Various cybercriminal improvements are making it simpler for scammers to money in in your upcoming journey plans. This story examines a latest spear-phishing marketing campaign that ensued when a California lodge had its reserving.com credentials stolen. We’ll additionally discover an array of cybercrime companies aimed toward phishers who goal inns that depend on the world’s most visited journey web site.
In line with the market share web site statista.com, reserving.com is by far the Web’s busiest journey service, with almost 550 million visits in September. KrebsOnSecurity final week heard from a reader whose shut good friend obtained a focused phishing message throughout the Reserving cellular app simply minutes after making a reservation at a California.
The missive bore the title of the lodge and referenced particulars from their reservation, claiming that reserving.com’s anti-fraud system required further details about the client earlier than the reservation might be finalized.

The phishing message our reader’s good friend obtained after making a reservation at reserving.com in late October.
In an e mail to KrebsOnSecurity, reserving.com confirmed considered one of its companions had suffered a safety incident that allowed unauthorized entry to buyer reserving data.
“Our safety groups are at present investigating the incident you talked about and may affirm that it was certainly a phishing assault concentrating on considered one of our lodging companions, which sadly is just not a brand new state of affairs and fairly widespread throughout industries,” reserving.com replied. “Importantly, we need to make clear that there was no compromise of Reserving.com’s inside techniques.”
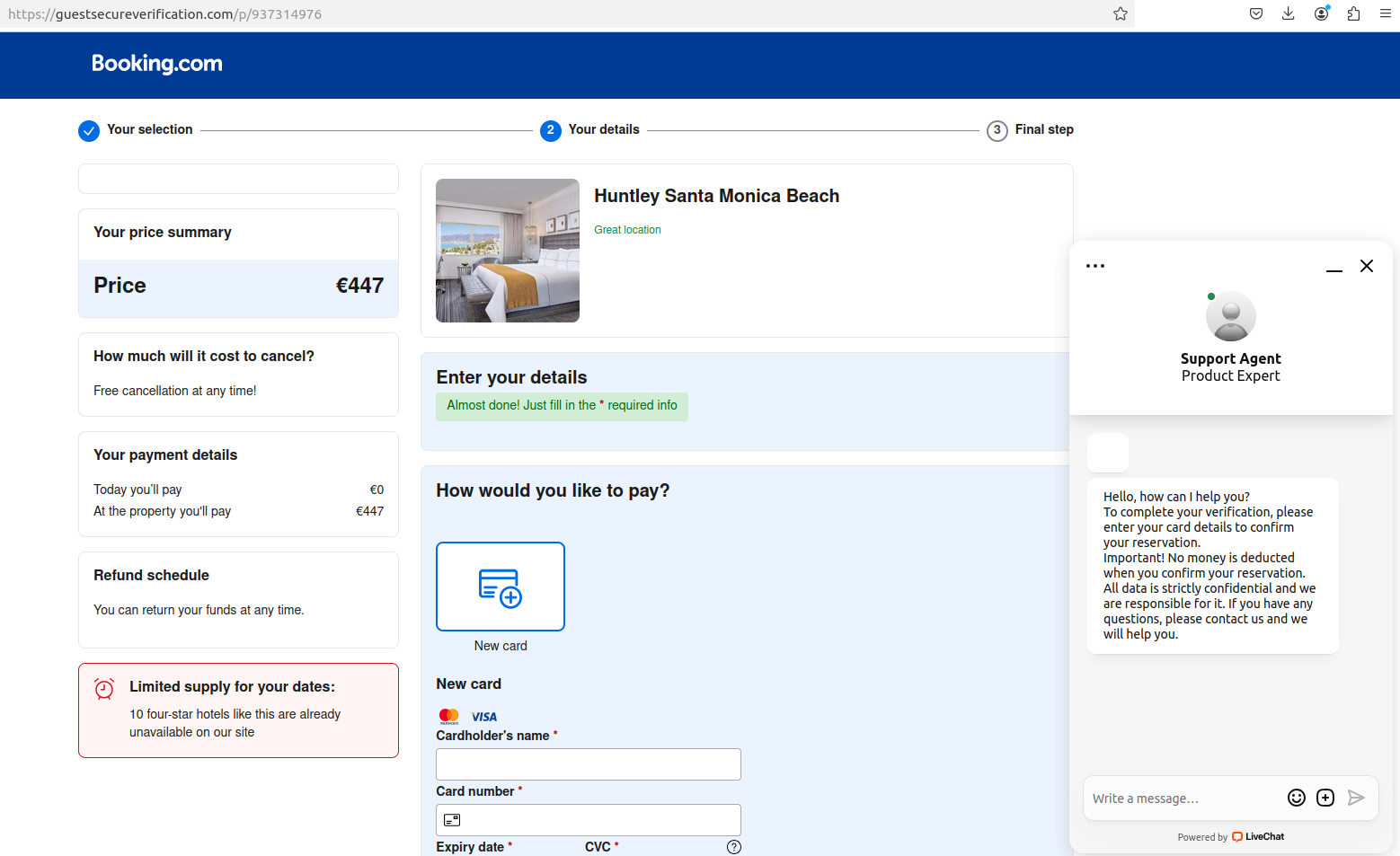
The phony reserving.com web site generated by visiting the hyperlink within the textual content message.
Reserving.com mentioned it now requires 2FA, which forces companions to supply a one-time passcode from a cellular authentication app (Pulse) along with a username and password.
“2FA is required and enforced, together with for companions to entry fee particulars from prospects securely,” a reserving.com spokesperson wrote. “That’s why the cybercriminals follow-up with messages to attempt to get prospects to make funds exterior of our platform.”
