Google says it has suspended the app for the Chinese language e-commerce big Pinduoduo after malware was present in variations of the software program. The transfer comes simply weeks after Chinese language safety researchers revealed an evaluation suggesting the favored e-commerce app sought to grab complete management over affected units by exploiting a number of safety vulnerabilities in a wide range of Android-based smartphones.
In November 2022, researchers at Google’s Project Zero warned about energetic assaults on Samsung cellphones which chained collectively three safety vulnerabilities that Samsung patched in March 2021, and which might have allowed an app so as to add or learn any recordsdata on the system.
Google mentioned it believes the exploit chain for Samsung units belonged to a “business surveillance vendor,” with out elaborating additional. The highly technical writeup additionally didn’t identify the malicious app in query.
On Feb. 28, 2023, researchers on the Chinese language safety agency DarkNavy revealed a blog post purporting to indicate proof {that a} main Chinese language ecommerce firm’s app was utilizing this identical three-exploit chain to learn person knowledge saved by different apps on the affected system, and to make its app almost not possible to take away.
DarkNavy likewise didn’t identify the app they mentioned was liable for the assaults. In truth, the researchers took care to redact the identify of the app from a number of code screenshots revealed of their writeup. DarkNavy didn’t reply to requests for clarification.
“At current, a lot of finish customers have complained on a number of social platforms,” reads a translated model of the DarkNavy weblog put up. “The app has issues akin to inexplicable set up, privateness leakage, and lack of ability to uninstall.”
Replace, March 27, 1:24 p.m. ET: Dan Goodin over at Ars Technica has an important update on this story that signifies the Pinduoduo code was exploiting a zero-day vulnerability in Android — not Samsung. From that piece:
“A preliminary evaluation by Lookout discovered that no less than two off-Play variations of Pinduoduo for Android exploited CVE-2023-20963, the monitoring quantity for an Android vulnerability Google patched in updates that turned out there to finish customers two weeks ago. This privilege-escalation flaw, which was exploited previous to Google’s disclosure, allowed the app to carry out operations with elevated privileges. The app used these privileges to obtain code from a developer-designated web site and run it inside a privileged atmosphere.
“The malicious apps characterize “a really refined assault for an app-based malware,” Christoph Hebeisen, certainly one of three Lookout researchers who analyzed the file, wrote in an e mail. “Lately, exploits haven’t often been seen within the context of mass-distributed apps. Given the extraordinarily intrusive nature of such refined app-based malware, this is a crucial risk cell customers want to guard towards.”
On March 3, 2023, a denizen of the now-defunct cybercrime community BreachForums posted a thread which famous {that a} distinctive part of the malicious app code highlighted by DarkNavy additionally was discovered within the ecommerce utility whose identify was apparently redacted from the DarkNavy evaluation: Pinduoduo.
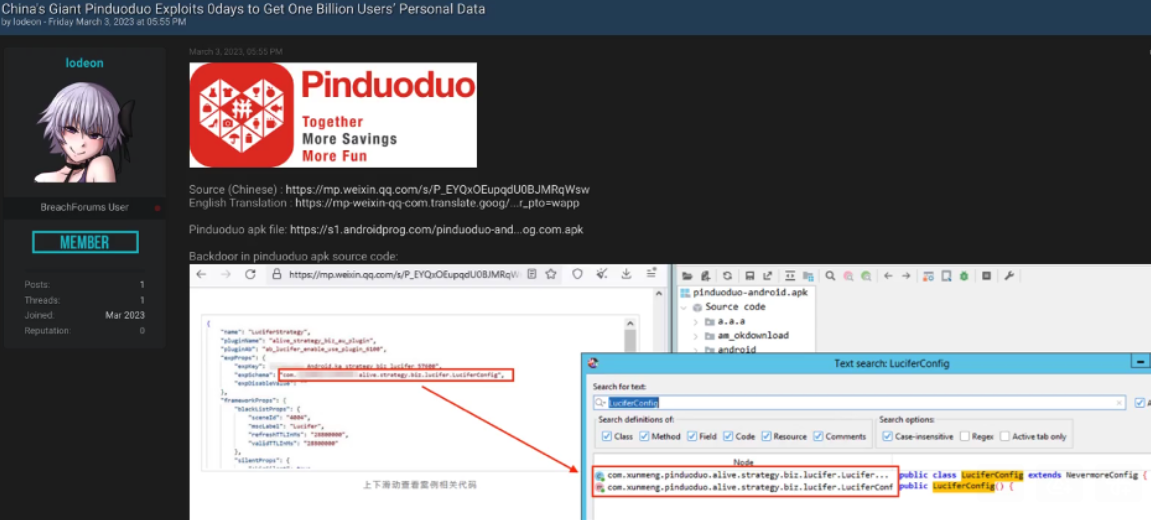
A Mar. 3, 2023 put up on BreachForums, evaluating the redacted code from the DarkNavy evaluation with the identical operate within the Pinduoduo app out there for obtain on the time.
