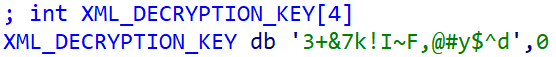ESET researchers have found a marketing campaign that we attribute to the APT group often called Evasive Panda, the place replace channels of reputable purposes had been mysteriously hijacked to ship the installer for the MgBot malware, Evasive Panda’s flagship backdoor.
Key factors of the report:
- Customers in mainland China had been focused with malware delivered by means of updates for software program developed by Chinese language corporations.
- We analyze the competing hypotheses of how the malware may have been delivered to focused customers.
- With excessive confidence we attribute this exercise to the Evasive Panda APT group.
- We offer an outline of Evasive Panda’s signature backdoor MgBot and its toolkit of plugin modules.
Evasive Panda profile
Evasive Panda (also referred to as BRONZE HIGHLAND and Daggerfly) is a Chinese language-speaking APT group, active since at least 2012. ESET Analysis has noticed the group conducting cyberespionage in opposition to people in mainland China, Hong Kong, Macao, and Nigeria. Authorities entities had been focused in China, Macao, and Southeast and East Asian international locations, particularly Myanmar, the Philippines, Taiwan, and Vietnam, whereas different organizations in China and Hong Kong had been additionally focused. In response to public reviews, the group has additionally focused unknown entities in Hong Kong, India, and Malaysia.
The group implements its personal customized malware framework with a modular structure that permits its backdoor, often called MgBot, to obtain modules to spy on its victims and improve its capabilities.
Marketing campaign overview
In January 2022, we found that whereas performing updates, a reputable Chinese language software had obtained an installer for the Evasive Panda MgBot backdoor. Throughout our investigation, we found that the malicious exercise went again to 2020.
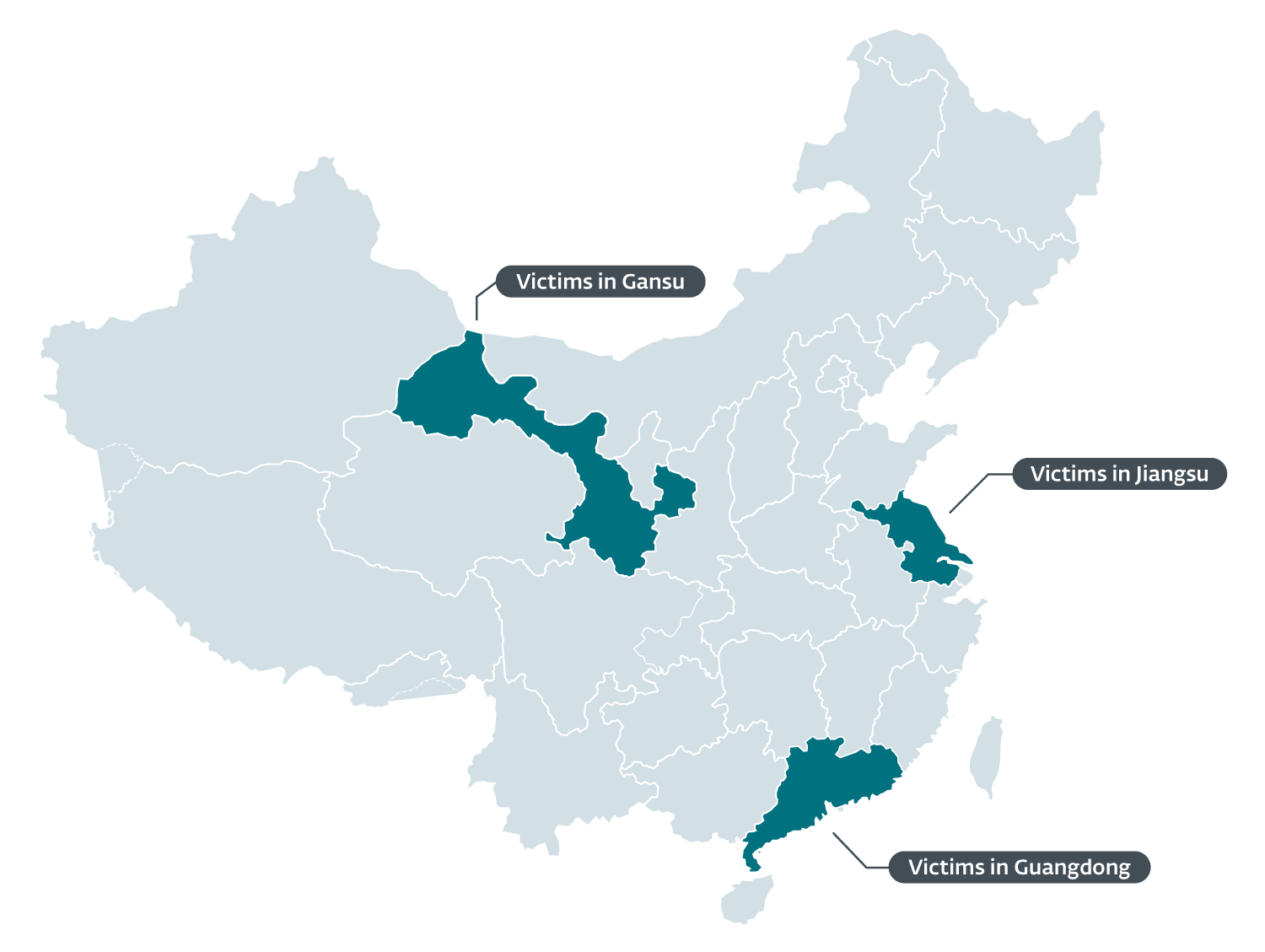
Chinese language customers had been the main focus of this malicious exercise, which ESET telemetry reveals beginning in 2020 and persevering with all through 2021. The focused customers had been positioned within the Gansu, Guangdong, and Jiangsu provinces, as proven in Determine 1.
The vast majority of the Chinese language victims are members of a global NGO that operates in two of the beforehand talked about provinces.
