Cellular Safety
WhatsApp, Telegram and Sign clones and mods stay a preferred automobile for malware distribution. Don’t get taken for a trip.
10 Jan 2024
•
,
5 min. learn

Cellular functions make the world go spherical. Immediate communication providers are among the many hottest apps on iOS and Android alike – US non-profit operation Sign has an estimated 40 million customers, with the determine rising to 700 million for Telegram, one other open-source messaging service. In the meantime, Meta-owned WhatsApp is the undisputed global leader with an estimated two billion month-to-month lively customers.
However their recognition has additionally attracted the scrutiny of risk actors, eager to discover a strategy to sneak malware onto your device. It might find yourself costing you and even your employer pricey.
The cyber-risks of malicious copycat apps
Malicious builders have develop into fairly expert at tricking customers into downloading their wares. Typically they’ll produce malicious copycat apps designed to imitate professional ones. They’ll then distribute them through phishing messages in e mail, by textual content, on social media or the communications app itself, taking the sufferer to a rip-off web page and mislead them into putting in what they consider to be an official app. Or they might direct customers to legitimate-looking pretend app that will sometimes make it via the strict vetting procedures on the Google Play market. Apple’s iOS platform has a far more locked-down ecosystem and it’s even much less uncommon for malicious apps to finish up there.
At any price, should you obtain and set up a malicious app on you cellphone, it might expose you or your employer to a variety of threats together with:
- theft of delicate private knowledge, which might be offered on the darkish net to id fraudsters
- theft of banking/monetary data, which might be used to empty funds
- efficiency points, as a result of malicious apps might change the system’s settings and options and gradual it down
- adware that floods the system with unwatched promoting, making it troublesome to make use of
- spy ware designed to eavesdrop in your conversations, messages and different data
- ransomware designed to utterly lock down the system till a charge is paid
- premium-rate providers which the malware might covertly use, racking up enormous payments
