence agency Intel 471, the very first “SSC” identification registered on the cybercrime boards occurred in 2009 on the Russian language hacker neighborhood Antichat, the place SSC registered utilizing the e-mail handle [email protected]. SSC requested fellow discussion board members for assist in testing the safety of a web site they claimed was theirs: myiptest[.]com, which promised to inform guests whether or not their proxy handle was included on any safety or anti-spam block lists.
DomainTools says myiptest[.]com was registered in 2008 to an Adrian Crismaru from Chisinau, Moldova. Myiptest[.]com is now not responding, however a cached copy of it from Archive.org exhibits that for about 4 years it included in its HTML supply a Google Analytics code of US-2665744, which was additionally current on greater than a dozen different web sites.
Many of the websites that after bore that Google monitoring code are now not on-line, however almost all of them centered round providers that have been just like myiptest[.]com, similar to abuseipdb[.]com, bestiptest[.]com, checkdnslbl[.]com, dnsbltools[.]com and dnsblmonitor[.]com.
Every of those providers have been designed to assist guests shortly decide whether or not the Web handle they have been visiting the positioning from was listed by any safety corporations as spammy, malicious or phishous. In different phrases, these providers have been designed in order that proxy service customers may simply inform if their rented Web handle was nonetheless protected to make use of for on-line fraud.
One other area with the Google Analytics code US-2665744 was sscompany[.]internet. An archived copy of the site says SSC stands for “Server Assist Firm,” which marketed outsourced options for technical assist and server administration. The corporate was situated in Chisinau, Moldova and owned by Adrian Crismaru.
Leaked copies of the hacked Antichat discussion board point out the SSC identification tied to [email protected] registered on the discussion board utilizing the IP handle 71.229.207.214. That very same IP was used to register the nickname “Deem3n®,” a prolific poster on Antichat between 2005 and 2009 who served as a moderator on the discussion board.
There was a Deem3n® person on the webmaster discussion board Searchengines.guru whose signature of their posts says they run a well-liked neighborhood catering to programmers in Moldova known as sysadmin[.]md, and that they have been a methods administrator for sscompany[.]internet.
That very same Google Analytics code can be now current on the homepages of wiremo[.]co and a VPN supplier known as HideIPVPN[.]com.
Wiremo sells software program and providers to assist web site homeowners higher handle their buyer critiques. Wiremo’s Contact Us web page lists a “Server Administration LLC” in Wilmington, DE because the dad or mum firm. Information from the Delaware Secretary of State point out Crismaru is CEO of this firm.
Server Administration LLC is currently listed in Apple’s App Retailer because the proprietor of a “free” VPN app known as HideIPVPN. The contact info on Crismaru’s LinkedIn page says his firm web sites embody myiptest[.]com, sscompany[.]internet, and hideipvpn[.]com.
“The easiest way to safe the transmissions of your cellular machine is VPN,” reads HideIPVPN’s description on the Apple Retailer. “Now, we offer you an excellent simpler manner to hook up with our VPN servers. We are going to conceal your IP handle, encrypt all of your site visitors, safe all of your delicate info (passwords, mail bank card particulars, and many others.) type [sic] hackers on public networks.”
Mr. Crismaru didn’t reply to a number of requests for remark. When requested in regards to the firm’s obvious connection to SocksEscort, Wiremo responded, “We don’t management this area and nobody from our crew is linked to this area.” Wiremo didn’t reply when introduced with the findings on this report.















