If you happen to function a cybercrime enterprise that depends on disseminating malicious software program, you in all probability additionally spend a great deal of time making an attempt to disguise or “crypt” your malware in order that it seems benign to antivirus and safety merchandise. In reality, the method of “crypting” malware is sufficiently advanced and time-consuming that almost all critical cybercrooks will outsource this vital operate to a handful of trusted third events. This story explores the historical past and identification behind Cryptor[.]biz, a long-running crypting service that’s trusted by among the greatest names in cybercrime.
Just about all malware that’s deployed to be used in information stealing in some unspecified time in the future must be crypted. This extremely technical, laborious course of entails iteratively altering the looks and habits of a malicious file till it not units off alarm bells when scanned by totally different antivirus instruments.
Skilled malware purveyors perceive that in the event that they’re not constantly crypting their malware earlier than sending it out, then much more of no matter digital illness they’re making an attempt to unfold goes to get flagged by safety instruments. In brief, if you’re operating a cybercrime enterprise and also you’re not geared up to deal with this crypting course of your self, you in all probability have to pay another person to do it for you.
Due to the excessive demand for dependable crypting providers, there are numerous cybercriminals who’ve frolicked their shingles as crypting service suppliers. Nevertheless, most of those folks don’t look like superb at what they do, as a result of most are quickly out of enterprise.
One standout is Cryptor[.]biz. This service is definitely beneficial by the purveyors of the RedLine information stealer malware, which is a well-liked and highly effective malware equipment that focuses on stealing sufferer information and is commonly used to put the groundwork for ransomware assaults. Cryptor[.]biz additionally has been beneficial to prospects of the Vidar information stealer malware family (by way of the malware’s Telegram assist channels).
WHO RUNS CRYPTOR[.]BIZ?
Pretty much as good as Cryptor[.]biz could also be at obfuscating malware, its proprietor doesn’t seem to have performed an incredible job masking his personal tracks. The registration information for the web site Cryptor[.]biz are hidden behind privateness safety providers, however the web site’s homepage says potential prospects ought to register by visiting the area crypt[.]guru, or by sending a Jabber prompt message to the handle “[email protected].”
Crypt[.]guru’s registration information are also hidden, but passive domain name system (DNS) records for each cryptor[.]biz and crypt[.]guru present that in 2018 the domains had been forwarding incoming e-mail to the handle [email protected].
Cyber intelligence agency Intel 471 stories that [email protected] was used to register an account on the discussion board Blacksoftware underneath the nickname “Kerens.” In the meantime, the Jabber handle [email protected] has been related to the person Kerens on the Russian hacking discussion board Exploit from 2011 to the current day.
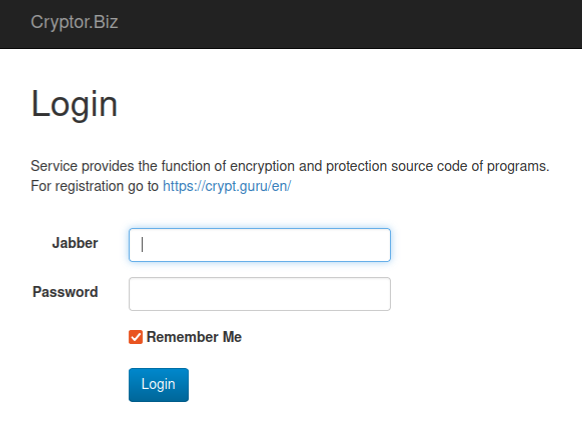
The login web page for Cryptor dot biz accommodates a number of clues about who runs the service.
The very first publish by Kerens on Exploit in 2011 was a adverse overview of a well-liked crypting service that predated Cryptor[.]biz known as VIP Crypt, which Kerens accused of being “shitty” and unreliable. However Intel 471 finds that after his vital overview of VIP Crypt, Kerens didn’t publish publicly on Exploit once more for an additional 4 years till October 2016, once they immediately started promoting Cryptor[.]biz.