“That mentioned, the phishing assaults stem from companions’ machines being compromised with malware, which has enabled them to additionally achieve entry to the companions’ accounts and to ship the messages that your reader has flagged,” they continued.
It’s unclear, nevertheless, if the corporate’s 2FA requirement is enforced for all or simply newer companions. Reserving.com didn’t reply to questions on that, and its present account security advice urges prospects to allow 2FA.
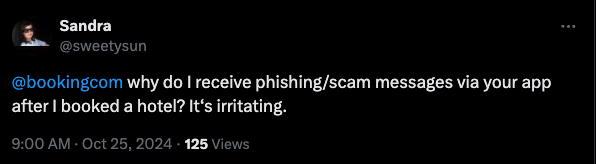
A scan of social media networks confirmed this isn’t an unusual rip-off.
In November 2023, the safety agency SecureWorks detailed how scammers focused reserving.com hospitality companions with data-stealing malware. SecureWorks mentioned these assaults had been happening since at the very least March 2023.
“The lodge didn’t allow multi-factor authentication (MFA) on its Reserving.com entry, so logging into the account with the stolen credentials was straightforward,” SecureWorks mentioned of the reserving.com associate it investigated.
In June 2024, reserving.com told the BBC that phishing assaults concentrating on vacationers had elevated 900 p.c, and that thieves benefiting from new synthetic intelligence (AI) instruments had been the first driver of this development.
Reserving.com advised the BCC the corporate had began utilizing AI to battle AI-based phishing assaults. Reserving.com’s assertion mentioned their investments in that area “blocked 85 million fraudulent reservations over greater than 1.5 million phishing makes an attempt in 2023.”
The area title within the phony reserving.com web site despatched to our reader’s good friend — guestssecureverification[.]com — was registered to the e-mail handle [email protected]. In line with DomainTools.com, this e mail handle was used to register greater than 700 different phishing domains prior to now month alone.
Most of the 700+ domains seem to focus on hospitality firms, together with platforms like reserving.com and Airbnb. Others appear crafted to phish customers of Shopify, Steam, and a wide range of monetary platforms. A full, defanged checklist of domains is accessible here.
A cursory assessment of latest posts throughout dozens of cybercrime boards monitored by the safety agency Intel 471 reveals there’s a nice demand for compromised reserving.com accounts belonging to inns and different companions.
