We’ve all misplaced depend of what number of occasions we’ve entered our electronic mail handle and telephone quantity to join a web based service, entry a web site or an app, learn the information or log into any of the social media accounts most of us have. Put bluntly, our contact info is everywhere in the web.
On the identical time, being secure and personal on-line will be laborious work and time-consuming, primarily if we’ve got to consider managing settings and what info we need to share each single time we sign up for a new service or make a web based buy. It turns into overwhelming and will undoubtedly be made extra environment friendly.
Can we make it simpler? Identical to taking Sunday night to prep some meals for the week, we are able to spend a while right this moment to guard our on-line privateness for the months forward!
Disposable and short-term: the artwork of on-line camouflage
Momentary electronic mail handle and a secondary inbox
As most web sites require an electronic mail handle to register, most of us will merely enter our main electronic mail handle. Why would we’d like a couple of inbox anyway? The truth, nevertheless, suggests in any other case. After we register a brand new account and even simply enter our electronic mail to entry restricted content material, we’re most frequently additionally agreeing to the switch of our contact info from a sure service to a different for advertising and marketing functions.
Nevertheless it doesn’t need to be that manner. What to do as a substitute?
Technique 1: Use a disposable electronic mail handle – for belongings you don’t actually care that a lot about.
Quite a lot of disposable electronic mail companies allow you to use a brief electronic mail that self-destructs after a set time period. This is available in significantly helpful for one-time use, for instance if you find yourself requested to submit an electronic mail handle to entry restricted content material, however don’t essentially need to run the danger of being bombarded by advertising and marketing communications and spam.
A caveat applies, nevertheless, and we are able to’t stress this sufficient: it’s not a good suggestion to make use of these companies for any communications which will contain actually delicate knowledge.
Technique 2: Create a secondary electronic mail handle for logins and essential newsletters.
For all authorities, banking and different key contacts, use an end-to-end encrypted electronic mail service as ProtonMail. Don’t use your main electronic mail handle for something aside from staying in contact along with your family and friends. It will preserve your inbox organized, freed from spam and shielded from knowledge leaks in case a service you’re registered with suffers a knowledge breach.
Alternatively, you may as well use a characteristic akin to Apple’s Hide My Email to join a service with out gifting away your actual electronic mail. Apple creates a novel handle that masks your actual handle and supplies it to the service you’re signing as much as. All emails will then be forwarded robotically from the masked account to yours. Whereas Android doesn’t but supply an analogous characteristic, there are a couple of options, akin to Firefox Relay.
The burner telephone quantity
Together with electronic mail addresses, your telephone quantity is a must have to register and log into a variety of web sites, to obtain timed passwords that verify your id and even for on-line retailers handy over your contact particulars to supply companies.
All in all, your telephone quantity is in every single place, so no marvel most of us already obtain random texts and WhatsApp scam makes an attempt.
Technique 3: Get an inexpensive pay as you go SIM card.
Often, this can be a low cost card that you just solely need to prime up with a couple of bucks each few months to maintain it on and, in most nations, you aren’t required to point out an ID to make use of it. The aim is to make use of this telephone quantity for all of your on-line wants: You may hyperlink it to social media accounts, use it for parcel monitoring numbers, share with potential dates you meet on-line and use it for basic anonymity.
