ESET has collaborated with Microsoft, BitSight, Lumen, Cloudflare, CleanDNS, and GMO Registry in a world disruption operation in opposition to Lumma Stealer, an notorious malware-as-a-service (MaaS) infostealer. The operation focused Lumma Stealer infrastructure with all identified C&C servers prior to now yr, rendering the exfiltration community, or a big a part of it, nonoperational.
Key factors of this blogpost:
- ESET took half in a coordinated international operation to disrupt Lumma Stealer.
- ESET offered technical evaluation and statistical data, and extracted important information from tens of hundreds of malware samples.
- We offer an outline of the Lumma Stealer MaaS ecosystem.
- We additionally present technical evaluation and an outline of the evolution of Lumma Stealer’s key static and dynamic properties, which have been crucial to the disruption effort.
Disruption contribution
ESET automated techniques processed tens of hundreds of Lumma Stealer samples, dissecting them to extract key components, akin to C&C servers and affiliate identifiers. This allowed us to repeatedly monitor Lumma Stealer’s exercise, monitor growth updates, cluster associates, and extra.
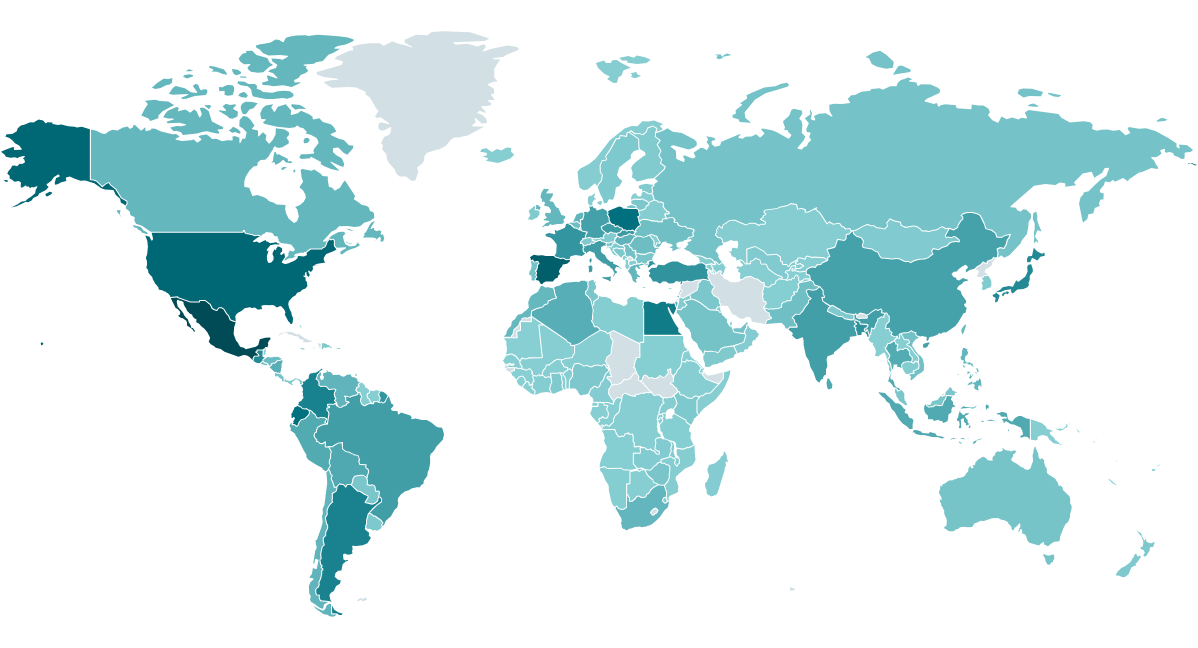
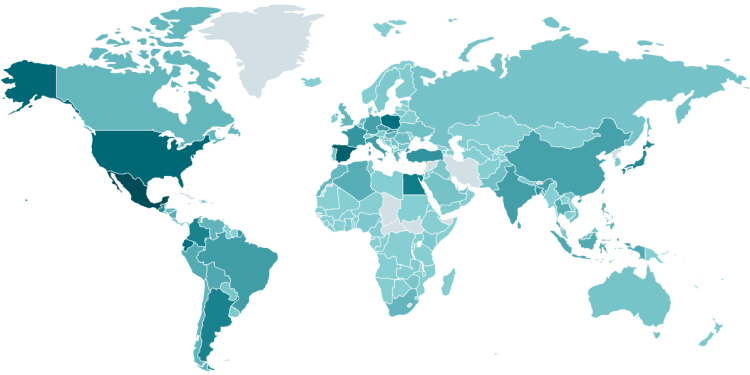
Infostealer malware households, like Lumma Stealer, are sometimes only a foreshadowing of a future, rather more devastating assault. Harvested credentials are a valued commodity within the cybercrime underground, offered by preliminary entry brokers to numerous different cybercriminals, together with ransomware associates. Lumma Stealer has been probably the most prevalent infostealers over the previous two years, and ESET telemetry (see Determine 1) confirms that it has left no a part of the world untouched.
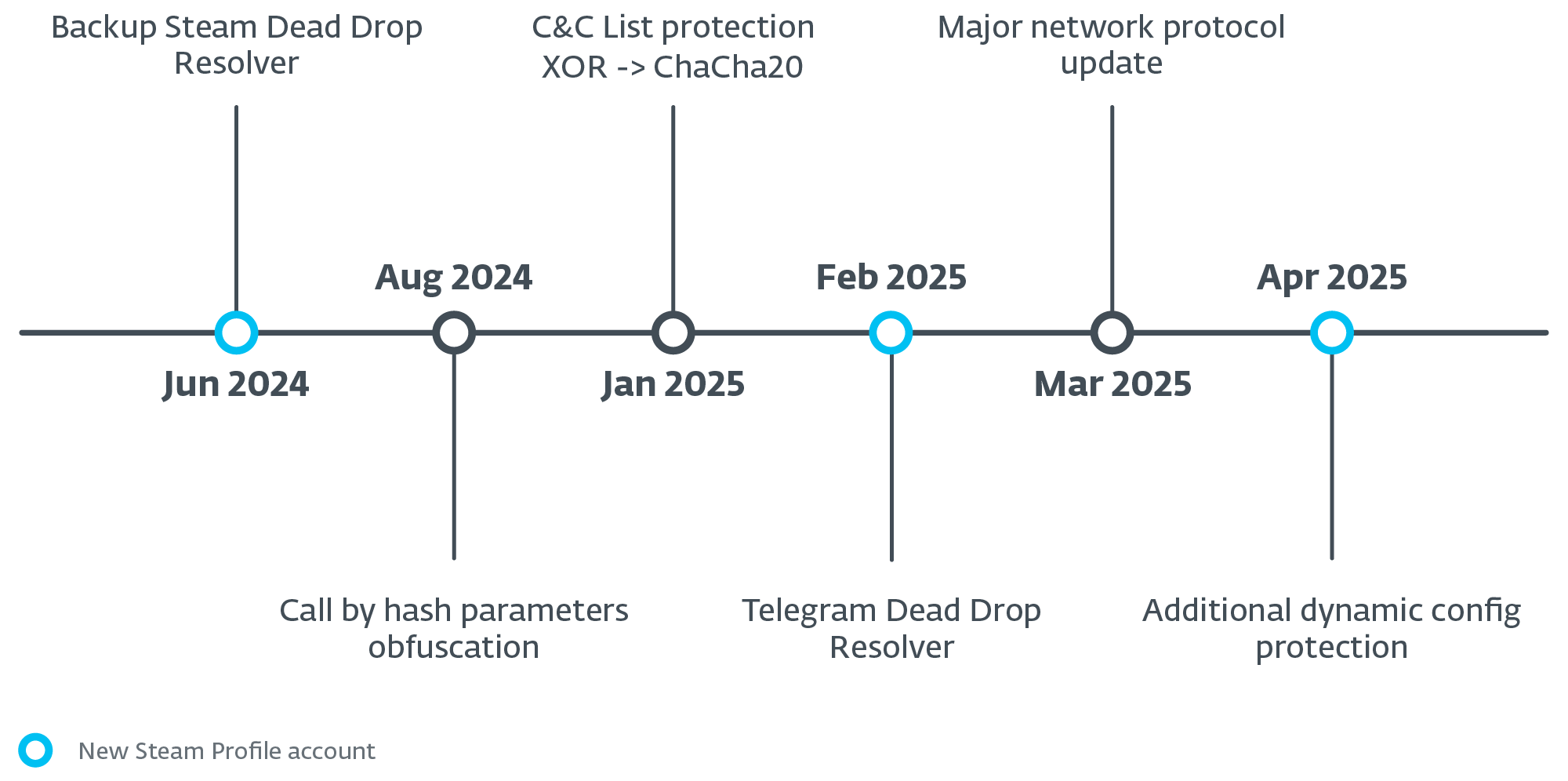
Lumma Stealer builders had been actively creating and sustaining their malware. We have now frequently seen code updates starting from minor bug fixes to finish alternative of string encryption algorithms and modifications to the community protocol. The operators additionally actively maintained the shared exfiltration community infrastructure. Between June 17th, 2024 and Could 1st, 2025, we noticed a complete of three,353 distinctive C&C domains, averaging roughly 74 new domains rising every week together with occasional updates to Telegram-based dead-drop resolvers (see Determine 2). We talk about the main points of the community infrastructure later within the blogpost.
