In a latest flip of occasions, Crew Insane Pakistan, a infamous hacking group with ties to Pakistan and Indonesia, has asserted its involvement within the Ediopedia cyberattack. This comes amidst a wave of cyber confrontations between Israel and Palestine.
The group made this declaration on its darkish net discussion board, asserting that the cyberattack is a part of their broader marketing campaign towards Israel.
The Ediopedia Cyberattack: Not the First Offense
Ediopedia, a platform designed for lecturers to change educational materials at socially reasonably priced costs, is at present inaccessible, displaying a “This website can’t be reached” error message.
The menace actor’s put up additionally featured a number of hashtags together with #Oplsraelv2, #AnonymousPakistan, #AllMuslimsHackers, #TeamInsanePk, and #Nameless.
Much like previous cyberattacks against Israel, Crew Insane Pakistan supplied hyperlinks to Examine-Host to permit guests to validate their assertions. On this case, the Ediopedia assault seems to be substantiated, given the present inaccessibility of the web site.
The Cyber Express sought to realize additional perception into the alleged Ediopedia cyberattack by reaching out to the group.
Sadly, because of the unresponsiveness of the web site, communication was not attainable at the moment, leaving the official claims of the Ediopedia assault unverified.
Crew Insane Pakistan’s Marketing campaign
Team Insane Pakistan, also referred to as Crew Insane PK, has gained notoriety for its large-scale cyberattack claims, believed to have roots in each Pakistan and Indonesia.
In line with a report from Cloudsek’s threat research team, the group executed roughly 2,450 focused cyberattacks underneath the banner of ‘#OpIndia’. Over half of those assaults had been distributed denial-of-service (DDoS) attacks.
These assaults had been distributed throughout numerous sectors, together with roughly 370 on authorities digital infrastructure, 80 on non-profit organizations’ web sites, 35 on the finance and banking sector, and round 15 on power and oil division web sites.
The report famous that the group selects targets based mostly on the eye they’ll generate.
Crew Insane Pakistan: Earlier Exploits
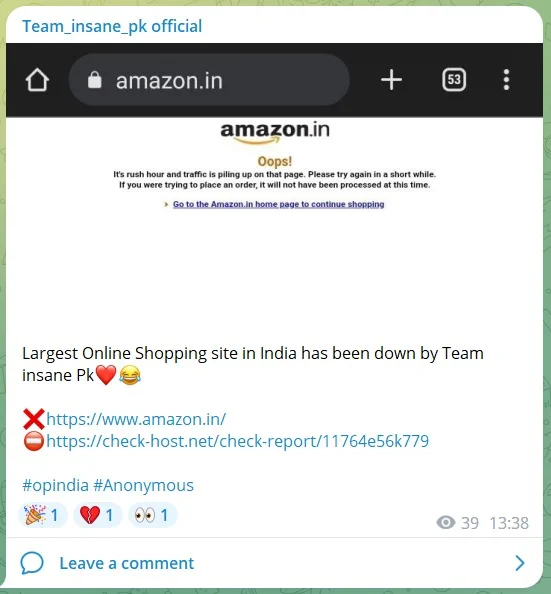
Final month, Crew Insane PK claimed accountability for a cyberattack on Amazon in India. They boldly introduced, “Largest On-line Buying website in India has been shut down by Crew Insane PK,” accompanied by a screenshot implying a profitable takedown of the Amazon India web site.
The purported cyberattack on Amazon India is just not an remoted incident. Crew Insane PK reportedly focused a number of important infrastructures in India, together with web sites like http://uppolice.gov.in, http://traffic.uppolice.gov.in, and http://uphed.gov.in.
Crew Insane Pakistan’s declare of accountability for the Ediopedia cyberattack provides a big chapter to their rising record of exploits — particularly within the war-like state of affairs between Israel and Palestine. The Cyber Categorical is intently monitoring this story and we’ll replace this put up as soon as now we have extra data or official affirmation of the alleged Ediopedia cyberattack.
Media Disclaimer: This report is predicated on inner and exterior analysis obtained by means of numerous means. The knowledge supplied is for reference functions solely, and customers bear full accountability for his or her reliance on it. The Cyber Categorical assumes no legal responsibility for the accuracy or penalties of utilizing this data.
Associated