- theft of logins for delicate accounts, which might be offered to scammers
- company cyberattacks designed to steal your work logins or knowledge, with a view to accessing delicate company knowledge or deploying ransomware
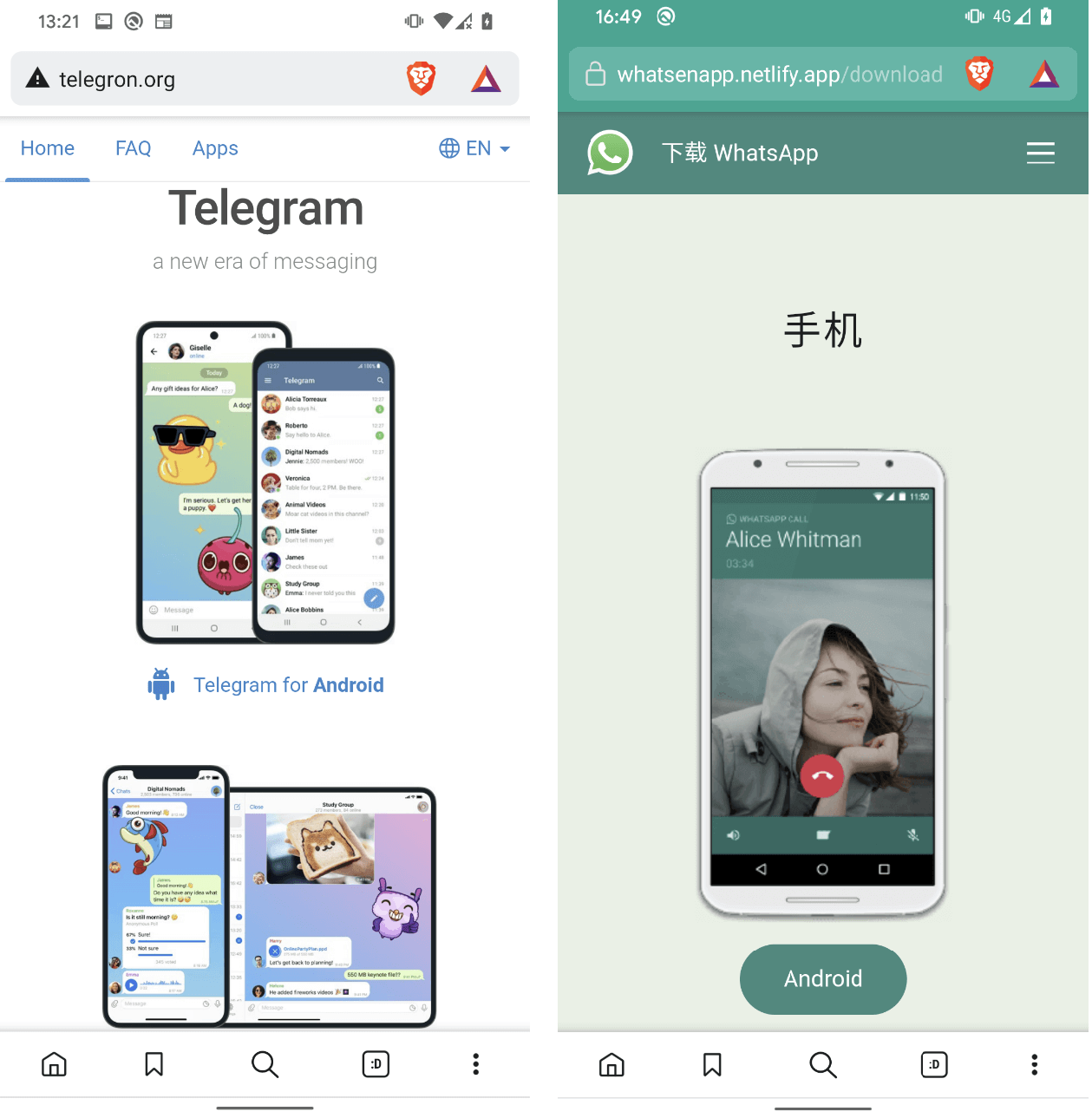
What ESET has seen
These threats have develop into more and more widespread over current years. Some are opportunistic assaults on a variety of shoppers, whereas others are extra extremely focused. Among the many most notable malicious copycat apps ESET has noticed embrace:
- A 2021 fake update campaign that unfold on WhatsApp, Sign and different messaging apps through phishing messages claiming the recipient might get hold of a brand new coloration theme for WhatsApp. In actuality, the WhatsApp pink theme was Trojan malware which mechanically replied to messages obtained in WhatsApp and different messaging apps with a malicious hyperlink.
- Dozens of copycat WhatsApp and Telegram websites touting malicious messaging apps generally known as “clippers” – designed to steal or modify the contents of the system clipboard. Victims have been first enticed by Google Adverts resulting in fraudulent YouTube channels, which then redirected them to the copycat web sites. As soon as put in, the apps have been designed to intercept victims’ chat messages in a bid to pilfer their delicate data and cryptocurrency funds.
- China-aligned hackers hid cyberespionage malware generally known as Android BadBazaar inside legitimate-looking Sign and Telegram apps. Each app sorts made it via official vetting and onto the Google Play and Samsung Galaxy Retailer, earlier than Google/Samsung have been made conscious of it.

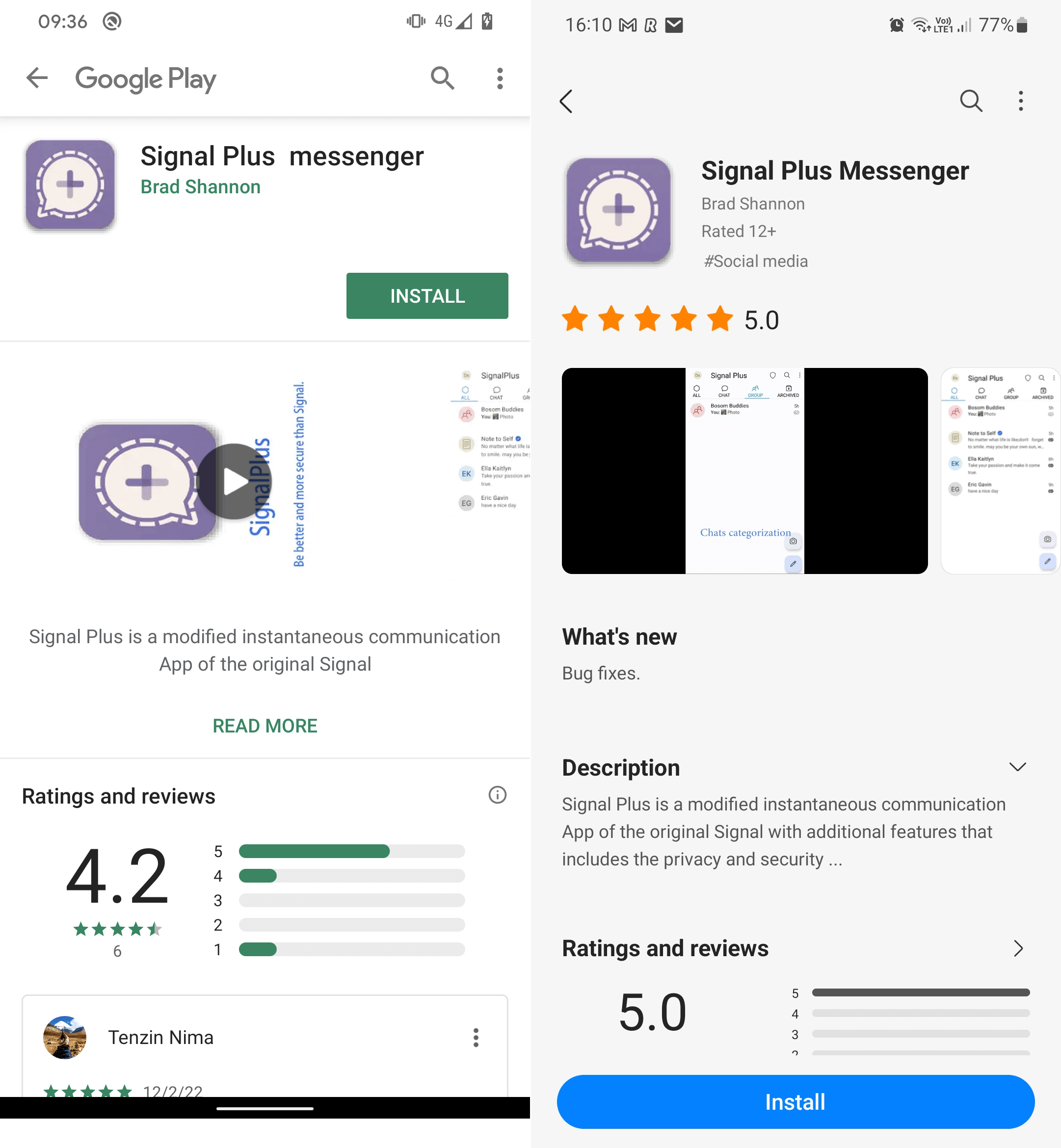
Taking precautions towards malicious apps
Whereas WhatsApp explicitly bans unofficial variations of its app, the open-source Telegram encourages third-party builders to create their very own Telegram shoppers. That may make discerning the actual from the pretend much more tough for customers. That stated, there are a number of issues you are able to do to cut back the possibilities of putting in one thing nasty in your system.
Right here’s a fast test record:
- At all times persist with official Android app shops, as they’ve rigorous vetting processes in place to maintain malicious apps off the platform.
- At all times maintain your mobile operating system and software on the latest version as malware will typically attempt to exploit bugs in older variations.