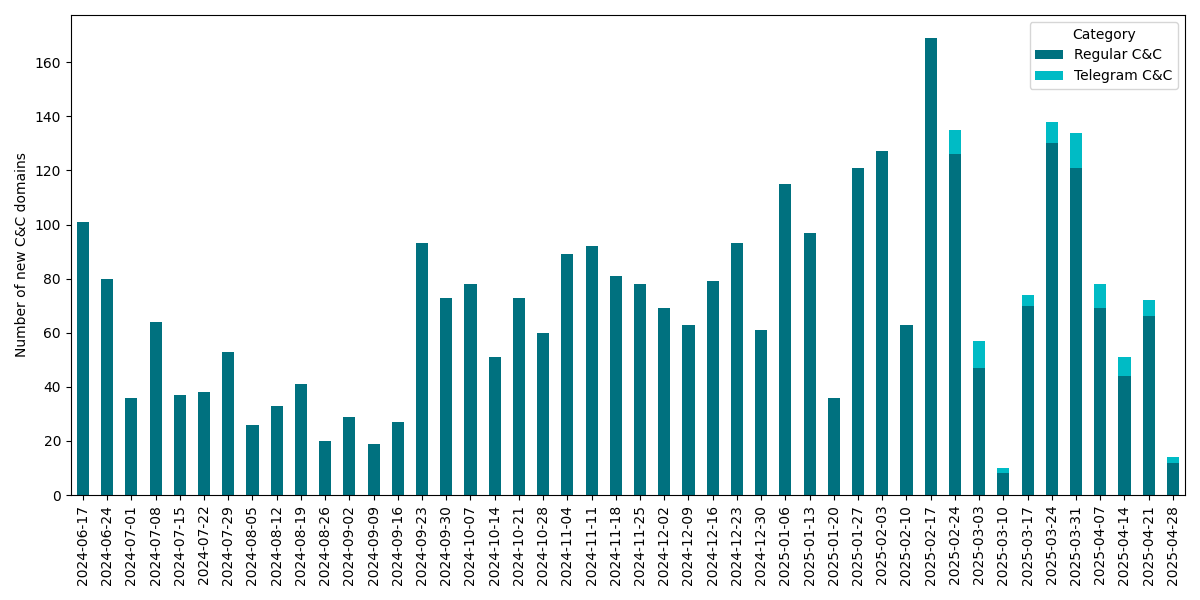
This ongoing evolution underscores the numerous menace posed by Lumma Stealer and highlights the significance and complexity of the disruption effort.
Background
Over the previous two years, Lumma Stealer (often known as LummaC or LummaC2) has emerged as probably the most lively infostealers within the cybercrime ecosystem, changing into a popular software amongst cybercriminals on account of its lively growth of malware options and its infrastructure being offered as a service.
Malware as a service
Lumma Stealer adopts the idea of malware as a service (MaaS), the place associates pay a month-to-month charge, based mostly on their tier, to obtain the most recent malware builds and the community infrastructure mandatory for information exfiltration. Associates have entry to a administration panel with a user-friendly interface the place they’ll obtain exfiltrated information and harvested credentials.
The tiered subscription mannequin ranges from USD 250 to USD 1,000 per thirty days, every with more and more subtle options. Decrease tiers embody fundamental filtering and log obtain choices, whereas increased tiers provide customized information assortment, evasion instruments, and early entry to new options. The costliest plan emphasizes stealth and flexibility, providing distinctive construct era and decreased detection.
The operators of Lumma Stealer have additionally created a Telegram market with a ranking system for associates to promote stolen information with out intermediaries. {The marketplace} has been effectively documented in Cybereason research. Furthermore, they keep public documentation of the administration panel for associates and periodically share updates and fixes on hacking boards, as proven in Determine 3.
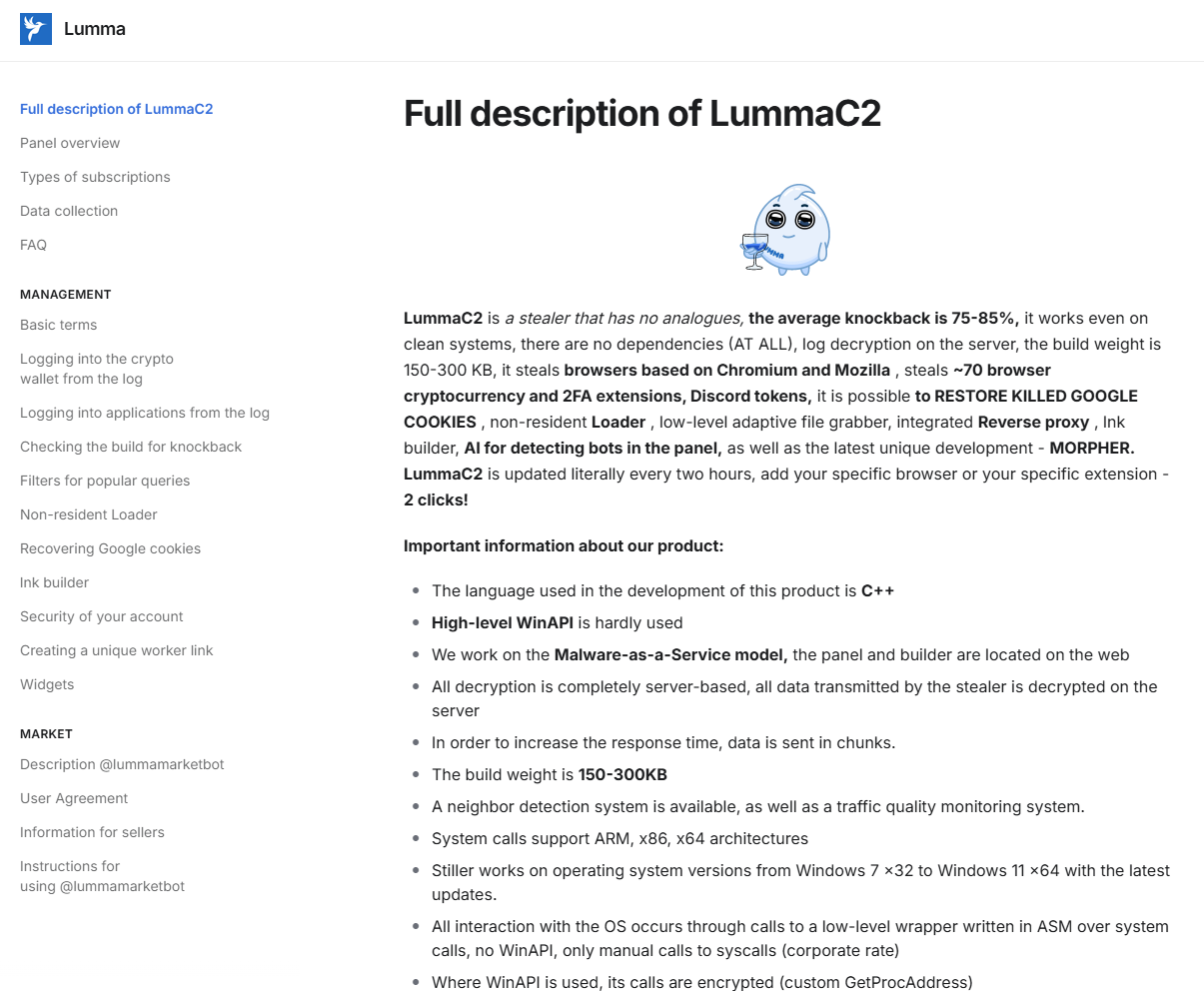
Open documentation not solely helps associates with much less expertise to make use of the malware service, but additionally offers precious insights for safety researchers. Builders deal with malware builds, information pipelining, and infrastructure upkeep, whereas associates are accountable for distributing the malware. This data, mixed with the service’s recognition, ends in all kinds of compromise vectors.
Frequent distribution strategies embody phishing, cracked software program, and different malware downloaders together with SmokeLoader, DarkGate, Amadey, Vidar, and others. Well-liked phishing schemes contain ClickFix or fake CAPTCHA internet pages, fraudulent boards with cracked software, pretend GitHub repositories, fraudulent hyperlinks on Reddit boards, and lots of extra.
Technical evaluation
Quite a few public analyses have already been written about Lumma Stealer and its compromise vectors. Our focus right here, nonetheless, is on the facets related to the disruption. On this part, we’ll briefly introduce the important thing static and dynamic properties that now we have been actively extracting from Lumma Stealer.
Static properties of Lumma Stealer
Varied data comes embedded in Lumma Stealer malware samples. This naturally presents a perfect goal for automated extraction. In addition to the plain information of curiosity – C&C server domains – the samples additionally comprise identifier strings that tie the pattern to a selected affiliate and a marketing campaign, and an non-obligatory identifier resulting in a customized dynamic configuration. These identifiers are utilized in community communication with the C&C server throughout information exfiltration and requests for dynamic configuration. Within the sections beneath, we take a look at these properties in depth.