Intel 471 discovered that Kerens used the e-mail handle [email protected], which additionally was used to register Kerens accounts on the Russian language hacking boards Verified and Damagelab.
Sarcastically, Verified has itself been hacked a number of instances over time, with its personal messages and person registration particulars leaked on-line. These information point out the person Kerens registered on Verified in March 2009 from an Web handle in Novosibirsk, a metropolis within the southern Siberian area of Russia.
In 2010, somebody with the username Pepyak on the Russian language affiliate discussion board GoFuckBiz[.]com shared that they usually cut up their time throughout the 12 months between dwelling in Siberia (throughout the milder months) and Thailand (when Novosibirsk is usually -15 °C/°5F).
For instance, in a single dialog about one of the best automobile to purchase for navigating shoddy roads, Pepyak declared, “We now have shitty roads in Siberia.” In January 2010, Pepyak requested the GoFuckBiz group the place one may discover a good USB-based modem in Phuket, Thailand.
DomainTools.com says the e-mail handle [email protected] was used to register 28 domains over time, together with a now-defunct Russian car gross sales web site known as “autodoska[.]biz.” DomainTools reveals this web site was registered in 2008 to a Yuri Churnov from Sevastpol, Crimea (previous to Russia’s annexation of Crimea in 2014, the peninsula was a part of Ukraine).
The WHOIS information for autodoska[.]biz had been modified in 2010 to Sergey Purtov ([email protected]) from Yurga, a city in Russia’s Kemerovo Oblast, which is a comparatively populous space in Western Siberia that’s adjoining to Novosibirsk.
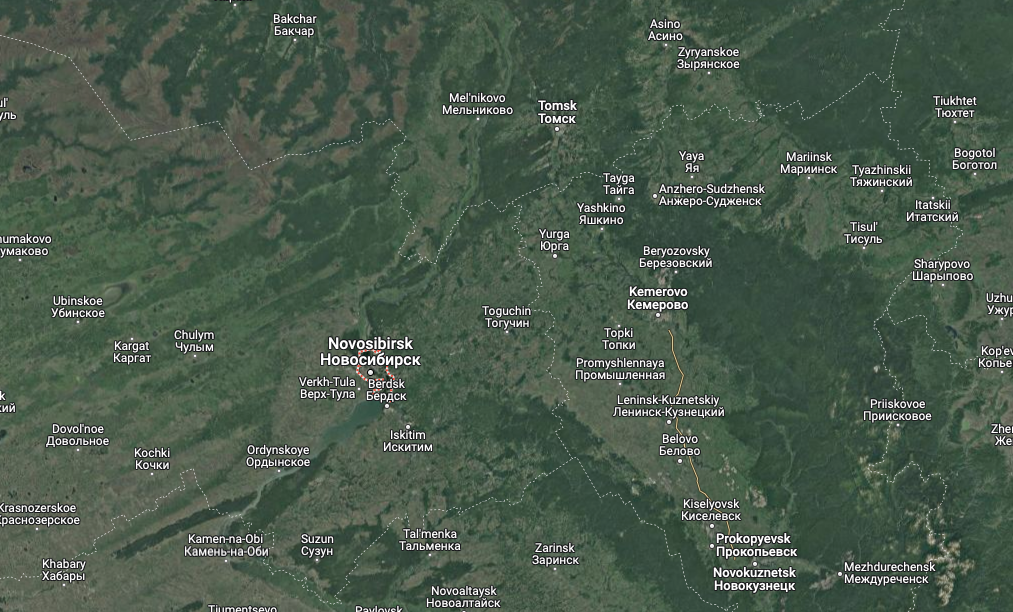
A satellite tv for pc view of the area together with Novosibirsk, Yurga and Kemerovo Oblast. Picture: Google Maps.
Most of the 28 domains registered to [email protected] have one other e-mail handle of their registration information: [email protected]. In response to DomainTools, the Unforgiven e-mail handle was used to register roughly a dozen domains, together with three that had been initially registered to Keren’s e-mail handle — [email protected] (e.g., antivirusxp09[.]com).
