The infamous MEDUSA ransomware group has struck once more, concentrating on two outstanding firms and demanding hefty ransoms for the discharge of encrypted information.
The victims of MEDUSA Cyber Assaults, recognized as Karam Chand Thapar & Bros. (Coal Gross sales) Ltd based mostly in India, and Windak Group, are the newest additions to the darkish internet portal of the MEDUSA ransomware group.
Each assaults had been listed on the menace actor’s dark web portal, the place it shares the newest victims on the darkish internet.
On this area, the MEDUSA ransomware group has shared many victims previously weeks. The addition of Karam Chand Thapar & Bros. and Windak as victims on the listing reveals the rising menace of the MEDUSA ransomware group.
MEDUSA Cyber Assaults Spree: Two New Victims Added!
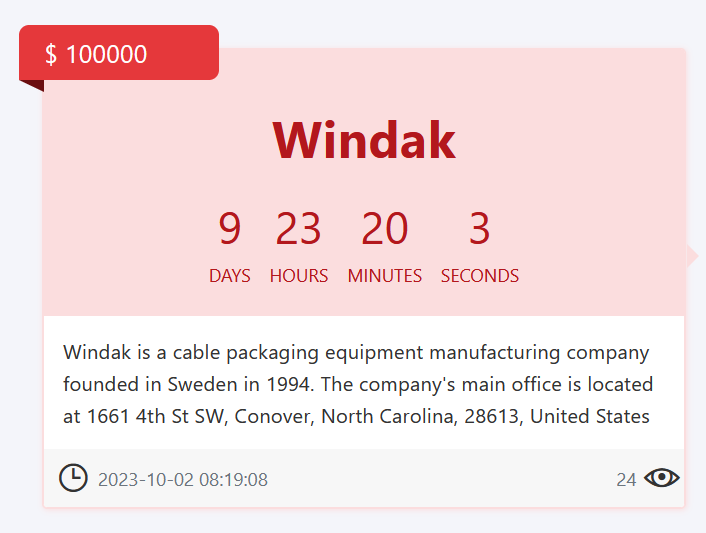
For Windak Group, a Sweden-based cable packaging tools producer based in 1994, the menace actors have set a ransom amount of $100,000.
The deadline for fee stands at 9 days, 23 hours, 20 minutes, and three seconds from the time of the cyber assault.
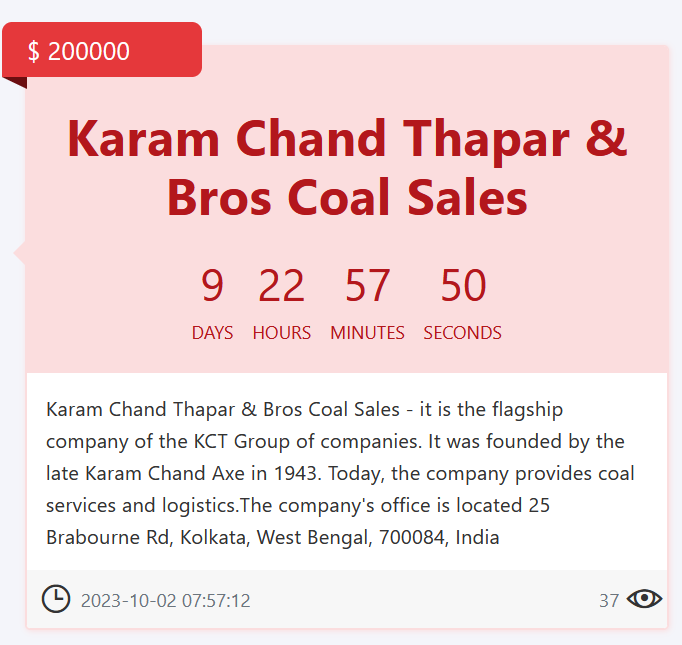
In the meantime, Karam Chand Thapar & Bros., the flagship firm of the KCT Group in India, has been focused with a ransom of $200,000.
The threat actors have given a deadline of 9 days, 22 hours, 57 minutes, and 50 seconds for the fee. Established in 1943 by the late Karam Chand Axe, the corporate makes a speciality of coal providers and logistics.
Efforts to confirm these claims have been initiated by The Cyber Express, which has reached out to each firms. On the time of writing, no official response has been acquired, leaving the MEDUSA cyber assault claims unverified.
Moreover, the sufferer web sites seem like operational, displaying no seen indicators of the cyber assault on their entrance finish, including a layer of uncertainty to the scenario.
Beforehand, TCE reported a similar pattern of MEDUSA cyber-attacks the place the menace actor used the identical methodology to announce their victims.
Within the earlier altercation, the MEDUSA ransomware group added two main entities to their dark web portal, Landstar Energy Ontario Inc. and Acoustic Heart.

Like this explicit assault, the earlier ones had been the identical as properly the place the menace actor makes use of its darkish internet platform to share the announcement concerning the alleged cyber assaults.
At this level, this methodology has turn into a go-to for the menace actor that retains repeating the identical techniques for its cyber attack claims.
MEDUSA Cyber Assaults, Emergence, and Modus Operandi
The MEDUSA ransomware group, recognized for its MedusaLocker Ransomware, emerged in September 2019 and primarily targets Home windows machines by way of SPAM campaigns.
This ransomware displays a singular conduct by booting up in protected mode earlier than encryption, using BAT recordsdata and PowerShell, relying on the variant. Notably, the newest variant alters the Bootmgr extension, leading to an error throughout boot-up.
Working underneath a ransomware-as-a-service (RaaS) enterprise mannequin, the Medusa ransomware predominantly focuses on healthcare, schooling, and enterprises dealing with substantial volumes of non-public info.
The group makes use of a double extortion tactic, pilfering sufferer information earlier than encryption and threatening its sale or public launch if the ransom just isn’t paid.
The ransomware predominantly exploits susceptible Distant Desktop Protocols (RDP) and employs misleading phishing campaigns for preliminary entry.
As soon as inside a system, Medusa ransomware group employs PowerShell for command execution, systematically erasing shadow copy backups to hinder information restoration.
Media Disclaimer: This report relies on inside and exterior analysis obtained by way of varied means. The knowledge offered is for reference functions solely, and customers bear full duty for his or her reliance on it. The Cyber Categorical assumes no legal responsibility for the accuracy or penalties of utilizing this info.
Associated
