In the meantime, your actual main quantity ought to solely be shared with household, pals and authorities or monetary establishments. Since you use the burner quantity to your on-line functions, if you happen to get a name, you may instantly assume it’s a rip-off and, most certainly, some web site you had been registered at suffered a knowledge breach.
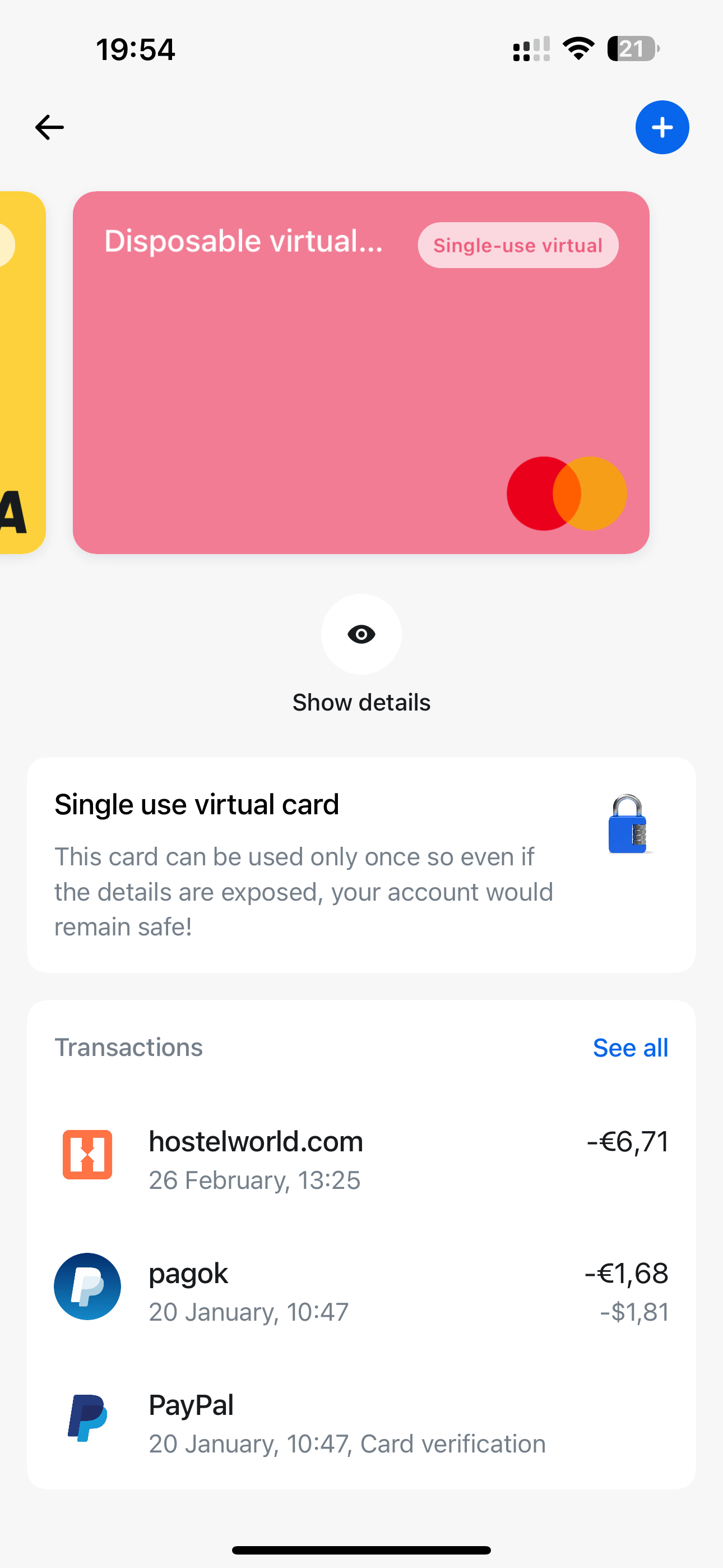
Single-use financial institution playing cards
Shopping for on-line will be actually handy, little doubt! We simply have to enter the web site, select what we would like and normally we have already got our banking card particulars saved from a earlier buy. All good. Until there’s a knowledge breach affecting the main points saved on that web site that compromises our card particulars or we fall sufferer to a nasty social engineering scam!
Technique 4: Go for single-use, digital playing cards.
Many banks, primarily these primarily based on cellular purposes, supply digital playing cards as a substitute, or as an extra possibility on prime of the bodily card. And most of those banks may also supply disposable single-use playing cards which can be related to your actual card. When you make a purchase with a single-use card, the financial institution system will detect the motion, destroy these card particulars and robotically generate new ones prepared for the following buy. As a result of this can be a randomized card, hackers received’t have the ability to monitor your actual info.
And in case you’re questioning about refunds, the sellers can nonetheless return the cash by means of the identical single-purchase card particulars to your account.
Two-factor authentication and one-time codes
Most on-line companies today permit – and advocate – the usage of two-factor authentication (2FA). That’s, aside from coming into your password, you may as well be required to carry out an additional authentication step. This manner, if somebody steals your password, they nonetheless received’t have the ability to log in with out the 2FA code of their fingers.
Technique 5: Use app-generated 2FA passcodes.
Most frequently, 2FA includes sending an SMS message to your telephone quantity (hopefully your burner telephone) with a one-time passcode (OTP). You solely have to kind it in the place requested to show your id. One other – and higher – manner depends on utilizing authentication apps akin to Microsoft Authenticator. Beneath their privateness settings, most web sites supply the chance to generate a QR or alphanumeric code that may be enter on the authenticator app; in flip, the app will generate a brief code that works identical to an OTP.
This second technique is one thing you would possibly need to get used to – and never simply because Twitter stopped supporting SMS-borne 2FA for non-paying users just lately.
Let’s recap!
- Create short-term electronic mail accounts for when you should cross a restricted content material wall that requests your electronic mail handle for additional entry.
- Use a good electronic mail supplier, akin to Gmail or Outlook, to create a secondary account that you just use for on-line companies and web site signups.
- Get a burner quantity to keep away from getting SMS and rip-off calls.
- Use digital disposable banking playing cards which can be self-destroyed after a single use.
- Use one-time codes for two-factor authentication on prime of a strong and unique password.
Embracing your on-line privateness as a part of your regular routine will make it really feel seamless and pure, taking away the sensation of burden and fixed doubt about whether or not you’re doing sufficient to guard your digital life. General, utilizing electronic mail addresses, telephone numbers and playing cards that aren’t instantly linked to you can be an effective way to minimize your digital footprint and slash the danger of being the victim of a data breach or rip-off. Lastly, there’s simply as a lot we as customers can do to forestall malicious exercise; it’s at all times advisable to make use of digital safety software program that protects you from different potential dangers and assaults.