One further sufferer was additionally found to be positioned within the nation of Nigeria.
Attribution
Evasive Panda makes use of a customized backdoor often called MgBot, which was publicly documented in 2014 and has seen little evolution since then; to one of the best of our information, the backdoor has not been utilized by another group. On this cluster of malicious exercise, solely the MgBot malware was noticed deployed on victimized machines, together with its toolkit of plugins. Subsequently, with excessive confidence we attribute this exercise to Evasive Panda.
Technical evaluation
Throughout our investigation, we found that when performing automated updates, a reputable software software program part downloaded MgBot backdoor installers from reputable URLs and IP addresses.
In Desk 1, we offer the URL from the place the obtain originated, in accordance with ESET telemetry knowledge, together with the IP addresses of the servers, as resolved on the time by the consumer’s system; subsequently, we imagine that these IP addresses are reputable. In response to passive DNS data, all of those IP addresses match the noticed domains, subsequently we imagine that these IP addresses are reputable.
Desk 1. Malicious obtain areas in accordance with ESET telemetry
| URL | First seen | Area IP | ASN | Downloader |
|---|---|---|---|---|
| http://replace.browser.qq[.]com/qmbs/QQ/QQUrlMgr_QQ88_4296.exe | 2020‑11‑02 | 123.151.72[.]74 | AS58542 | QQUrlMgr.exe QQ.exe QQLive.exe QQCall<XX>.exe |
| 183.232.96[.]107 | AS56040 | |||
| 61.129.7[.]35 | AS4811 |
Hypotheses of compromise
After we analyzed the chance of a number of strategies that would clarify how the attackers managed to ship malware by means of reputable updates, we had been left with two situations: supply-chain compromise, and adversary-in-the-middle assaults. For each situations we may even take into consideration antecedents of comparable assaults by different Chinese language-speaking APT teams.
Tencent QQ is a well-liked Chinese language chat and social media service. Within the subsequent sections, we’ll use the Tencent QQ Home windows shopper software program updater, QQUrlMgr.exe (listed in Desk 1), for our examples, provided that now we have the very best variety of detections from downloads by this explicit part.