C&C domains
Every Lumma Stealer pattern accommodates an inventory of 9 encrypted C&C domains. Whereas the encryption strategies have developed over time, the attribute array construction has remained constant as much as the time of writing.
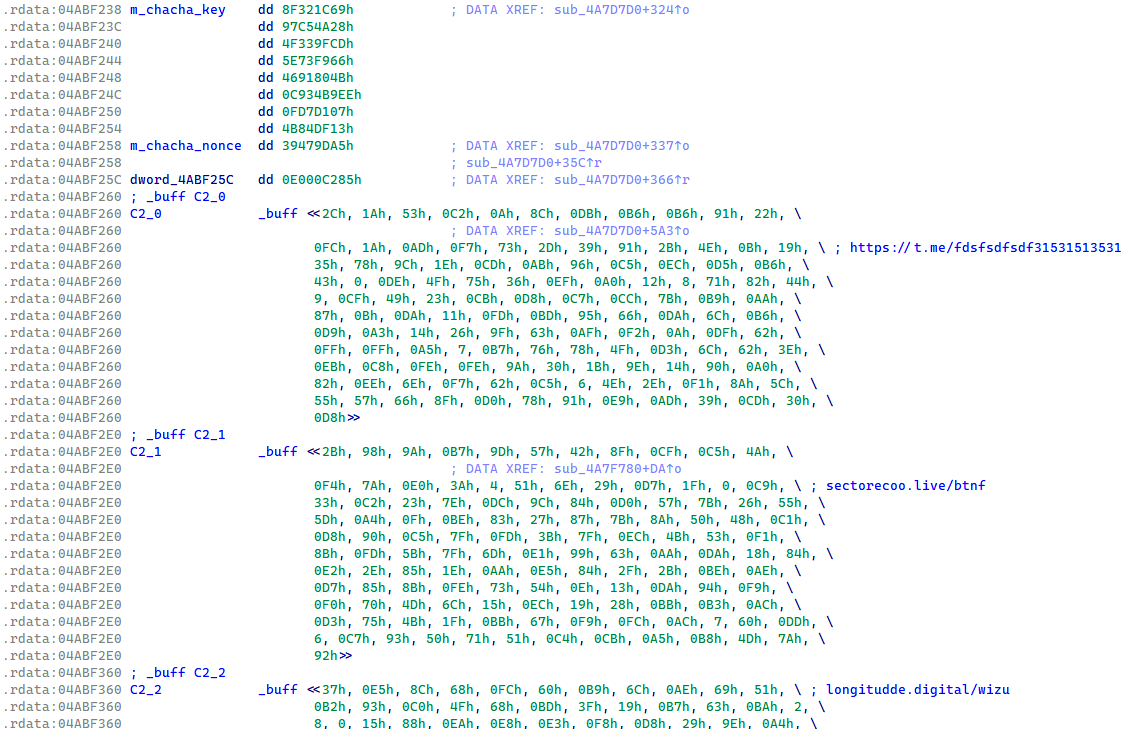
Primarily based on Lumma Stealer’s inner pattern versioning, which is closely protected by stack string obfuscation, we all know that up till January 2025, the C&C domains within the samples have been protected by an XOR perform and base64 encoding (see Determine 4). When the base64-encoded string was decoded, it revealed a construction the place the primary 32 bytes served as an XOR key, and the remaining bytes contained the encrypted C&C area.
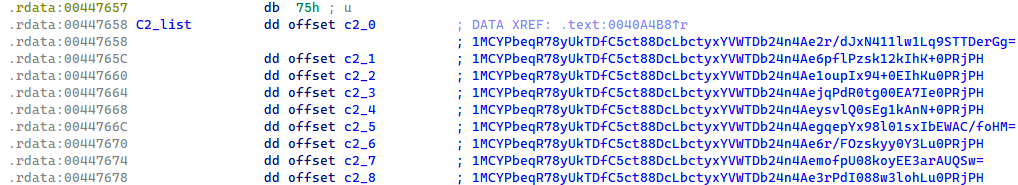
In January 2025, Lumma Stealer transitioned the safety of the C&C record to ChaCha20 encryption with a single hardcoded key and nonce (see Determine 5). This safety of the C&C record within the Lumma Stealer binaries has remained the identical up till the time of publication.
Lifeless-drop resolvers
Since June 2024, every Lumma Stealer construct got here with a brand new characteristic for acquiring a backup C&C. If no C&C server from the static config responds to Lumma Stealer, then the backup C&C is extracted from a dummy Steam profile internet web page performing as a dead-drop resolver. The Steam profile URL is closely protected within the binary, the identical means because the model string. The encrypted backup C&C URL is about within the Steam profile identify, as proven in Determine 6, and the safety is an easy Caesar cipher (ROT11).

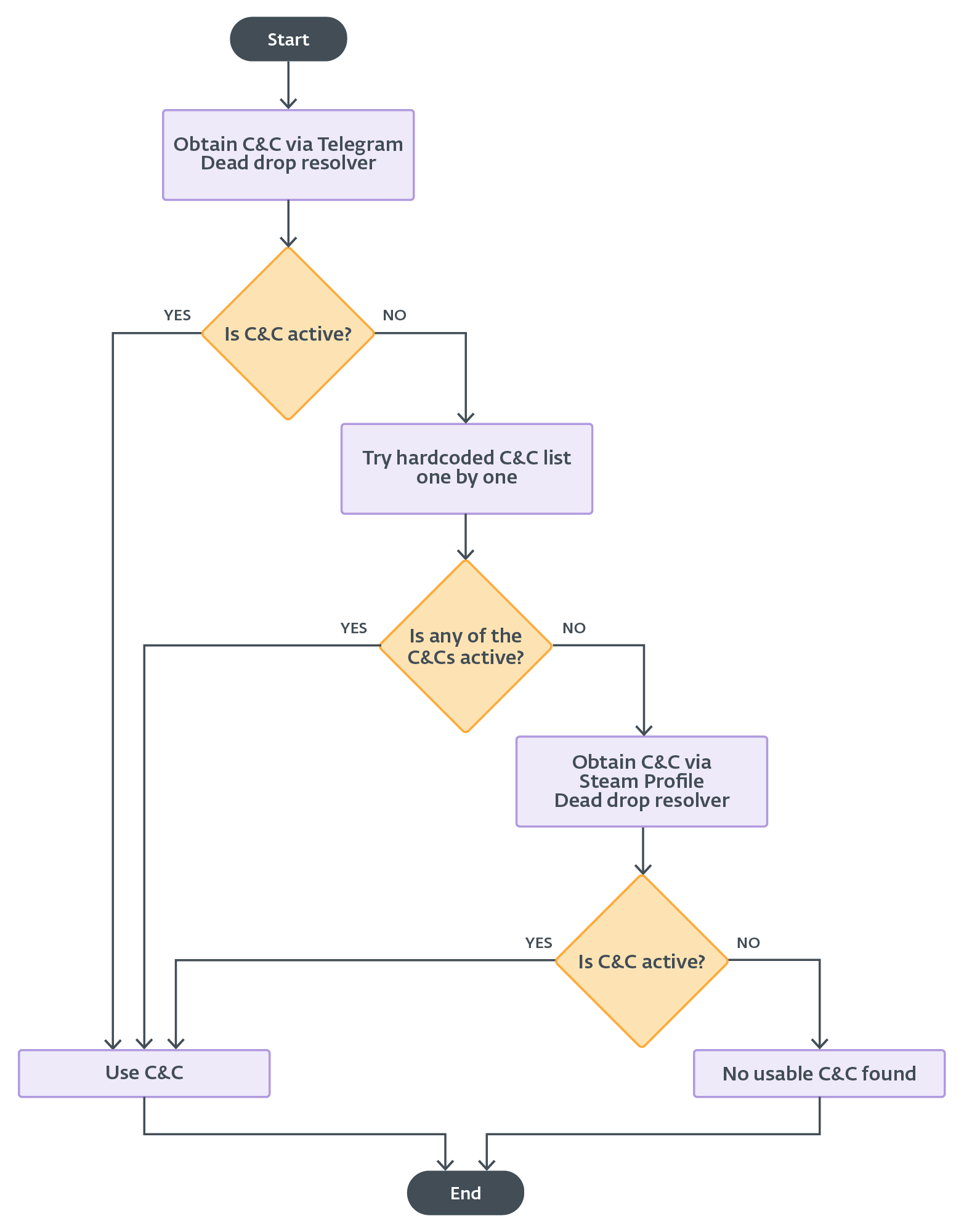
In February 2025, Lumma Stealer obtained an replace that included a characteristic for acquiring a brand new, main C&C URL from a Telegram channel dead-drop resolver. The C&C URL is extracted from the Telegram channel’s title subject, and it’s protected by the identical algorithm as within the case of the Steam profile dead-drop resolver. The primary distinction within the utilization of the Telegram and Steam profile dead-drop resolvers is that the Telegram possibility is examined first, whereas the Steam profile is used as a final resort if profitable communication has not been established with beforehand obtained C&C servers (Determine 16).
Furthermore, we imagine that the Telegram dead-drop resolver is out there for increased tier subscriptions. It’s because many samples wouldn’t have the Telegram URL set, and subsequently the malware skips this methodology.