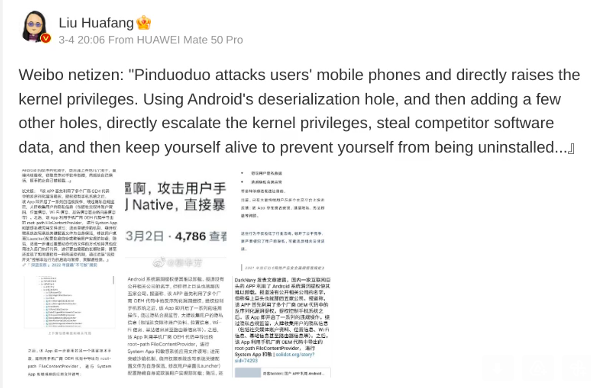
On March 4, 2023, e-commerce knowledgeable Liu Huafang posted on the Chinese language social media community Weibo that Pinduoduo’s app was utilizing safety vulnerabilities to achieve market share by stealing person knowledge from its opponents. That Weibo put up has since been deleted.
On March 7, the newly created Github account Davinci1010 revealed a technical analysis claiming that till just lately Pinduoduo’s supply code included a “backdoor,” a hacking time period used to explain code that permits an adversary to remotely and secretly hook up with a compromised system at will.
That evaluation contains links to archived versions of Pinduoduo’s app launched earlier than March 5 (model 6.50 and decrease), which is when Davinci1010 says a brand new model of the app eliminated the malicious code.
Pinduoduo has not but responded to requests for remark. Pinduoduo mum or dad firm PDD Holdings informed Reuters Google has not shared particulars about why it suspended the app.
The corporate told CNN that it strongly rejects “the hypothesis and accusation that Pinduoduo app is malicious simply from a generic and non-conclusive response from Google,” and mentioned there have been “a number of apps which have been suspended from Google Play on the identical time.”
Pinduoduo is amongst China’s hottest e-commerce platforms, boasting roughly 900 million month-to-month energetic customers.
A lot of the information protection of Google’s transfer towards Pinduoduo emphasizes that the malware was present in variations of the Pinduoduo app out there outdoors of Google’s app retailer — Google Play.
“Off-Play variations of this app which have been discovered to comprise malware have been enforced on by way of Google Play Defend,” a Google spokesperson mentioned in an announcement to Reuters, including that the Play model of the app has been suspended for safety issues.
Nevertheless, Google Play will not be out there to shoppers in China. Because of this, the app will nonetheless be out there by way of different cell app shops catering to the Chinese language market — together with these operated by Huawei, Oppo, Tencent and VIVO.
Google mentioned its ban didn’t have an effect on the PDD Holdings app Temu, which is a web based purchasing platform in america. In accordance with The Washington Post, 4 of the Apple App Retailer’s 10 most-downloaded free apps are owned by Chinese language corporations, together with Temu and the social media community TikTok.
The Pinduoduo suspension comes as lawmakers in Congress this week are gearing as much as grill the CEO of TikTok over nationwide safety issues. TikTok, which is owned by Beijing-based ByteDance, mentioned final month that it now has roughly 150 million month-to-month energetic customers in america.
A new cybersecurity strategy launched earlier this month by the Biden administration singled out China as the best cyber risk to the U.S. and Western pursuits. The technique says China now presents the “broadest, most energetic, and most persistent risk to each authorities and personal sector networks,” and says China is “the one nation with each the intent to reshape the worldwide order and, more and more, the financial, diplomatic, navy, and technological energy to take action.”











![[2025 Japan Public Holidays] Do you have to keep away from the Golden Week when touring to Japan? Record of Japanese nationwide holidays and lengthy holidays | Peak and off-seasons for touring in Japan](http://marketibiza.com/wp-content/uploads/2025/05/Japan-Public-Holidays-2025-820x453.webp-120x86.webp)



