Privateness
A primer on how one can use this highly effective instrument for uncovering and connecting data from publicly out there sources
22 Jun 2023
•
,
4 min. learn

It’s a truism that non-public information is a worthwhile asset for cybercriminals, because it permits them to tailor and in any other case enhance their phishing and different social engineering assaults. The wealth and number of private information that’s out there on-line is leveraged for assaults and scams that concentrate on not solely folks but additionally firms.
However organizations can also faucet into strategies equivalent to Open Source Intelligence (OSINT) that permit them to see their community the best way attackers may see it and to collect numerous sorts of publicly out there details about themselves with the intention to determine their weak factors and finally improve their safety. One such standard and highly effective information-gathering instrument is a chunk of software program referred to as Maltego.
What’s Maltego and why use it?
Maltego is a chunk of software program that enables moral hackers, penetration testers and different safety practitioners to uncover details about folks or firms on the web. It allows them to cross-match information and map out connections between social media profiles, e mail addresses, cellphone numbers, places, skilled affiliations and different data. The knowledge is represented in easy-to-digest graphical hyperlinks and relationship diagrams.
Learn additionally: 5 free OSINT tools for social media
Maltego presents a slew of advantages for numerous entities, each within the non-public and public sectors. Cybersecurity practitioners can leverage Maltego for gathering worthwhile details about threats which may jeopardize the safety of an organization’s data and infrastructure. Regulation enforcement businesses can use Maltego to gather worthwhile information that helps in investigating fraud and gathering digital proof, amongst different issues.
What kind of knowledge can Maltego accumulate?
The instrument’s most-used options are these that allow you to determine and visualize relationships between what the instrument calls entities, equivalent to IP addresses, domains, e-mails, social media profiles, and so on. As well as, Maltego means that you can combine completely different sources of knowledge, equivalent to databases, on-line search instruments, APIs, and so on.
Even Maltego’s free model fetches a considerable amount of data, together with:
- Community data: Maltego can scan and collect details about community hosts, open ports and protocols used. For instance, with Maltego, you’ll be able to obtain Shodan inside the instrument, which lets you collect extra particular details about the community to be analyzed.
- Area and e mail data: Maltego can collect details about domains, equivalent to our DNS entries, e mail logs, and host identify logs. It could additionally collect details about e mail addresses, domains, e mail suppliers and DNS information.
- Social media data: You will get Maltego to gather numerous varieties of knowledge from social media, together with profiles, posts, associates, followers and connections.
- Details about folks and organizations: Maltego can collect details about folks or organizations, together with their names, addresses, phone numbers, e mail addresses, web sites and social media profiles.
- Malware data: Maltego can collect details about malware, equivalent to file names, fingerprints, assault patterns and habits. This helps collect details about threats, making it a helpful instrument for menace intelligence duties.
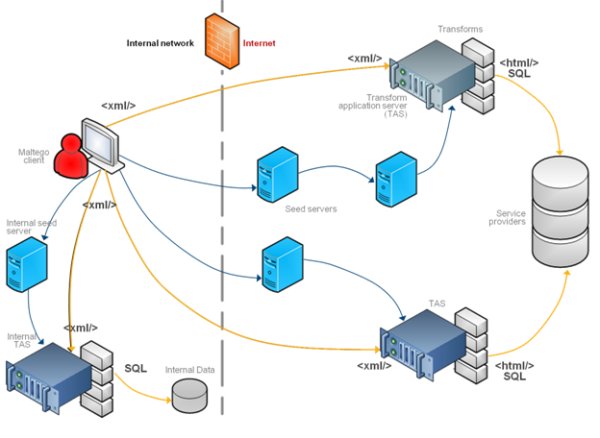
Right here’s what occurs beneath the hood:
- The Maltego consumer sends a request in XML format to seed servers over HTTPS.
- The request from the seed server is shipped to rework software servers (TAS) that, in flip, ahead it to the service suppliers.
- The outcomes are despatched to the Maltego consumer.
