KrebsOnSecurity final week was hit by a close to report distributed denial-of-service (DDoS) assault that clocked in at greater than 6.3 terabits of knowledge per second (a terabit is one trillion bits of knowledge). The transient assault seems to have been a take a look at run for a large new Web of Issues (IoT) botnet able to launching crippling digital assaults that few internet locations can face up to. Learn on for extra in regards to the botnet, the assault, and the obvious creator of this world menace.

For reference, the 6.3 Tbps assault final week was ten instances the scale of the assault launched in opposition to this website in 2016 by the Mirai IoT botnet, which held KrebsOnSecurity offline for nearly four days. The 2016 assault was so giant that Akamai – which was offering pro-bono DDoS safety for KrebsOnSecurity on the time — requested me to depart their service as a result of the assault was inflicting issues for his or her paying clients.
Because the Mirai assault, KrebsOnSecurity.com has been behind the safety of Mission Protect, a free DDoS protection service that Google offers to web sites providing information, human rights, and election-related content material. Google Safety Engineer Damian Menscher advised KrebsOnSecurity the Could 12 assault was the most important Google has ever dealt with. By way of sheer dimension, it’s second solely to a really comparable assault that Cloudflare mitigated and wrote about in April.
After evaluating notes with Cloudflare, Menscher stated the botnet that launched each assaults bears the fingerprints of Aisuru, a digital siege machine that first surfaced lower than a 12 months in the past. Menscher stated the assault on KrebsOnSecurity lasted lower than a minute, hurling large UDP data packets at random ports at a fee of roughly 585 million information packets per second.
“It was the kind of assault usually designed to overwhelm community hyperlinks,” Menscher stated, referring to the throughput connections between and amongst numerous Web service suppliers (ISPs). “For many firms, this dimension of assault would kill them.”
The Aisuru botnet includes a globally-dispersed assortment of hacked IoT gadgets, together with routers, digital video recorders and different techniques which can be commandeered through default passwords or software program vulnerabilities. As documented by researchers at QiAnXin XLab, the botnet was first recognized in an August 2024 assault on a big gaming platform.
Aisuru reportedly went quiet after that publicity, solely to reappear in November with much more firepower and software program exploits. In a January 2025 report, XLab discovered the brand new and improved Aisuru (a.ok.a. “Airashi“) had included a beforehand unknown zero-day vulnerability in Cambium Networks cnPilot routers.
NOT FORKING AROUND
The folks behind the Aisuru botnet have been peddling entry to their DDoS machine in public Telegram chat channels which can be intently monitored by a number of safety companies. In August 2024, the botnet was rented out in subscription tiers starting from $150 per day to $600 per week, providing assaults of as much as two terabits per second.
“You might not assault any measurement partitions, healthcare services, faculties or authorities websites,” learn a discover posted on Telegram by the Aisuru botnet homeowners in August 2024.
events had been advised to contact the Telegram deal with “@yfork” to buy a subscription. The account @yfork beforehand used the nickname “Forky,” an id that has been posting to public DDoS-focused Telegram channels since 2021.
In keeping with the FBI, Forky’s DDoS-for-hire domains have been seized in a number of legislation enforcement operations over time. Final 12 months, Forky stated on Telegram he was promoting the area stresser[.]finest, which noticed its servers seized by the FBI in 2022 as a part of an ongoing worldwide legislation enforcement effort geared toward diminishing the provision of and demand for DDoS-for-hire providers.
“The operator of this service, who calls himself ‘Forky,’ operates a Telegram channel to promote options and talk with present and potential DDoS clients,” reads an FBI seizure warrant (PDF) issued for stresser[.]finest. The FBI warrant said that on the identical day the seizures had been introduced, Forky posted a link to a story on this blog that detailed the area seizure operation, including the remark, “We’re shopping for our new domains proper now.”
