Digital Safety
A fast dive into the murky world of cyberespionage and different rising threats going through managed service suppliers – and their clients
02 Might 2023
•
,
4 min. learn

ESET telemetry from This autumn 2022 noticed the beginning of a brand new marketing campaign by MuddyWater, a cyberespionage group linked to Iran’s Ministry of Intelligence and Safety (MOIS) and energetic since a minimum of 2017. The group (primarily) targets victims within the Center East, Asia, Africa, Europe, and North America, specializing in telecommunications corporations, governmental organizations, and the oil & gasoline and power verticals.
For the MSP-interested reader, what stands out of their October 2022 marketing campaign is that 4 victims, three in Egypt and one in Saudi Arabia, have been compromised through the abuse of SimpleHelp, a reputable distant entry device (RAT) and distant assist software program utilized by MSPs. This improvement indicators the significance of visibility for MSPs. In deploying a whole bunch and even hundreds of software program varieties haven’t any alternative however to make use of automation and be sure that SOC groups, customer-facing safety admins, and detection and response processes are mature and consistently enhancing.
Good instruments for unhealthy guys?
ESET Analysis discovered that when SimpleHelp was current on a sufferer’s disk, MuddyWater operators deployed Ligolo, a reverse tunnel, to attach the sufferer’s system to their Command and Management (C&C) servers. How and when MuddyWater got here into possession of the MSP’s tooling or entered the MSP’s setting is unknown. We have now reached out to the MSP.
Whereas this marketing campaign continues, MuddyWater’s use of SimpleHelp has, up to now, efficiently obfuscated the MuddyWater C&C servers – the instructions to provoke Ligolo from SimpleHelp haven’t been captured. Regardless, we are able to already observe that MuddyWater operators are additionally pushing MiniDump (an lsass.exe dumper), CredNinja, and a brand new model of the group’s password dumper MKL64.
In late October 2022, ESET detected MuddyWater deploying a customized reverse tunneling device to the identical sufferer in Saudi Arabia. Whereas its objective was not instantly obvious, the evaluation continues, and progress may be tracked in our private APT Reports.
Alongside utilizing MiniDump to acquire credentials from Native Safety Authority Subsystem Service (LSASS) dumps and leveraging the CredNinja penetration testing device, MuddyWater sports activities different ways and methods, for instance, utilizing in style MSP tools from ConnectWise to realize entry to victims’ methods.
ESET has additionally tracked different methods linked to the group, corresponding to steganography, which obfuscates information in digital media corresponding to photos, audio tracks, video clips, or textual content recordsdata. A 2018 report from ClearSky Cyber Safety, MuddyWater Operations in Lebanon and Oman, additionally paperwork this utilization, sharing hashes for malware hidden in a number of faux resumes – MyCV.doc. ESET detects the obfuscated malware as VBA/TrojanDownloader.Agent.
Whereas 4 years have handed because the publication of the ClearSky report, and the quantity of ESET detections fell from seventh place (with 3.4%) in T3 2021 Threat Report to their most up-to-date rating in “final” place (with 1.8%) in T3 2022 Menace Report, VBA/TrojanDownloader.Agent remained in our prime 10 malware detections chart.