Provide-chain compromise situation
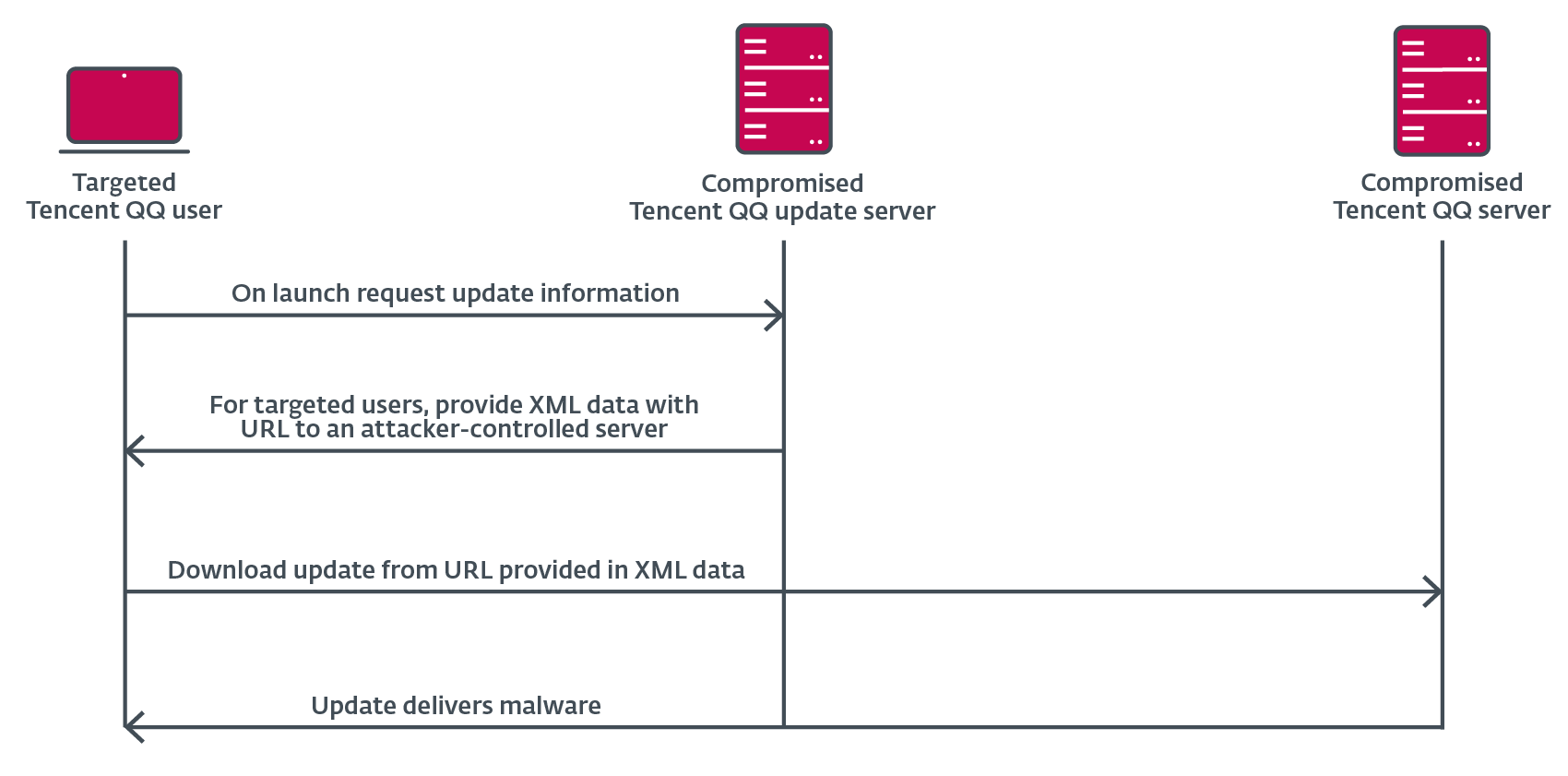
Given the focused nature of the assaults, we speculate that attackers would have wanted to compromise the QQ replace servers to introduce a mechanism to establish the focused customers to ship them the malware, filtering out non-targeted customers and delivering them reputable updates – we registered instances the place reputable updates had been downloaded by means of the identical abused protocols.