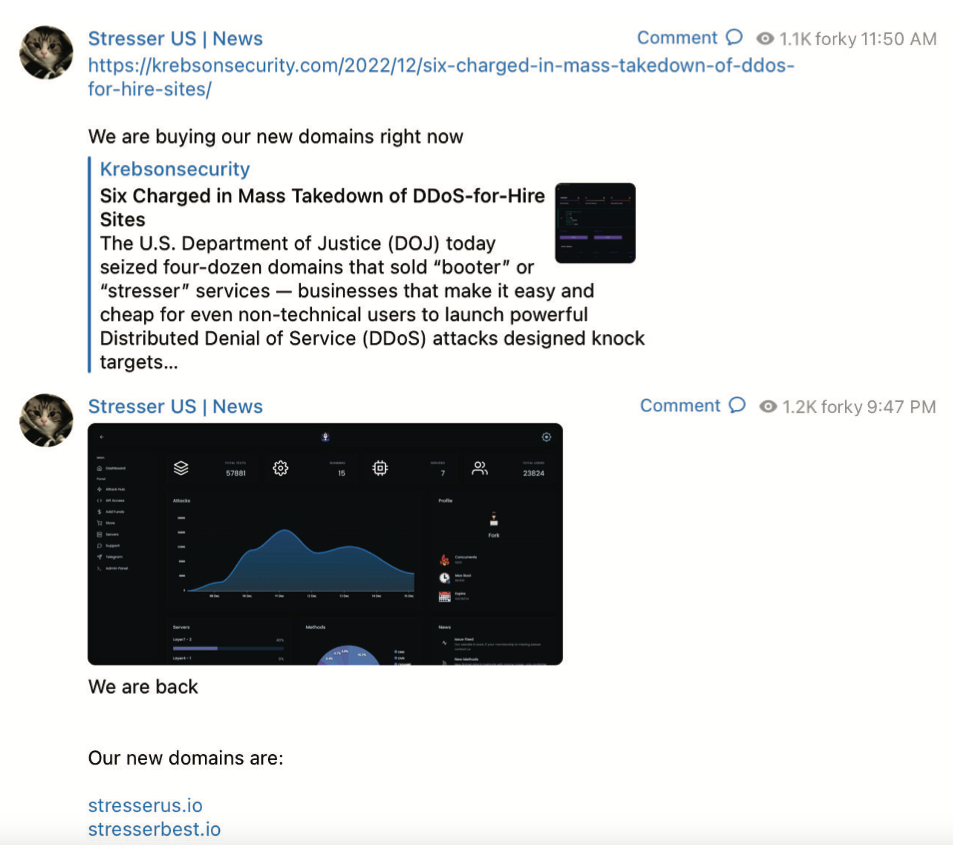
A screenshot from the FBI’s seizure warrant for Forky’s DDoS-for-hire domains reveals Forky saying the resurrection of their service at new domains.
Roughly ten hours later, Forky posted once more, together with a screenshot of the stresser[.]finest consumer dashboard, instructing clients to make use of their saved passwords for the previous web site on the brand new one.
A overview of Forky’s posts to public Telegram channels — as listed by the cyber intelligence companies Unit 221B and Flashpoint — reveals a 21-year-old particular person who claims to reside in Brazil [full disclosure: Flashpoint is currently an advertiser on this blog].
Since late 2022, Forky’s posts have regularly promoted a DDoS mitigation firm and ISP that he operates known as botshield[.]io. The Botshield web site is linked to a enterprise entity registered in the UK known as Botshield LTD, which lists a 21-year-old girl from Sao Paulo, Brazil because the director. Web routing information point out Botshield (AS213613) presently controls a number of hundred Web addresses that had been allotted to the corporate earlier this 12 months.
Domaintools.com stories that botshield[.]io was registered in July 2022 to a Kaike Southier Leite in Sao Paulo. A LinkedIn profile by the identical title says this particular person is a community specialist from Brazil who works in “the planning and implementation of sturdy community infrastructures, with a deal with safety, DDoS mitigation, colocation and cloud server providers.”
MEET FORKY

Picture: Jaclyn Vernace / Shutterstock.com.
In his posts to public Telegram chat channels, Forky has hardly tried to hide his whereabouts or id. In numerous chat conversations listed by Unit 221B, Forky might be seen speaking about on a regular basis life in Brazil, typically remarking on the extraordinarily low or excessive costs in Brazil for a spread of products, from laptop and networking gear to narcotics and meals.
Reached through Telegram, Forky claimed he was “not concerned in one of these unlawful actions for years now,” and that the undertaking had been taken over by different unspecified builders. Forky initially advised KrebsOnSecurity he had been out of the botnet scene for years, solely to concede this wasn’t true when offered with public posts on Telegram from late final 12 months that clearly confirmed in any other case.
Forky denied being concerned within the assault on KrebsOnSecurity, however acknowledged that he helped to develop and market the Aisuru botnet. Forky claims he’s now merely a employees member for the Aisuru botnet staff, and that he stopped working the botnet roughly two months in the past after beginning a household. Forky additionally stated the girl named as director of Botshield is expounded to him.
Forky supplied equivocal, evasive responses to a variety of questions in regards to the Aisuru botnet and his enterprise endeavors. However on one level he was crystal clear:
“I’ve zero worry about you, the FBI, or Interpol,” Forky stated, asserting that he’s now virtually solely targeted on their internet hosting enterprise — Botshield.
Forky declined to debate the make-up of his ISP’s clientele, or to make clear whether or not Botshield was extra of a internet hosting supplier or a DDoS mitigation agency. Nevertheless, Forky has posted on Telegram about Botshield efficiently mitigating giant DDoS assaults launched in opposition to different DDoS-for-hire providers.
DomainTools finds the identical Sao Paulo road deal with within the registration information for botshield[.]io was used to register a number of different domains, together with cant-mitigate[.]us. The e-mail deal with within the WHOIS information for that area is [email protected], which DomainTools says was used to register the area for the now-defunct DDoS-for-hire service stresser[.]us, one of many domains seized in the FBI’s 2023 crackdown.