Lumma Stealer identifier
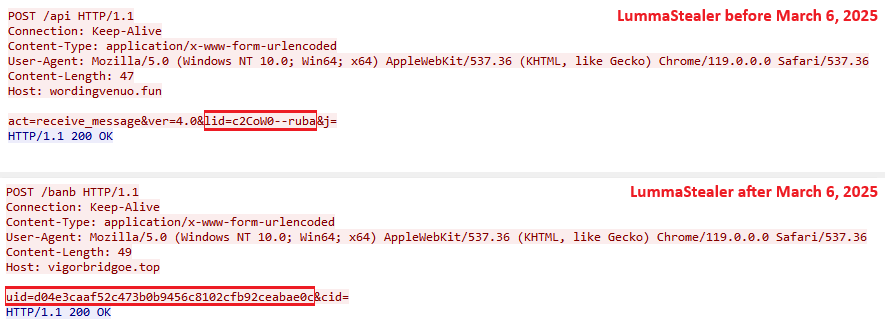
Every Lumma Stealer pattern accommodates a novel hardcoded affiliate identifier referred to as LID. It’s embedded in plaintext type and utilized for communication with C&C servers. Up till March 2025, the LID parameter string adopted a structured format, delimited by two dashes (Determine 7). A detailed evaluation of the LID affiliate string is offered in an upcoming part.
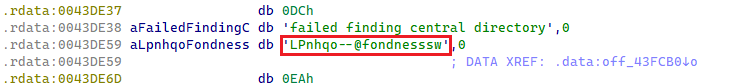
Though probably the most prevalent LID noticed throughout our monitoring begins with the string uz4s1o; the second most typical LID, which begins with LPnhqo, offers a greater instance for visualizing typical LID variability. Within the phrase cloud in Determine 8, we current the highest 200 LIDs collected throughout our monitoring, beginning with LPnhqo.

Nevertheless, in early March 2025, Lumma Stealer transitioned to utilizing hexadecimal identifiers, referred to internally as UID (see Determine 9).
Elective configuration identifier
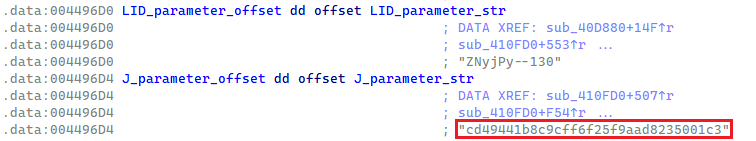
Along with the LID parameter, Lumma Stealer samples may additionally comprise an non-obligatory parameter referred to internally as J. When current, this parameter is in cleartext and formatted as a 32-byte ASCII hex string (see Determine 10). The J parameter is utilized within the C&C request for dynamic configuration with further definitions for exfiltration. We speak about dynamic configuration in additional element in a following part.
If the J parameter is lacking within the Lumma Stealer pattern, an empty string is used within the C&C request and a default configuration is retrieved. Not like LID, the J parameter is never current in Lumma Stealer samples. Nevertheless, it performs an important position when current, because it permits retrieving a dynamic configuration that considerably will increase the stealer’s capabilities, making it a extra versatile exfiltration software for menace actors.
In March 2025, when the LID parameter was renamed to UID and its format modified, the J parameter was renamed to CID however with no change to its format or perform.
Evaluation of static properties
From our long-term monitoring and statistical evaluation of LID parameters, we imagine that the primary section of the LID identifies the affiliate, whereas the second section differentiates between campaigns. Primarily based on this assumption you possibly can see the highest 200 affiliate identifiers in Determine 11.
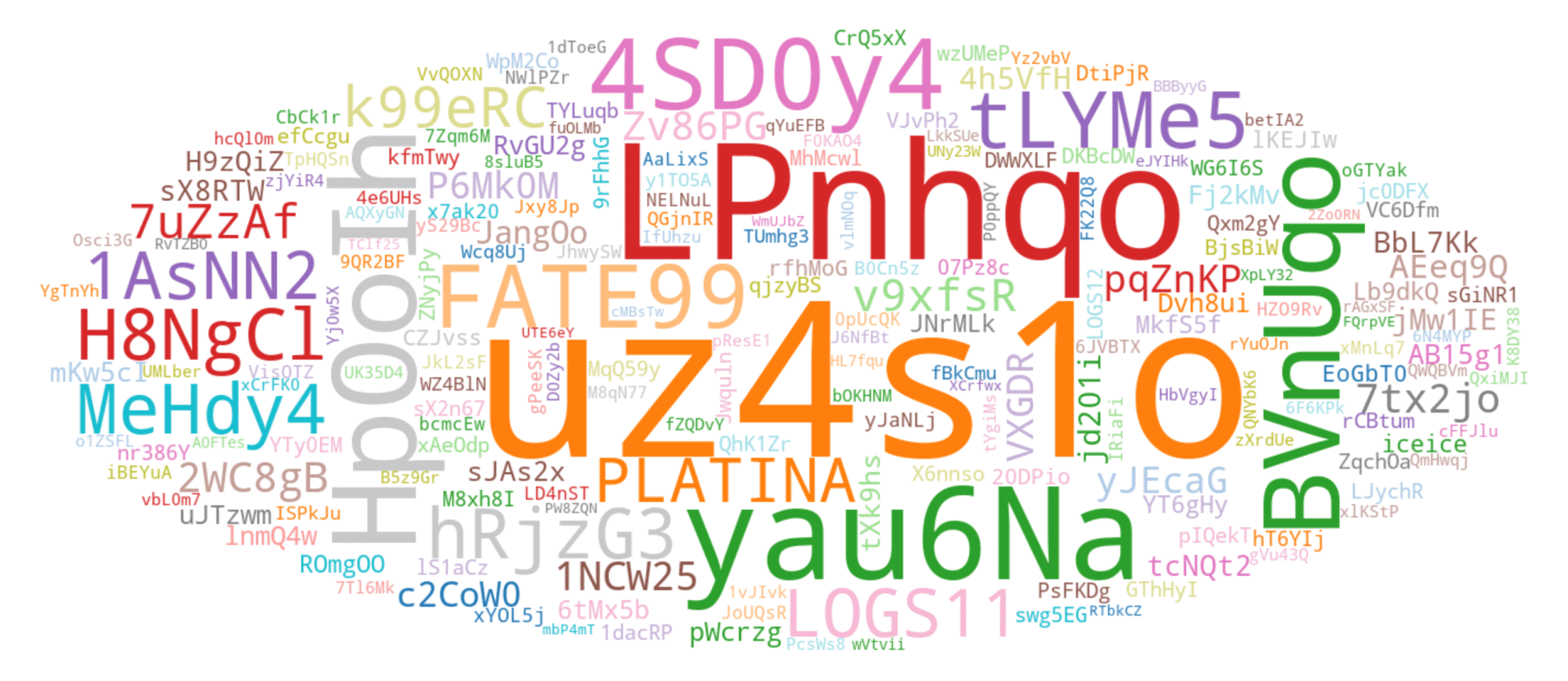
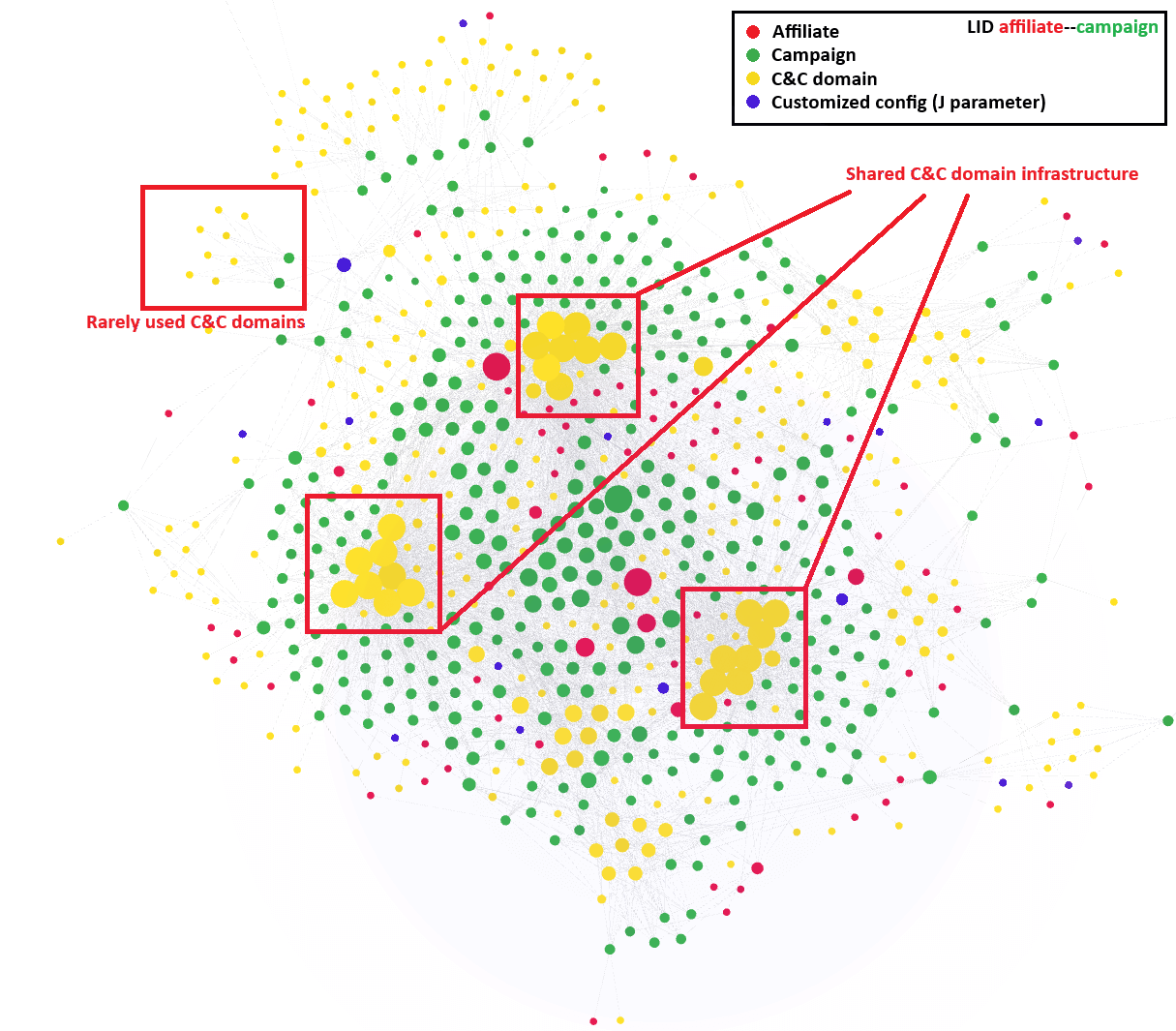
Furthermore, now we have been capable of create a visualization of the associates’ actions over the previous yr (see Determine 12). This visualization highlights every week in January 2025. All these visualizations have offered us with precious insights into the patterns and behaviors of various menace actors. Moreover, the visualizations reveal a shared, domain-based C&C infrastructure amongst most Lumma Stealer associates. On the identical time, we have been capable of establish much less continuously used C&C domains, which we suspect have been reserved for increased tier associates or extra necessary campaigns.