The way to use Maltego
Download and install Maltego on Home windows, macOS or Linux and create an account on the instrument’s web site that can let you use the app and the free servers. As soon as you put in the software program and check in, you must create a brand new search web page and drag the entity there (i.e., the kind of search you wish to make – on this case, an individual) to then run the search and see the outcomes.
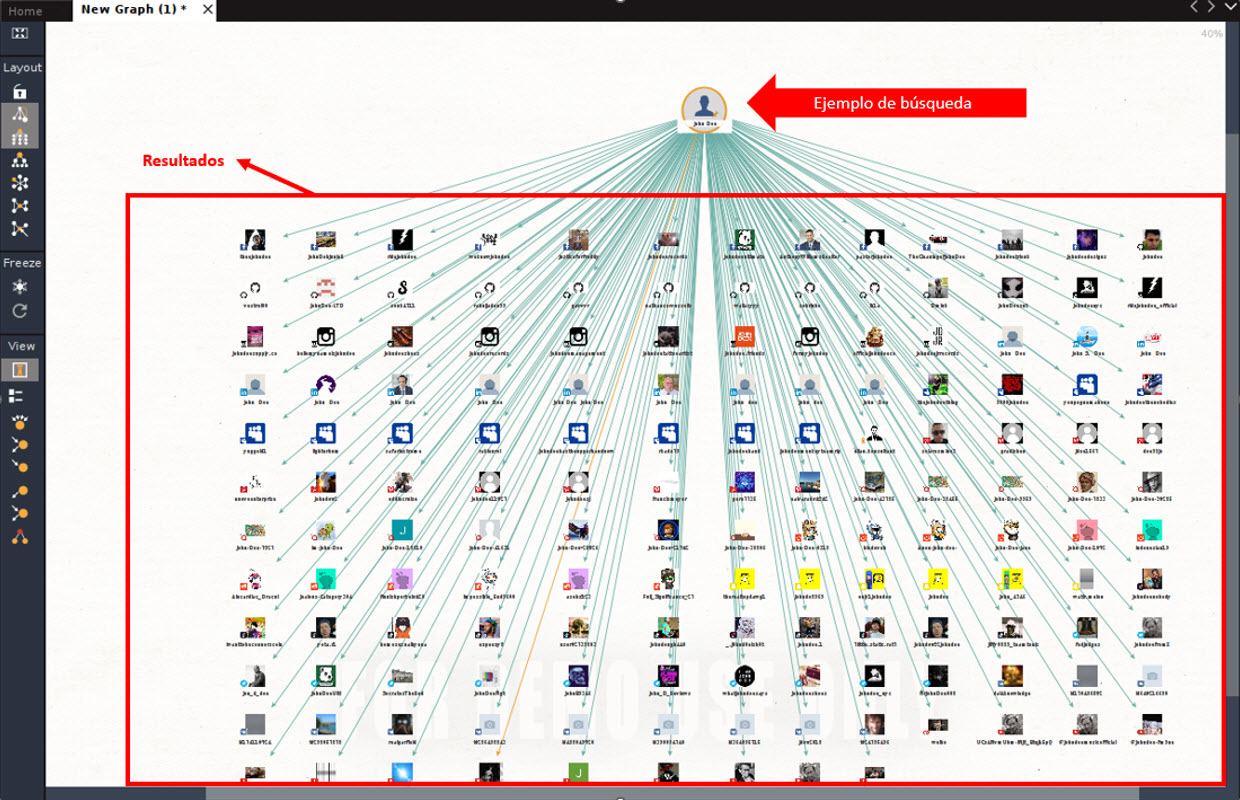
Upon getting chosen the kind of search you wish to make, double click on on the individual icon to entry the configuration part and, when you enter the identify, excellent click on on the individual icon and choose “run rework”. Inside this class, there are completely different subcategories, the place you’ll be able to seek for particular data, equivalent to e mail addresses, IP addresses of a web site, and so on. On this specific case, we are going to use the “all transforms” choice to seek for all doable data within the Web, so it would rapidly begin gathering information and the outcome will probably be just like that proven within the picture under:
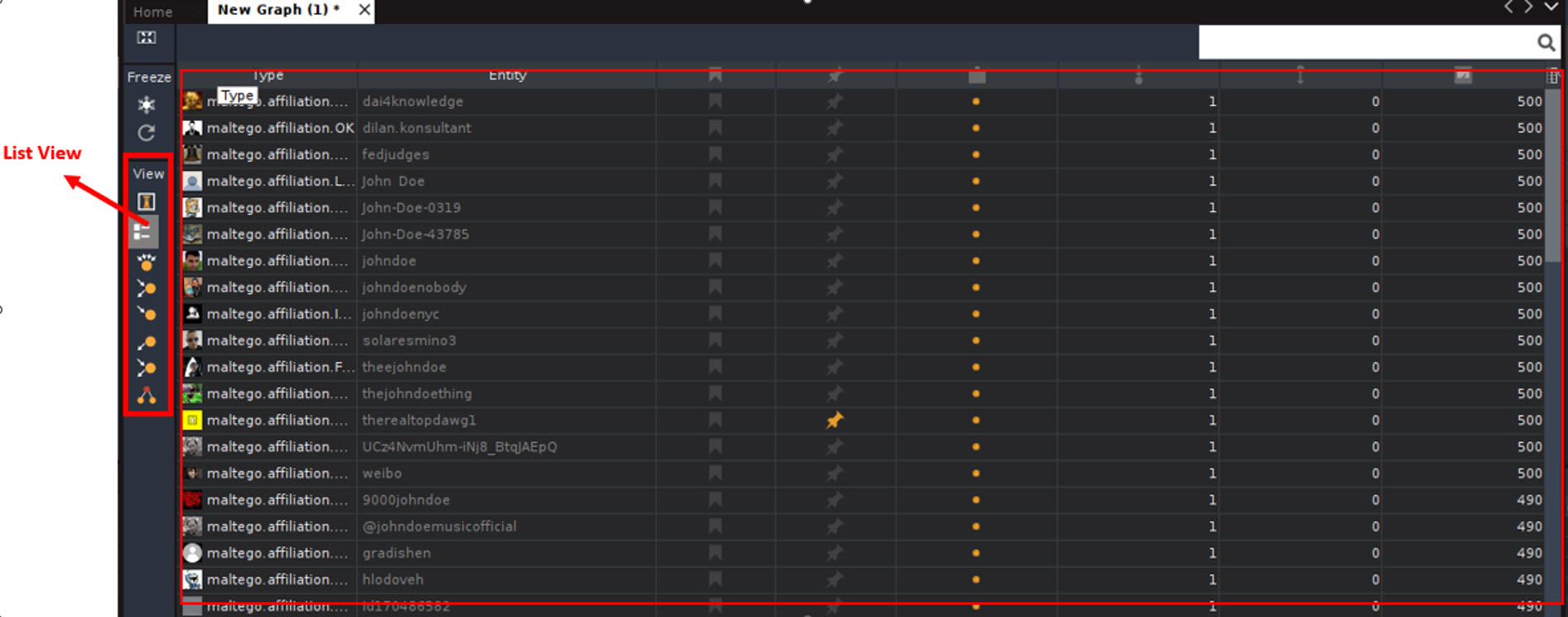
Within the screenshot, you’ll be able to see web sites the place the identify “John Doe” was talked about or there may be data associated to it. It’s value mentioning that this instrument is so highly effective that it might discover profiles in Fb, LinkedIn, Instagram, Tik Tok, Snapchat, Twitter, and Youtube, amongst others. However that’s not all, as you can too discover associates associated to this individual in social media. To see it in additional element, click on on the “Listing View” button within the “View” lateral bar, the place you’ll be able to see the hyperlinks and different data.
Conclusion
The knowledge gathered utilizing Maltego may also be utilized by cybercriminals when deploying their assaults. For this reason it’s helpful to know what sort of data a cybercriminal can find out about us or our firm and be cognizant of – and presumably lower – our stage of publicity.
It goes with out saying that everytime you use an OSINT instrument, be sure to are conscious of native and nationwide legal guidelines and laws associated to the gathering and use of knowledge in order that you don’t commit a criminal offense or violate the privateness of others. Additionally, when amassing and storing data, it is very important take measures to guard it towards doable theft or information breaches.