One submit final month on the Russian-language hacking discussion board BHF supplied as much as $5,000 for every lodge account. This vendor claims to assist individuals monetize hacked reserving.com companions, apparently by utilizing the stolen credentials to arrange fraudulent listings.
A service marketed on the English-language crime group BreachForums in October courts phishers who could need assistance with sure facets of their phishing campaigns concentrating on reserving.com companions. These embody greater than two million lodge e mail addresses, and companies designed to assist phishers arrange massive volumes of phished information. Clients can work together with the service by way of an automatic Telegram bot.
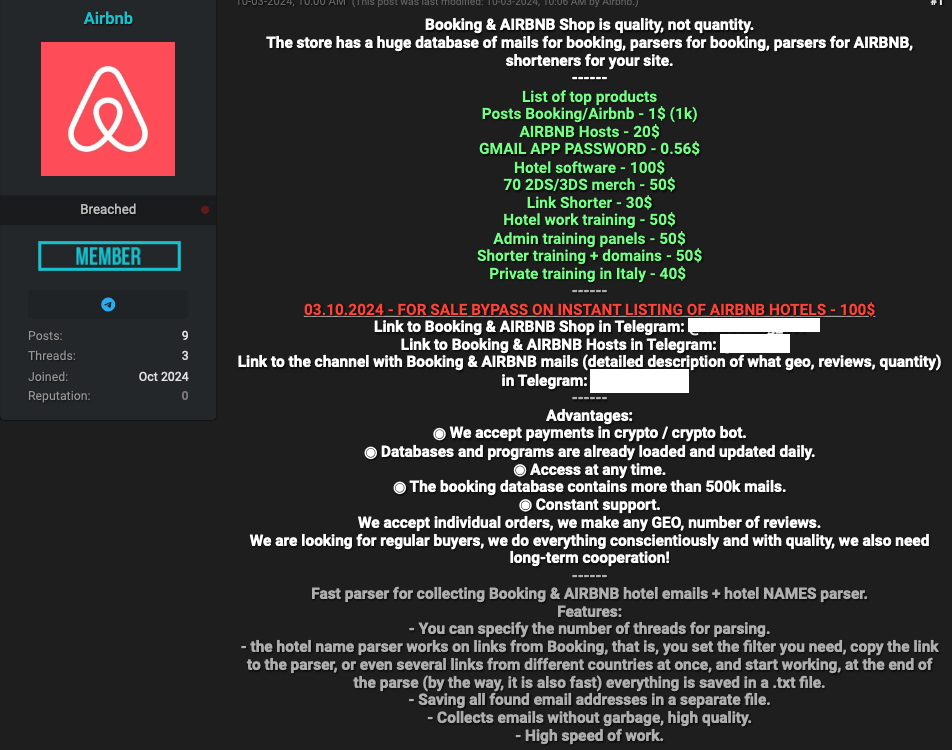
Some cybercriminals seem to have used compromised reserving.com accounts to energy their very own journey businesses catering to fellow scammers, with as much as 50 p.c reductions on lodge reservations by way of reserving.com. Others are promoting ready-to-use “config” recordsdata designed to make it easy to conduct automated login makes an attempt towards reserving.com administrator accounts.
SecureWorks discovered the phishers concentrating on reserving.com associate inns used malware to steal credentials. However at present’s thieves can simply as simply simply go to crime bazaars on-line and buy stolen credentials to cloud companies that don’t implement 2FA for all accounts.
That’s exactly what transpired over the previous 12 months with many purchasers of the cloud knowledge storage large Snowflake. In late 2023, cybercriminals discovered that whereas tons of firms had stashed monumental quantities of buyer knowledge at Snowflake, a lot of these buyer accounts weren’t protected by 2FA.
Snowflake responded by making 2FA obligatory for all new prospects. However that change got here solely after thieves used stolen credentials to siphon knowledge from 160 firms — together with AT&T, Lending Tree and TicketMaster.