Dynamic properties of Lumma Stealer
Lumma Stealer retrieves a dynamic configuration from the C&C server, which accommodates definitions specifying what to scan for exfiltration (see Desk 1). The first focus is on stealing internet browser extension information and databases containing passwords, session cookies, internet looking historical past, and autofill information. In addition to internet browsers, it additionally focuses on stealing information from password managers, VPNs, FTP purchasers, cloud providers, distant desktop purposes, e-mail purchasers, cryptocurrency wallets, and note-taking purposes.
Desk 1. Dynamic config’s JSON fields
| Key | Description |
| v | Dynamic config model. |
| se | Choice for taking a screenshot of the sufferer’s machine for exfiltration. |
| ex | Record of Chromium-based browser extensions to focus on for exfiltration. Every entry consists of: · The extension ID, saved as en. · The extension identify, saved as ez. |
| c | Definition of recordsdata focused for exfiltration. Probably the most attention-grabbing entries are: · The trail for file scanning, saved as p. · The file extension record filter for exfiltration, saved as m. · The utmost folder scanning depth, saved as d. · The utmost file measurement for exfiltration, saved as fs. |
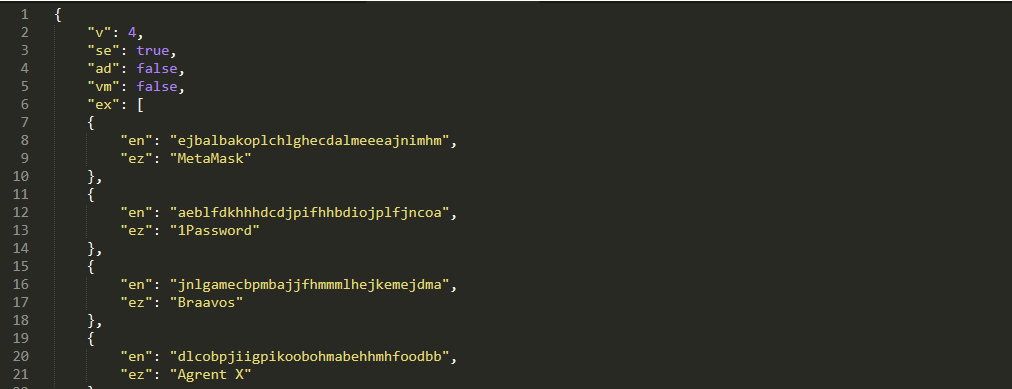
Despite the fact that we haven’t seen vital modifications within the default configurations, this characteristic enhances the malware’s capacity to carry out focused exfiltration (see Determine 13). A complete overview of the configuration fields has already been effectively documented on this research by SpyCloud.
The configuration is in JSON format, and it’s downloaded from the C&C server utilizing an HTTPS POST request that features the LID identifier, non-obligatory J parameter, and a selected hardcoded Person-Agent string.
The safety of the dynamic configuration has modified a number of occasions just lately. Previously, it was protected in the identical means because the static C&C record, by a 32-byte XOR perform and base64 encoding. In March 2025 the safety modified to ChaCha20, the place the important thing and nonce have been prepended to the encrypted configuration.
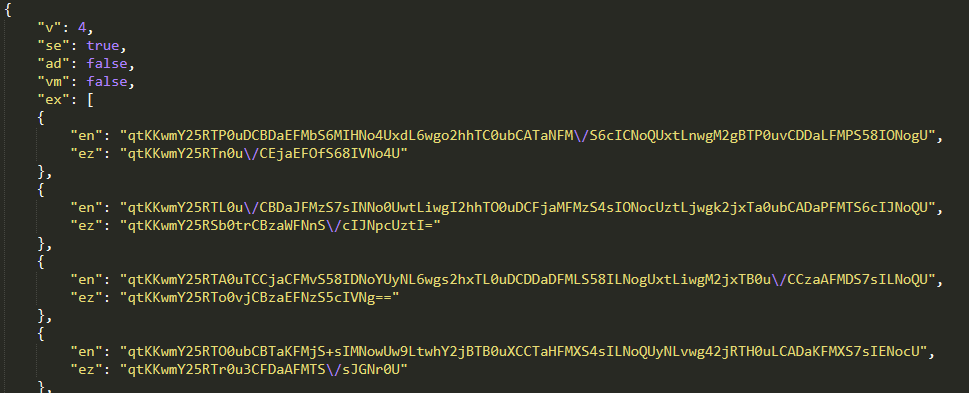
The Person-Agent string is necessary to observe, as offering it appropriately is crucial for receiving the dynamic configuration. In April 2025, Lumma Stealer launched an extra layer of obfuscation by encrypting JSON values utilizing an 8-byte XOR perform (see Determine 14).
This encrypted variant of the dynamic configuration is delivered when a barely up to date Person-Agent string is specified (see Desk 2).
Desk 2. Person-Agent variants
| Person-Agent | Description |
| Mozilla/5.0 (Home windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 | Outdated Person-Agent string leading to a dynamic configuration variant proven in Determine 13. |
| Mozilla/5.0 (Home windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36 | New Person-Agent string leading to a dynamic configuration variant with encryption of some values (Determine 14). |
In addition to this dynamic configuration strategy, Lumma Stealer samples nonetheless comprise hardcoded directions for exfiltrating recordsdata. These embody information from purposes akin to Outlook or Thunderbird, Steam account data, and Discord account tokens (see this SpyCloud blogpost). This mix of dynamic and hardcoded configurations ensures that Lumma Stealer can successfully acquire a variety of precious information.
To summarize all of the static and dynamic modifications talked about thus far, now we have created a timeline (Determine 15) highlighting probably the most vital developments noticed within the Lumma Stealer malware over the previous yr.