Whereas not an Evasive Panda case, a primary instance of the sort of compromise is in our report Operation NightScout: Supply‑chain attack targets online gaming in Asia, the place attackers compromised the replace servers of a software program developer firm based mostly in Hong Kong. In response to our telemetry, greater than 100,000 customers had the BigNox software program put in, however solely 5 had malware delivered by means of an replace. We suspect that the attackers compromised the BigNox API on the replace server to answer to the updater part on the machines of focused customers with a URL to a server the place the attackers hosted their malware; non-targeted customers had been despatched the reputable replace URL.
Based mostly on that antecedent, in Determine 2 we illustrate how the supply-chain compromise situation may have unfolded in accordance with observations in our telemetry. Nonetheless, we should warn the reader that that is purely hypothesis and based mostly on our static evaluation, with very restricted data, of QQUrlMgr.exe (SHA-1: DE4CD63FD7B1576E65E79D1D10839D676ED20C2B).
It is usually value noting that in our analysis we had been by no means capable of retrieve a pattern of the XML “replace” knowledge – neither a reputable, nor a malicious, XML pattern – from the server contacted by QQUrlMgr.exe. The “replace examine” URL is hardcoded, in obfuscated kind, within the executable, as proven in Determine 3.
Deobfuscated, the whole replace examine URL is:
http://c.gj.qq[.]com/fcgi-bin/busxml?busid=20&supplyid=30088&guid=CQEjCF9zN8Zdyzj5S6F1MC1RGUtw82B7yL+hpt9/gixzExnawV3y20xaEdtektfo&dm=0
The server responds with XML-formatted knowledge encoded with base64 and encrypted with an implementation of the TEA algorithm utilizing a 128-bit key. This knowledge incorporates directions to obtain and execute a file, together with different data. For the reason that decryption key can be hardcoded, as proven in Determine 4, it might be identified to the attackers.
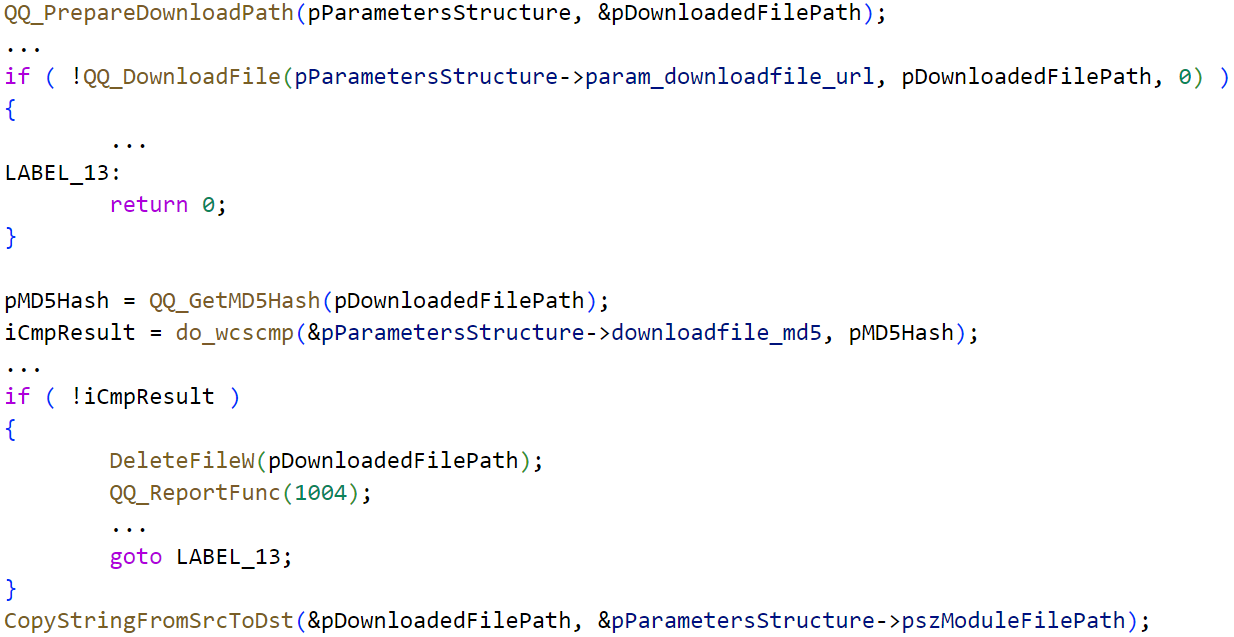
QQUrlMgr.exe then downloads the indicated file, unencrypted, by way of HTTP and hashes its contents with the MD5 algorithm. The result’s checked in opposition to a hash current within the replace examine response XML knowledge, as seen in Determine 5. If the hashes match, QQUrlMgr.exe executes the downloaded file. This reinforces our speculation that the attackers would wish to regulate the XML server-side mechanism within the replace server to have the ability to present the proper MD5 hash of the malware installer.
We imagine that this situation would clarify our observations; nonetheless, many questions are left unanswered. We reached out to Tencent’s Security Response Center to verify the legitimacy of the complete URL from the place the malware was downloaded; replace.browser.qq[.]com is – on the time of writing – unreachable, however Tencent couldn’t verify whether or not the complete URL was reputable.