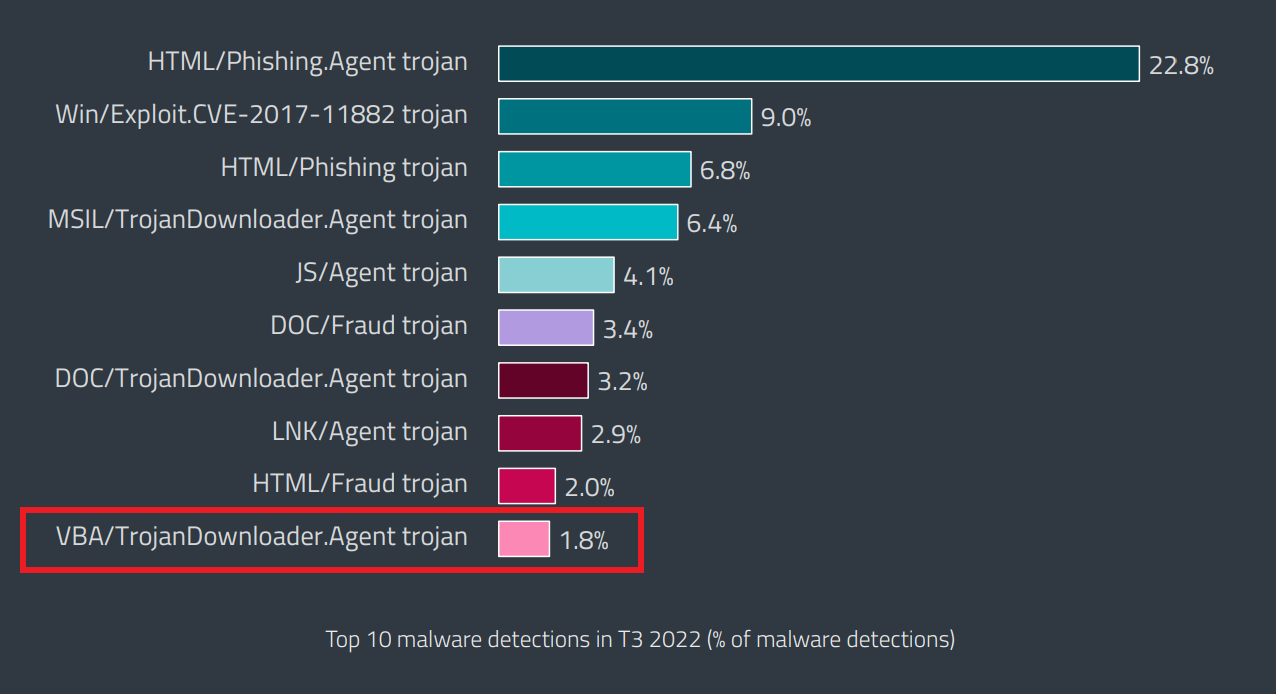
Detections of VBA/TrojanDownloader.Agent within the ESET T3 2022 Threat Report. (Notice: These detections regroup numerous malware households/scripts. As such, VBA/TrojanDownloader.Agent trojan proportion above is just not an unique detection of MuddyWater’s use of this malware sort.)
VBA macros attacks leverage maliciously crafted Microsoft Workplace recordsdata and attempt to manipulate customers (together with MSP staff and shoppers) into enabling the execution of macros. If enabled, the enclosed malicious macro usually downloads and executes extra malware. These malicious paperwork are normally despatched as e mail attachments disguised as necessary info related to the recipient.
A name to motion for MSPs and enterprises
MSP Admins, who configure main productiveness instruments like Microsoft Phrase/Workplace 365/Outlook, run their palms over the very menace vectors carrying threats to the networks they handle. Concurrently, SOC staff members could or could not have their very own EDR/XDR instruments effectively configured to determine whether or not APTs like MuddyWater or legal entities are trying to leverage methods, together with steganography, to entry their very own or shoppers’ methods.
MSPs require each trusted network connectivity and privileged access to buyer methods with a purpose to present companies; this implies they accumulate danger and duty for big numbers of shoppers. Importantly, shoppers may inherit dangers from their chosen MSP’s exercise and setting. This has proven XDR to be a crucial device in supplying visibility into each their very own environments and buyer endpoints, gadgets, and networks to make sure that rising threats, dangerous worker conduct, and undesirable purposes don’t danger their income or fame. The mature operation of XDR instruments by MSPs additionally communicates their energetic function in offering a selected layer of safety for the privileged entry granted to them by shoppers.
When mature MSPs handle XDR, they’re in a a lot better place to counter a variety of threats, together with APT teams which may search to leverage their shoppers’ place in each bodily and digital provide chains. As defenders, SOC groups and MSP admins carry a double burden, sustaining inside visibility and visibility into shoppers’ networks. Shoppers ought to be involved concerning the safety stance of their MSPs and perceive the threats they face, lest a compromise of their supplier results in a compromise of themselves.
RELATED READING:
Choosing your MSP: What the Kaseya incident tells us about third‑party cyber‑risk
Criminal hacking hits Managed Service Providers: Reasons and responses

