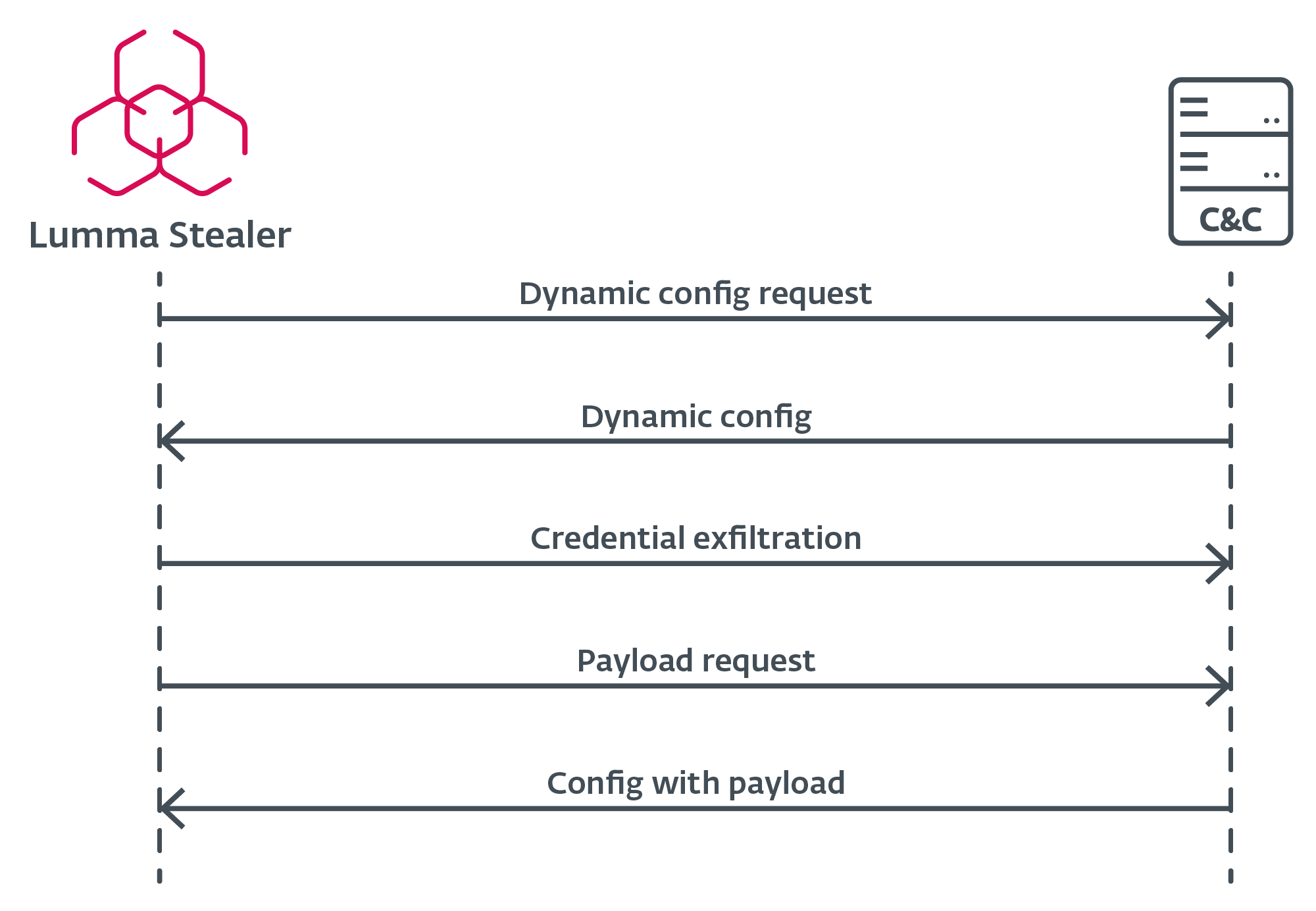
C&C communication
All through our Lumma Stealer monitoring interval, all extracted C&C domains constantly led to Cloudflare providers, that are utilized to hide Lumma Stealer’s actual C&C infrastructure. Cloudflare providers are additionally employed for C&C servers positioned through dead-drop resolvers.
First, Lumma Stealer must get hold of an lively C&C server. The mechanism of this selection is illustrated within the movement chart proven in Determine 16.
Handshake
Though the precise handshake request to the C&C server isn’t current within the newest Lumma Stealer builds, it’s price mentioning as a result of it was a characteristic of our monitoring for a very long time. The handshake request was an HTTPS POST request containing act=dwell and a hardcoded Person-Agent. Lively servers responded with a cleartext okay message.
Configuration request
When Lumma Stealer identifies an lively C&C server, it requests the configuration through an HTTPS POST request (Determine 17), which incorporates the LID and J parameters as information. If the J parameter isn’t current within the pattern, Lumma Stealer retrieves the default configuration from the C&C server. This configuration specifies what to scan for exfiltration, permitting the malware to adapt to totally different targets and environments.
Extra payload execution
After Lumma Stealer efficiently exfiltrates delicate information and harvested credentials, it points one ultimate HTTPS POST request to the C&C server – this time, with an extra sufferer {hardware} ID referred to as hwid. This ultimate request retrieves a configuration of an extra payload to be executed on the sufferer’s machine. The payload or a URL to obtain from is a part of that configuration. Notice that such a payload isn’t at all times offered.
Anti-analysis obfuscation methods
Lumma Stealer employs a number of, however efficient, anti-emulation methods to make evaluation as sophisticated as potential. These methods are designed to evade detection and hinder the efforts of safety analysts.
Oblique soar obfuscation
One of many main obfuscation methods utilized by Lumma Stealer is oblique management movement flattening, proven in Determine 18. This methodology successfully disrupts the code blocks of the capabilities, making it practically unimaginable to maintain monitor of the perform logic. By flattening the management movement, the malware obfuscates its operations, complicating the evaluation course of. For an in depth exploration of this method and thorough evaluation of those obfuscation patterns, together with an overview of the answer, you possibly can confer with this complete article by Mandiant.
Stack strings
One other approach employed by Lumma Stealer is the usage of encrypted stack strings, as illustrated in Determine 19. This methodology successfully hides binary information and lots of necessary strings within the Lumma Stealer pattern, making static evaluation of the binary troublesome. Furthermore, every encrypted string has its personal distinctive mathematical perform for decryption, including one other layer of complexity to the evaluation course of.
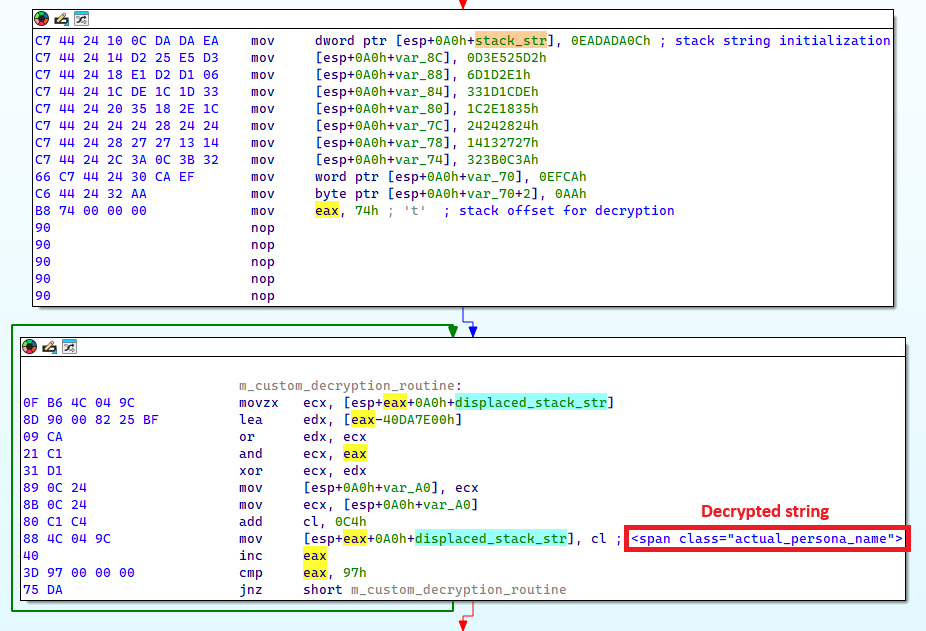
Import API obfuscation
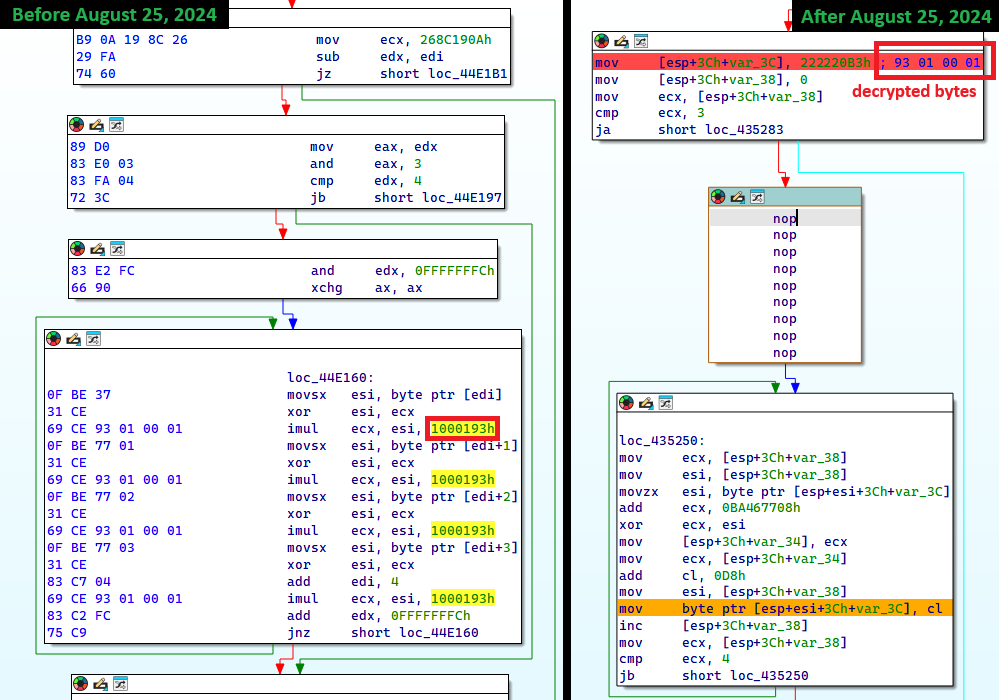
In Lumma Stealer, imports are resolved at runtime. Import names are hashed utilizing the FNV-1a algorithm with every construct utilizing a customized offset foundation. As proven in Determine 20, since August 25th, 2024, Lumma Stealer additionally obfuscates the FNV hash algorithm parameters by utilizing stack strings.