Adversary-in-the-middle situation
On 2022-06-02, Kaspersky printed a research report concerning the capabilities of the Chinese language-speaking LuoYu APT group and their WinDealer malware. Much like what we noticed on this cluster of Evasive Panda victims, their researchers discovered that, since 2020, victims of LuoYu had obtained the WinDealer malware by means of updates by way of the reputable software qgametool.exe from the PPTV software program, additionally developed by a Chinese language firm.
WinDealer has a puzzling functionality: as an alternative of carrying a listing of established C&C servers to contact in case of a profitable compromise, it generates random IP addresses within the 13.62.0.0/15 and 111.120.0.0/14 ranges from China Telecom AS4134. Though a small coincidence, we seen that the IP addresses of the focused Chinese language customers on the time of receiving the MgBot malware had been on the AS4134 and AS4135 IP addresses ranges.
Attainable explanations for what allows these capabilities for its C&C infrastructure are that LuoYu both management a considerable amount of gadgets related to the IP addresses on these ranges, or that they can do adversary-in-the-middle (AitM) or attacker-on-the-side interception on the infrastructure of that specific AS.
AitM kinds of interception could be doable if the attackers – both LuoYu or Evasive Panda – had been capable of compromise weak gadgets akin to routers or gateways. As an antecedent, in 2019 ESET researchers discovered that the Chinese language APT group often called BlackTech was performing AitM assaults by means of compromised ASUS routers and delivering the Plead malware by means of ASUS WebStorage software program updates.
With entry to ISP spine infrastructure – by means of authorized or unlawful means – Evasive Panda would be capable to intercept and reply to the replace requests carried out by way of HTTP, and even modify packets on the fly. In April 2023, Symantec researchers reported on Evasive Panda concentrating on a telecommunications group in Africa.
Wrap-up
Finally, with out additional proof, we can’t show or discard one speculation in favor of the opposite, provided that such capabilities are at hand for Chinese language APT teams.
Toolset
MgBot
MgBot is the first Home windows backdoor utilized by Evasive Panda, which in accordance with our findings has existed since a minimum of 2012 and, as talked about on this weblog publish, was publicly documented at VirusBulletin in 2014. It was developed in C++ with an object-oriented design, and has the capabilities to speak by way of TCP and UDP, and lengthen its performance by way of plugin modules.
MgBot’s installer and backdoor, and their performance, haven’t modified considerably because it was first documented. Its chain of execution is identical as described on this report by Malwarebytes from 2020.