On Could 8, 2023, the U.S. Division of Justice announced the seizure of stresser[.]us, together with a dozen different domains providing DDoS providers. The DOJ stated ten of the 13 domains had been reincarnations of providers that had been seized throughout a prior sweep in December, which focused 48 prime stresser providers (also called “booters”).
Forky claimed he may discover out who attacked my website with Aisuru. However when pressed a day in a while the query, Forky stated he’d come up empty-handed.
“I attempted to ask round, all the large guys aren’t retarded sufficient to assault you,” Forky defined in an interview on Telegram. “I didn’t have something to do with it. However you’re welcome to jot down the story and attempt to put the blame on me.”
THE GHOST OF MIRAI
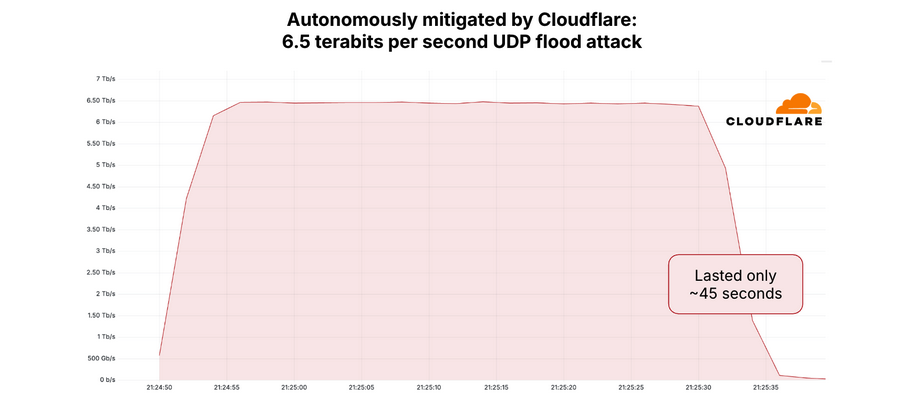
The 6.3 Tbps assault final week triggered no seen disruption to this website, partially as a result of it was so transient — lasting roughly 45 seconds. DDoS assaults of such magnitude and brevity usually are produced when botnet operators want to take a look at or reveal their firepower for the good thing about potential patrons. Certainly, Google’s Menscher stated it’s doubtless that each the Could 12 assault and the marginally bigger 6.5 Tbps assault in opposition to Cloudflare final month had been merely exams of the identical botnet’s capabilities.
In some ways, the risk posed by the Aisuru/Airashi botnet is paying homage to Mirai, an revolutionary IoT malware pressure that emerged in the summertime of 2016 and efficiently out-competed nearly all different IoT malware strains in existence on the time.
As first revealed by KrebsOnSecurity in January 2017, the Mirai authors had been two U.S. men who co-ran a DDoS mitigation service — at the same time as they had been promoting way more profitable DDoS-for-hire providers utilizing probably the most highly effective botnet on the planet.
Lower than every week after the Mirai botnet was utilized in a days-long DDoS in opposition to KrebsOnSecurity, the Mirai authors published the source code to their botnet in order that they might not be the one ones in possession of it within the occasion of their arrest by federal investigators.
Paradoxically, the leaking of the Mirai supply is exactly what led to the eventual unmasking and arrest of the Mirai authors, who went on to serve probation sentences that required them to consult with FBI investigators on DDoS investigations. However that leak additionally quickly led to the creation of dozens of Mirai botnet clones, lots of which had been harnessed to gasoline their very own highly effective DDoS-for-hire providers.
Menscher advised KrebsOnSecurity that as counterintuitive as it could sound, the Web as an entire would in all probability be higher off if the supply code for Aisuru turned public information. In any case, he stated, the folks behind Aisuru are in fixed competitors with different IoT botnet operators who’re all striving to commandeer a finite variety of weak IoT gadgets globally.
Such a growth would virtually actually trigger a proliferation of Aisuru botnet clones, he stated, however not less than then the general firepower from every particular person botnet could be enormously diminished — or not less than inside vary of the mitigation capabilities of most DDoS safety suppliers.
Barring a supply code leak, Menscher stated, it could be good if somebody revealed the complete listing of software program exploits being utilized by the Aisuru operators to develop their botnet so rapidly.
“A part of the rationale Mirai was so harmful was that it successfully took out competing botnets,” he stated. “This assault by some means managed to compromise all these bins that no person else is aware of about. Ideally, we’d wish to see that fragmented out, in order that no [individual botnet operator] controls an excessive amount of.”









![[Travel Insurance] Does it Cowl Pure Disasters Like Typhoons and Earthquakes? What’s the Distinction Between Shopping for Earlier than or After Departure?](http://marketibiza.com/wp-content/uploads/2025/05/travel-insurance-disaster-820x453.webp-120x86.webp)