Conclusion
This international disruption operation was made potential by our long-term monitoring of Lumma Stealer, which now we have offered an outline of on this blogpost. We have now described the modus operandi of the Lumma Stealer group and its service. Moreover, now we have documented the necessary static identifiers and C&C communication in addition to its evolution during the last yr. Lastly, we summarized the important thing obfuscation methods that make the evaluation of Lumma Stealer difficult.
The disruption operation, led by Microsoft, goals to grab all identified Lumma Stealer C&C domains, rendering Lumma Stealer’s exfiltration infrastructure nonfunctional. ESET will proceed to trace different infostealers whereas carefully monitoring for Lumma Stealer exercise following this disruption operation.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at [email protected].ESET Analysis provides personal APT intelligence stories and information feeds. For any inquiries about this service, go to the ESET Threat Intelligence web page.
IoCs
SHA-1
Filename
Detection
Description
6F94CFAABB19491F2B8E
AcroRd32.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer pattern – Construct 2024-06-27.
C5D3278284666863D758
Notion.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer pattern – Construct 2024-07-14.
5FA1EDC42ABB42D54D98
explorer.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer pattern – Construct 2024-08-08.
0D744811CF41606DEB41
aspnet_regiis
Win32/Spy.Lumma Stealer.B
Lumma Stealer pattern – Construct 2024-08-25.
2E3D4C2A7C68DE2DD31A
nslookup.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer pattern – Construct 2024-09-20.
09734D99A278B3CF59FE
nslookup.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer pattern – Construct 2024-10-04.
1435D389C72A5855A5D6
BitLockerToGo
Win32/Spy.Lumma Stealer.B
Lumma Stealer pattern – Construct 2024-11-09.
2CCCEA9E1990D6BC7755
exterior.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer pattern – Construct 2024-12-23.
658550E697D9499DB782
Wemod-Premium-Unlocker-2025
MSIL/GenKryptik.HGWU
Lumma Stealer pattern – Construct 2025-01-18.
070A001AC12139CC1238
khykuQw.exe
Win32/Kryptik.HYUC
Lumma Stealer pattern – Construct 2025-02-27.
1FD806B1A0425340704F
Begin.exe
Win64/Injector.WR
Lumma Stealer pattern – Construct 2025-03-24.
F4840C887CAAFF0D5E07
loader.exe
Win64/Kryptik.FAZ
Lumma Stealer pattern – Construct 2025-04-15.
8F58C4A16717176DFE3C
Set-up.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer pattern – Construct 2025-04-23.
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 172.67.134[.]100 | cooperatvassquaidmew[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 172.67.175[.]165 | crisisrottenyjs[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 188.114.96[.]1 | deadtrainingactioniw[.]xyz tamedgeesy[.]sbs nighetwhisper[.]high |
Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 172.67.141[.]43 | exuberanttjdkwo[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 188.114.96[.]3 | grandcommonyktsju[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 104.21.92[.]96 | qualificationjdwko[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 172.67.209[.]200 | sweetcalcutangkdow[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 104.21.49[.]80 | wordingnatturedowo[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 188.114.97[.]0 | bigmouthudiop[.]store froytnewqowv[.]store locatedblsoqp[.]store stagedchheiqwo[.]store |
Cloudflare, Inc. | 2024‑07‑16 | Lumma Stealer C&C server. |
| 104.21.19[.]156 | callosallsaospz[.]store | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.153[.]40 | indexterityszcoxp[.]store | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.192[.]52 | lariatedzugspd[.]store | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.213[.]85 | liernessfornicsa[.]store | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.137[.]78 | outpointsozp[.]store | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.221[.]214 | shepherdlyopzc[.]store | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.204[.]158 | unseaffarignsk[.]store | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.178[.]194 | upknittsoappz[.]store | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 188.114.97[.]3 | bassizcellskz[.]store byteplusx[.]digital sparkiob[.]digital longitudde[.]digital |
Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 104.21.47[.]141 | celebratioopz[.]store | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 172.67.158[.]159 | complaintsipzzx[.]store | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 172.67.204[.]20 | deallerospfosu[.]store | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 104.21.35[.]48 | languagedscie[.]store | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 104.21.73[.]43 | mennyudosirso[.]store | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 188.114.97[.]9 | quialitsuzoxm[.]store | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 172.67.166[.]231 | writerospzm[.]store | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 104.21.16[.]180 | caffegclasiqwp[.]store | Cloudflare, Inc. | 2024‑08‑24 | Lumma Stealer C&C server. |
| 172.67.146[.]35 | condedqpwqm[.]store | Cloudflare, Inc. | 2024‑08‑24 | Lumma Stealer C&C server. |
| N/A | evoliutwoqm[.]store | N/A | 2024‑08‑24 | Lumma Stealer C&C server. |
| 188.114.96[.]0 | millyscroqwp[.]store stamppreewntnq[.]store advennture[.]high |
Cloudflare, Inc. | 2024‑08‑24 | Lumma Stealer C&C server. |
| 104.21.67[.]155 | traineiwnqo[.]store | Cloudflare, Inc. | 2024‑08‑24 | Lumma Stealer C&C server. |
| 94.140.14[.]33 | achievenmtynwjq[.]store carrtychaintnyw[.]store chickerkuso[.]store metallygaricwo[.]store milldymarskwom[.]store opponnentduei[.]store puredoffustow[.]store quotamkdsdqo[.]store bemuzzeki[.]sbs exemplarou[.]sbs exilepolsiy[.]sbs frizzettei[.]sbs invinjurhey[.]sbs isoplethui[.]sbs laddyirekyi[.]sbs wickedneatr[.]sbs |
Cloudflare, Inc. | 2024‑09‑21 | Lumma Stealer C&C server. |
| 188.114.97[.]4 | usseorganizedw[.]store bellflamre[.]click on tripfflux[.]world |
Cloudflare, Inc. | 2024‑09‑24 | Lumma Stealer C&C server. |
| 104.21.44[.]84 | beerishint[.]sbs | Cloudflare, Inc. | 2024‑10‑06 | Lumma Stealer C&C server. |
| 104.21.64[.]84 | 1212tank.activitydmy[.]icu | Cloudflare, Inc. | 2024‑11‑12 | Lumma Stealer C&C server. |
| 104.21.93[.]246 | brownieyuz[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 172.67.189[.]210 | ducksringjk[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 172.67.146[.]64 | explainvees[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 104.21.90[.]226 | relalingj[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 104.21.14[.]17 | repostebhu[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 172.67.192[.]43 | rottieud[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 188.114.97[.]1 | thinkyyokej[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 188.114.97[.]7 | bashfulacid[.]lat tentabatte[.]lat |
Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 104.21.86[.]54 | curverpluch[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 104.21.66[.]86 | lev‑tolstoi[.]com | Cloudflare, Inc. | 2024‑12‑17 | Lumma Stealer C&C server. |
| 172.64.80[.]1 | manyrestro[.]lat toppyneedus[.]biz |
Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 188.114.97[.]2 | shapestickyr[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 172.67.192[.]247 | slipperyloo[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 104.105.90[.]131 | steamcommunity[.]com steamcommunity[.]com |
Akamai Applied sciences, Inc. | 2024‑06‑27 | Steam profile lifeless‑drop resolvers. |
| 172.67.146[.]68 | talkynicer[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 172.67.184[.]241 | wordyfindy[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| N/A | beevasyeip[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | broadecatez[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | encirelk[.]cyou | N/A | 2025‑01‑28 | Lumma Stealer C&C server. |
| N/A | granystearr[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | quarrelepek[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | rockemineu[.]bond | N/A | 2025‑01‑28 | Lumma Stealer C&C server. |
| 104.21.19[.]91 | suggestyuoz[.]biz | Cloudflare, Inc. | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | tranuqlekper[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| 104.21.69[.]194 | codxefusion[.]high | Cloudflare, Inc. | 2025‑02‑28 | Lumma Stealer C&C server. |
| 104.21.80[.]1 | earthsymphzony[.]right now climatologfy[.]high |
Cloudflare, Inc. | 2025‑02‑26 | Lumma Stealer C&C server. |
| 104.21.88[.]16 | experimentalideas[.]right now | Cloudflare, Inc. | 2025‑03‑01 | Lumma Stealer C&C server. |
| 172.67.146[.]181 | gadgethgfub[.]icu | Cloudflare, Inc. | 2025‑03‑01 | Lumma Stealer C&C server. |
| 104.21.48[.]238 | hardrwarehaven[.]run | Cloudflare, Inc. | 2025‑02‑28 | Lumma Stealer C&C server. |
| 104.21.16[.]1 | hardswarehub[.]right now pixtreev[.]run |
Cloudflare, Inc. | 2025‑02‑28 | Lumma Stealer C&C server. |