MgBot Plugins
MgBot’s modular structure permits it to increase its performance by receiving and deploying modules on the compromised machine. Desk 2 lists the identified plugins and their performance. You will need to observe that the plugins don’t have distinctive inner identification numbers; subsequently we’re figuring out them right here by their DLL names on disk, which now we have by no means seen change.
Desk 2. Record of plugin DLL information
| Plugin DLL title | Overview |
|---|---|
| Kstrcs.dll | Keylogger. It solely actively logs keystrokes when the foreground window belongs to a course of named QQ.exe and the window title matches QQEdit. It is possible goal is the Tencent QQ chat software. |
| sebasek.dll | File stealer. Has a configuration file that allows the gathering of information from completely different sources: HDDs, USB thumb drives, and CD-ROMs; in addition to standards based mostly on the file properties: filename should include a key phrase from a predefined checklist, file dimension have to be between an outlined a minimal and most dimension. |
| Cbmrpa.dll | Captures textual content copied to the clipboard and logs data from the USBSTOR registry key. |
| pRsm.dll | Captures enter and output audio streams. |
| mailLFPassword.dll | Credential stealer. Steals credentials from Outlook and Foxmail electronic mail shopper software program. |
| agentpwd.dll | Credential stealer. Steals credentials from Chrome, Opera, Firefox, Foxmail, QQBrowser, FileZilla, and WinSCP, amongst others. |
| qmsdp.dll | A posh plugin designed to steal the content material from the Tencent QQ database that shops the consumer’s message historical past. That is achieved by in-memory patching of the software program part KernelUtils.dll and dropping a pretend userenv.dll DLL. |
| wcdbcrk.dll | Info stealer for Tencent WeChat. |
| Gmck.dll | Cookies stealer for Firefox, Chrome, and Edge. |
The vast majority of the plugins are designed to steal data from extremely fashionable Chinese language purposes akin to QQ, WeChat, QQBrowser, and Foxmail – all of them purposes developed by Tencent.
Conclusion
We found a marketing campaign that we attribute to the Evasive Panda APT group, concentrating on customers in mainland China, delivering their MgBot backdoor by means of replace protocols of purposes from well-known Chinese language corporations. We additionally analyzed the plugins of the MgBot backdoor and located the vast majority of them are designed to spy on customers of Chinese language software program by stealing credentials and knowledge.
IoCs
Information
| SHA-1 | Filename | Detection | Description |
|---|---|---|---|
| 10FB52E4A3D5D6BDA0D22BB7C962BDE95B8DA3DD | wcdbcrk.dll | Win32/Agent.VFT | MgBot data stealer plugin. |
| E5214AB93B3A1FC3993EF2B4AD04DFCC5400D5E2 | sebasek.dll | Win32/Agent.VFT | MgBot file stealer plugin. |
| D60EE17418CC4202BB57909BEC69A76BD318EEB4 | kstrcs.dll | Win32/Agent.VFT | MgBot keylogger plugin. |
| 2AC41FFCDE6C8409153DF22872D46CD259766903 | gmck.dll | Win32/Agent.VFT | MgBot cookie stealer plugin. |
| 0781A2B6EB656D110A3A8F60E8BCE9D407E4C4FF | qmsdp.dll | Win32/Agent.VFT | MgBot data stealer plugin. |
| 9D1ECBBE8637FED0D89FCA1AF35EA821277AD2E8 | pRsm.dll | Win32/Agent.VFT | MgBot audio seize plugin. |
| 22532A8C8594CD8A3294E68CEB56ACCF37A613B3 | cbmrpa.dll | Win32/Agent.ABUJ | MgBot clipboard textual content seize plugin. |
| 970BABE49945B98EFADA72B2314B25A008F75843 | agentpwd.dll | Win32/Agent.VFT | MgBot credential stealer plugin. |
| 8A98A023164B50DEC5126EDA270D394E06A144FF | maillfpassword.dll | Win32/Agent.VFT | MgBot credential stealer plugin. |
| 65B03630E186D9B6ADC663C313B44CA122CA2079 | QQUrlMgr_QQ88_4296.exe | Win32/Kryptik.HRRI | MgBot installer. |
Community
| IP | Supplier | First seen | Particulars |
|---|---|---|---|