- Earlier than downloading, all the time test the developer’s repute on-line and any evaluations for the app – watching out for point out of scams.
- Uninstall any apps that you don’t use, so it’s simpler to maintain observe of what’s in your system.
- Don’t click on on hyperlinks or attachments, particularly if they seem in unsolicited social media messages or emails and invite you to obtain software program from third-party websites.
- Keep away from clicking on promoting on-line, in case it’s a part of a rip-off designed to steer you to a malicious copycat app.
- Be cautious of granting an app permissions that seem unrelated to its functionality, because it might be malware making an attempt to entry your knowledge.
- At all times use a cell safety answer from a good supplier as it will assist to dam malicious installs and/or forestall malware working in your system.
- Think about using biometric logins reasonably than mere passwords in your accounts.
- By no means obtain something from high-risk websites, equivalent to many grownup leisure or gaming platforms.

Easy methods to spot the indicators of an imposter app
It additionally pays to be looking out for uncommon exercise in your system, in case malware slips via despite your finest efforts. With that in thoughts, keep in mind:
- If one thing doesn’t sound correct concerning the app’s title, description and “official app” claims, or the developer’s pedigree, likelihood is excessive you’re coping with an imposter app
- Concentrate on persistent pop-up adverts as it might imply you’ve put in adware
- Preserve a watch out for any uncommon icons in your display screen which can have not too long ago been put in
- Concentrate on battery draining extra quickly than common or different unusual habits
- Regulate payments and knowledge utilization per thirty days; something excessively excessive might point out malicious exercise
- Perceive that in case your system is working slower than common, it might be right down to malware
Smartphones and tablets are our gateway to the digital world. But it surely’s a world we have to safe from uninvited friends. With these easy steps you’ll stand a a lot better probability of defending your funds and your private knowledge. For a deeper dive into how you can cope with pretend apps, learn our 7 tips for spotting a fake mobile app.