One of many domains registered in 2006 to the handle [email protected] was thelib[.]ru, which for a few years was a spot to obtain pirated e-books. DomainTools says thelib[.]ru was initially registered to a Sergey U Purtov.
Many of the two-dozen domains registered to [email protected] shared a server at one level with a small variety of different domains, together with mobile-soft[.]su, which was registered to the e-mail handle [email protected].
CDEK, an categorical supply firm primarily based in Novosibirsk, was apparently hacked in some unspecified time in the future as a result of cyber intelligence agency Constella Intelligence discovered that its database reveals the e-mail handle [email protected] was assigned to a Sergey Yurievich Purtov (Сергей Юрьевич Пуртов).
DomainTools says the identical telephone quantity within the registration information for autodoska[.]biz (+7.9235059268) was used to safe two different domains — bile[.]ru and thelibrary[.]ru, each of which had been registered to a Sergey Y Purtov.
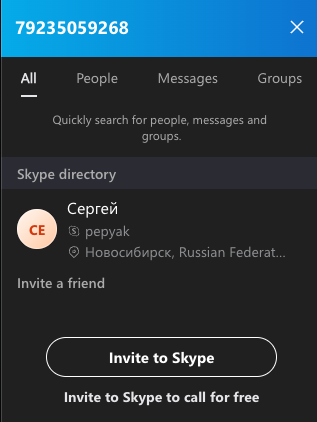 A search on the telephone quantity 79235059268 in Skype reveals these digits belong to a “Sergey” from Novosibirsk with the now-familiar username — Pepyak.
A search on the telephone quantity 79235059268 in Skype reveals these digits belong to a “Sergey” from Novosibirsk with the now-familiar username — Pepyak.
Bringing issues full circle, Constella Intelligence reveals that numerous on-line accounts tied to the e-mail handle [email protected] often relied on the considerably distinctive password, “plk139t51z.” Constella says that very same password was used for only a handful of different e-mail addresses, together with [email protected].
Hacked buyer information from CDEK present [email protected] was tied to a buyer named Sergey Yurievich Purtov. DomainTools discovered that nearly all the 15 domains registered to [email protected] (together with the aforementioned mobile-soft[.]su) had been at one level registered to [email protected].
Intel 471 stories that [email protected] was utilized in 2009 to register a person by the nickname “Kolumb” on the Russian hacking discussion board Antichat. From Kolumb’s posts on Antichat, it appears this person was largely interested by shopping for entry to compromised computer systems within Russia.
Then in December 2009, Kolumb stated they had been in determined want of a dependable crypting service or full-time cryptor.
“We want an individual who will crypt software program every single day, typically even a few instances a day,” Kolumb wrote on Antichat.
Mr. Purtov didn’t reply to requests for remark despatched to any of the e-mail addresses referenced on this report. Mail.ru responded that the e-mail handle [email protected] is not lively.
ANALYSIS
As KrebsOnSecurity opined on Mastodon earlier this week, it makes a number of sense for cybersecurity researchers and regulation enforcement alike to focus consideration on the highest gamers within the crypting area — for a number of causes. Most critically, the cybercriminals providing time-tested crypting providers additionally are typically among the many most skilled and related malicious coders on the planet.
Consider it this manner: By definition, a crypting service scans and examines all forms of malware earlier than these new nasties are first set unfastened within the wild. This truth alone ought to make these prison enterprises a main goal of cybersecurity corporations seeking to achieve extra well timed intelligence about new malware.
Additionally, a overview of numerous posts and personal messages from Pepyak and different crypting suppliers reveals {that a} profitable crypting service could have direct and frequent contact with among the world’s most superior malware authors.
In brief, infiltrating or disrupting a trusted crypting service may be a superb technique to decelerate and even sideline numerous cybercrime operations suddenly.
Additional studying on the crypting business:
This Service Helps Malware Authors Fix Flaws in Their Code
Antivirus is Dead: Long Live Antivirus!