| 104.21.39[.]95 | quietswtreams[.]life | Cloudflare, Inc. | 2025‑02‑26 | Lumma Stealer C&C server. |
| 172.67.222[.]46 | socialsscesforum[.]icu | Cloudflare, Inc. | 2025‑03‑03 | Lumma Stealer C&C server. |
| 172.67.191[.]187 | techmindzs[.]dwell | Cloudflare, Inc. | 2025‑03‑01 | Lumma Stealer C&C server. |
| 172.67.214[.]226 | techspherxe[.]high | Cloudflare, Inc. | 2025‑03‑01 | Lumma Stealer C&C server. |
| 104.21.26[.]124 | appgridn[.]dwell | Cloudflare, Inc. | 2025‑03‑24 | Lumma Stealer C&C server. |
| 172.67.178[.]7 | lunoxorn[.]high | Cloudflare, Inc. | 2025‑03‑31 | Lumma Stealer C&C server. |
| 104.21.47[.]117 | skynetxc[.]dwell | Cloudflare, Inc. | 2025‑03‑24 | Lumma Stealer C&C server. |
| 104.21.72[.]121 | targett[.]high | Cloudflare, Inc. | 2025‑03‑20 | Lumma Stealer C&C server. |
| 188.114.96[.]2 | travewlio[.]store | Cloudflare, Inc. | 2025‑03‑20 | Lumma Stealer C&C server. |
| 104.21.42[.]7 | changeaie[.]high | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 104.21.85[.]126 | clarmodq[.]high | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 172.67.161[.]40 | liftally[.]high | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 172.67.176[.]107 | piratetwrath[.]run | Cloudflare, Inc. | 2025‑04‑17 | Lumma Stealer C&C server. |
| 172.67.215[.]114 | quilltayle[.]dwell | Cloudflare, Inc. | 2025‑04‑17 | Lumma Stealer C&C server. |
| 172.67.143[.]12 | salaccgfa[.]high | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 104.21.5[.]146 | starofliught[.]high | Cloudflare, Inc. | 2025‑04‑17 | Lumma Stealer C&C server. |
| 104.21.32[.]1 | zestmodp[.]high | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 172.67.147[.]123 | equatorf[.]run | Cloudflare, Inc. | 2025‑04‑21 | Lumma Stealer C&C server. |
| 104.21.112[.]1 | hemispherexz[.]high | Cloudflare, Inc. | 2025‑04‑21 | Lumma Stealer C&C server. |
| 104.21.20[.]106 | latitudert[.]dwell | Cloudflare, Inc. | 2025‑04‑21 | Lumma Stealer C&C server. |
| 172.67.216[.]12 | sectorecoo[.]dwell | Cloudflare, Inc. | 2025‑04‑19 | Lumma Stealer C&C server. |
MITRE ATT&CK methods
This desk was constructed utilizing version 17 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
| Useful resource Growth | T1587.001 | Develop Capabilities: Malware | Lumma Stealer operators actively developed their malware as a product for his or her service. |
| T1583.001 | Purchase Infrastructure: Domains | Lumma Stealer operators registered domains for his or her exfiltration infrastructure. | |
| T1583.006 | Purchase Infrastructure: Net Providers | Lumma Stealer operators used Cloudflare providers to cover their infrastructure. Lumma Stealer additionally hid its C&C URLs in public providers like dummy Steam profiles or empty Telegram channels. | |
| Execution | T1059.003 | Command-Line Interface: Home windows Command Shell | Lumma Stealer executes cmd.exe to delete momentary recordsdata. |
| T1106 | Native API | Lumma Stealer executes quite a lot of Home windows APIs, together with VirtualAlloc, LoadLibraryA, and GetProcAddress. | |
| T1204.001 | Person Execution: Malicious Hyperlink | Lumma Stealer operators provide a easy LNK packing characteristic for his or her malware builds. | |
| T1047 | Home windows Administration Instrumentation | Lumma Stealer makes use of WMI queries to assemble system data. | |
| Protection Evasion | T1622 | Debugger Evasion | Lumma Stealer checks for debugger presence. |
| T1140 | Deobfuscate/Decode Information or Data | Lumma Stealer makes use of ChaCha20 for C&C record and dynamic config encryption. | |
| T1027.007 | Obfuscated Information or Data: Dynamic API Decision | Lumma Stealer resolves API names at runtime utilizing the FNV-1a hash algorithm. | |
| T1027.013 | Obfuscated Information or Data: Encrypted/Encoded File | Lumma Stealer encrypts strings and necessary binary information utilizing stack strings or ChaCha20. | |
| Credential Entry | T1555.003 | Credentials from Password Shops: Credentials from Net Browsers | Lumma Stealer gathers credentials from a number of browsers. |
| T1539 | Steal Net Session Cookie | Lumma Stealer gathers cookies from a number of browsers. | |
| Discovery | T1217 | Browser Bookmark Discovery | Lumma Stealer checks and collects varied details about put in browsers on victims’ machines. |
| T1012 | Question Registry | Lumma Stealer queries registry keys to record put in software program on victims’ machines. | |
| T1057 | Course of Discovery | Lumma Stealer sends the method record to its C&C server. | |
| T1518 | Software program Discovery | Lumma Stealer sends an inventory of put in software program to its C&C server. | |
| T1082 | System Data Discovery | Lumma Stealer sends system data to its C&C server. | |
| T1124 | System Time Discovery | Lumma Stealer sends the present system time and time zone to its C&C server. | |
| Assortment | T1560 | Archive Collected Information | Lumma Stealer compresses gathered information earlier than exfiltration to its C&C server. |
| T1119 | Automated Assortment | Lumma Stealer’s exfiltration capabilities are absolutely automated and based mostly on a configuration file. | |
| T1113 | Display screen Seize | Lumma Stealer takes screenshots of victims’ machines based mostly on dynamic configuration. | |
| T1005 | Information from Native System | Lumma Stealer collects native system information from victims’ machines. | |
| Command and Management | T1071.001 | Software Layer Protocol: Net Protocols | Lumma Stealer makes use of HTTPS communication with its C&C servers. |
| T1132.001 | Information Encoding: Customary Encoding | Lumma Stealer used base64 encoding for acquiring its configuration from the C&C server. | |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | Lumma Stealer makes use of further ChaCha20 encryption beneath the HTTPS community protocol. | |
| T1008 | Fallback Channels | Lumma Stealer employs backup dead-drop resolvers in Steam profiles and Telegram channels. | |
| T1102.001 | Net Service: Lifeless Drop Resolver | Lumma Stealer employs backup dead-drop resolvers in Steam profiles and Telegram channels. | |
| Exfiltration | T1020 | Automated Exfiltration | Lumma Stealer exfiltrates stolen credentials and information over the C&C channel. |
| T1041 | Exfiltration Over C2 Channel | Lumma Stealer exfiltrates stolen credentials and information over the C&C channel. |














Seasoned gambler here, and I have spent several seasons in digital gambling. I learned control through profits and setbacks. Consistency became my main rule. Quick wins rarely work. Experience always matters. Recently I had a strong run while playing digitally. I used my usual approach. Bet sizes stayed reasonable. The total started growing. It felt earned. Chance was only a small part here [url=https://lalabetlogin.com/]https://lalabetlogin.com/[/url].
After the win, I stayed focused. I checked the rules and conditions. The payout process was smooth. Funds arrived on time. That moment confirmed my method. Discipline once again worked.
I share this as a real case. This is not bragging. Casino wins are real. They require time. Smart play beats emotion. Steady thinking brings results.
Ребята, подскажите, по каким критериям вы выбираете даркнет магазины? Что для вас важно при выборе?
Я обычно смотрю на:
– Репутацию и отзывы
– Рейтинг магазина
– Время работы на рынке
– Наличие поддержки
– Актуальность ссылок
Для сравнения магазинов использую [url=https://rc24.pro]rc24.pro[/url] – там есть рейтинг магазинов с подробной информацией о каждом. Можно посмотреть статус работы, описание, категории товаров. Это помогает сделать правильный выбор и не нарваться на мошенников.
Какие еще критерии важны при выборе магазина? Что посоветуете новичкам?
becem travel | Kıbrıs araç transfer Kıbrıs araç kiralama , Kıbrıs vip araç , Kıbrıs araç transfer , Kıbrıs güvenli ulaşım
Düzce Egemer Mermer Granit Akrilik tezgah uygulaması temiz işçilikle tamamlandı ve ortaya çıkan sonuç oldukça memnun ediciydi.https://egemermergranit.com.tr/
Your content never disappoints. Keep up the great work!
Deluxe Promosyon | 2026 Promosyon ürünleri eşantiyon hediyelik, ajanda 2025, promosyon ucuz, hızlı promosyon ürünü, kalem yapımı promosyon
Your timing with this post is absolutely perfect! I’ve been trying to figure this out on my own for ages, and you just saved me probably weeks of trial and error. The detailed breakdown you provided is incredibly helpful, and I appreciate that you included both the theory and the practical application. Your writing is so clear and engaging that it never feels like a chore to read, even when you’re covering complex material. Thank you for sharing your expertise so generously!
I agree with your point of view and found this very insightful.
Hi there to all, for the reason that I am genuinely keen of reading this website’s post to be updated on a regular basis. It carries pleasant stuff.
Güzel aydınlatıcı makale için teşekkürler daha iyisi samda kayısı umarım faydalı çalışmalarınızın devamı gelir.
Düzce Egemer Mermer Granit’ten yaptırdığımız porselen tezgah hem görünüm hem de kullanım açısından beklentimizin üzerinde oldu.https://egemermergranit.com.tr/