| 122.10.88[.]226 | AS55933 Cloudie Restricted | 2020-07-09 | MgBot C&C server. |
| 122.10.90[.]12 | AS55933 Cloudie Restricted | 2020-09-14 | MgBot C&C server. |
MITRE ATT&CK strategies
This desk was constructed utilizing version 12 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
|---|---|---|---|
| Useful resource Improvement | T1583.004 | Purchase Infrastructure: Server | Evasive Panda acquired servers for use for C&C infrastructure. |
| T1587.001 | Develop Capabilities: Malware | Evasive Panda develops its customized MgBot backdoor and plugins, together with obfuscated loaders. | |
| Execution | T1059.003 | Command and Scripting Interpreter: Home windows Command Shell | MgBot’s installer launches the service from BAT information with the command web begin AppMgmt |
| T1106 | Native API | MgBot’s installer makes use of the CreateProcessInternalW API to execute rundll32.exe to load the backdoor DLL. | |
| T1569.002 | System Providers: Service Execution | MgBot is executed as a Home windows service. | |
| Persistence | T1543.003 | Create or Modify System Course of: Home windows Service | MgBot replaces the trail of the prevailing Utility Administration service DLL with its personal. |
| Privilege Escalation | T1548.002 | Abuse Elevation Management Mechanism: Bypass Consumer Account Management | MgBot performs UAC Bypass. |
| Protection Evasion | T1140 | Deobfuscate/Decode Information or Info | MgBot’s installer decrypts an embedded CAB file that incorporates the backdoor DLL. |
| T1112 | Modify Registry | MgBot modifies the registry for persistence. | |
| T1027 | Obfuscated Information or Info | MgBot’s installer incorporates embedded malware information and encrypted strings. MgBot incorporates encrypted strings. MgBot plugins include embedded DLL information. | |
| T1055.002 | Course of Injection: Transportable Executable Injection | MgBot can inject Transportable Executable information to distant processes. | |
| Credential Entry | T1555.003 | Credentials from Password Shops: Credentials from Internet Browsers | MgBot plugin module agentpwd.dll steals credential from internet browsers. |
| T1539 | Steal Internet Session Cookie | MgBot plugin module Gmck.dll steals cookies. | |
| Discovery | T1082 | System Info Discovery | MgBot collects system data. |
| T1016 | System Community Configuration Discovery | MgBot has the aptitude to get better community data. | |
| T1083 | File and Listing Discovery | MgBot has the aptitude of making file listings. | |
| Assortment | T1056.001 | Enter Seize: Keylogging | MgBot plugin module kstrcs.dll is a keylogger. |
| T1560.002 | Archive Collected Information: Archive by way of Library | MgBot’s plugin module sebasek.dll makes use of aPLib to compress information staged for exfiltration. | |
| T1123 | Audio Seize | MgBot’s plugin module pRsm.dll captures enter and output audio streams. | |
| T1119 | Automated Assortment | MgBot’s plugin modules seize knowledge from numerous sources. | |
| T1115 | Clipboard Information | MgBot’s plugin module Cbmrpa.dll captures textual content copied to the clipboard. | |
| T1025 | Information from Detachable Media | MgBot’s plugin module sebasek.dll collects information from detachable media. | |
| T1074.001 | Information Staged: Native Information Staging | MgBot’s plugin modules stage knowledge regionally on disk. | |
| T1114.001 | E-mail Assortment: Native E-mail Assortment | MgBot’s plugin modules are designed to steal credentials and electronic mail data from a number of purposes. | |
| T1113 | Display Seize | MgBot can seize screenshots. | |
| Command and Management | T1095 | Non-Utility Layer Protocol | MgBot communicates with its C&C by means of TCP and UDP protocols. |
| Exfiltration | T1041 | Exfiltration Over C2 Channel | MgBot performs exfiltration of collected knowledge by way of C&C. |