Cybersixgill
Insider Threats: Authorities and army
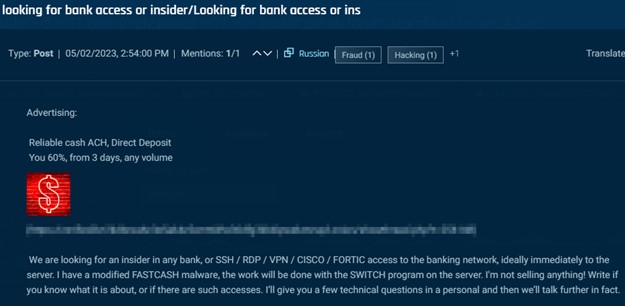
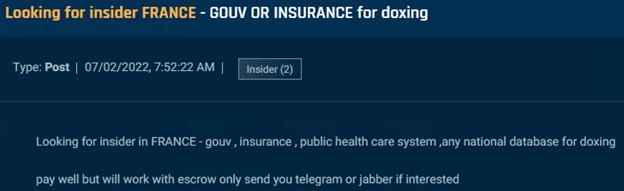
Transcending from cybercrime to espionage, we found a number of posts through which actors solicited governmental or government-affiliated insiders to offer data. This consists of people, like within the picture beneath, who can present nationwide citizen databases to help in doxing. An actor looking for an insider within the French authorities to offer citizen knowledge.
Cybersixgill
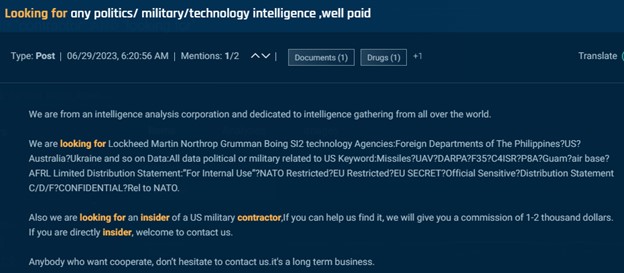
Different posts search people who can present categorized data. For instance, this subsequent submit appeared a number of instances throughout a number of boards and Telegram from a self-described “intelligence evaluation company” providing $1,000-$2,000 as a finders charge for somebody that may join them with an insider at a US army contractor.
Cybersixgill
Lastly, we additionally found the beneath submit through which a person presupposed to promote sixteen units of categorized authorities knowledge, together with proprietary knowledge belonging to protection producers equivalent to Raytheon and Elbit. The submit additionally lists a secret doc a few confidential 5 Eyes army train for $300, noting that it was obtained by an insider.

Cybersixgill
We should emphasize that posts soliciting insiders to offer categorized data are uncommon. The penalties for such actions are extreme, and many of the darkish internet’s customers are financially motivated. Even so, it’s not extraordinary for an insider to leak categorized data on the deep and darkish internet; most lately, a Massachusetts Nationwide Guardsman has been charged with posting classified documents on a Discord server.
Defending Towards Insider Threats
Workers can pose a singular sort of risk to a corporation. Most staff aren’t malicious, and so they should be trusted with entry to the information and programs wanted for performing their duties. Nevertheless, those that are lured by a wide range of strategies to make use of their positions to help in prison enterprises could cause vital monetary and reputational injury to their employers.
In line with the 2023 Verizon Information Breach Investigations Report, malicious insiders perpetrate about 19% of recognized knowledge breaches. Whereas there isn’t any approach of figuring out for positive what number of of those assaults originated from a partnership solid on the deep and darkish internet, there are a number of practices that firms can take to guard themselves.
- Principal of least privilege: Worker privileges must be restricted solely to what their duties require.
- Job rotation: Common biking of staff between duties to disclose fraudulent exercise.
- A number of signoff: Execution of delicate actions ought to require a number of staff to approve.
- VIP account safety: Prospects with delicate accounts or who usually tend to be focused ought to have the ability to opt-in to extra stringent account safety.
- Worker consciousness: Workers ought to perceive that risk actors search to recruit their friends and perpetrate fraud. In the event that they see one thing suspicious, they need to report it.
- Automated detection: Use of software program to flag suspicious actions.
- Underground monitoring: Organizations should perceive adversarial efforts to recruit insiders. Actual-time cyber risk intelligence from the clear, deep, and darkish internet is crucial to collect the knowledge wanted to reveal organizational threat from insider threats.
A rogue worker can severely influence a enterprise’s operations, funds, community safety, and model. They’re way over simply an “IT drawback” or perhaps a “safety crew drawback.” A correct organizational protection requires coordination between technical and non-technical gamers, from the SOC to HR, as a way to hold the corporate safe.
Organizations should determine which of their staff are in roles that could be focused for recruitment by cybercriminals, and implement stringent monitoring and controls to neutralize any threats from contained in the constructing.















