Should you’ve ever owned a site title, the possibilities are good that sooner or later you’ve obtained a snail mail letter which seems to be a invoice for a site or website-related providers. In actuality, these deceptive missives attempt to trick individuals into paying for ineffective providers they by no means ordered, don’t want, and doubtless won’t ever obtain. Right here’s a have a look at the newest incarnation of this rip-off — DomainNetworks — and a few clues about who could also be behind it.
The DomainNetworks mailer could reference a site that’s or was at one level registered to your title and handle. Though the letter contains the phrases “advertising and marketing providers” within the higher proper nook, the remainder of the missive is deceptively designed to appear to be a invoice for providers already rendered.
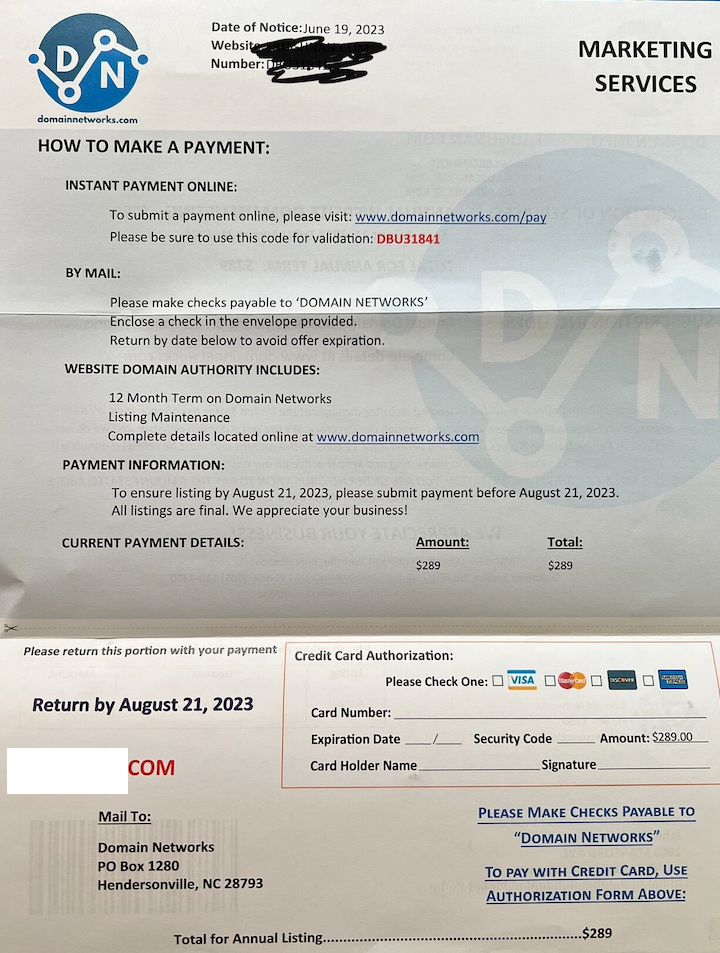
DomainNetworks claims that itemizing your area with their promotion providers will end in elevated site visitors to your web site. This can be a doubtful declare for a corporation that seems to be an entire fabrication, as we’ll see in a second. However fortunately, the proprietors of this enterprise weren’t so troublesome to trace down.
The web site Domainnetworks[.]com says it’s a enterprise with a put up workplace field in Hendersonville, N.C., and one other handle in Santa Fe, N.M. There are just a few random, non-technology companies tied to the cellphone quantity listed for the Hendersonville handle, and the New Mexico handle was utilized by a number of no-name hosting corporations.
Nonetheless, there may be little linked to those addresses and cellphone numbers that get us any nearer to discovering out who’s working Domainnetworks[.]com. And neither entity seems to be an lively, official firm of their supposed state of residence, a minimum of in accordance with every state’s Secretary of State database.
The Higher Enterprise Bureau listing for DomainNetworks provides it an “F” ranking, and contains greater than 100 opinions by individuals indignant at receiving certainly one of these scams through snail mail. Helpfully, the BBB says DomainNetworks beforehand operated below a special title: US Area Authority LLC.
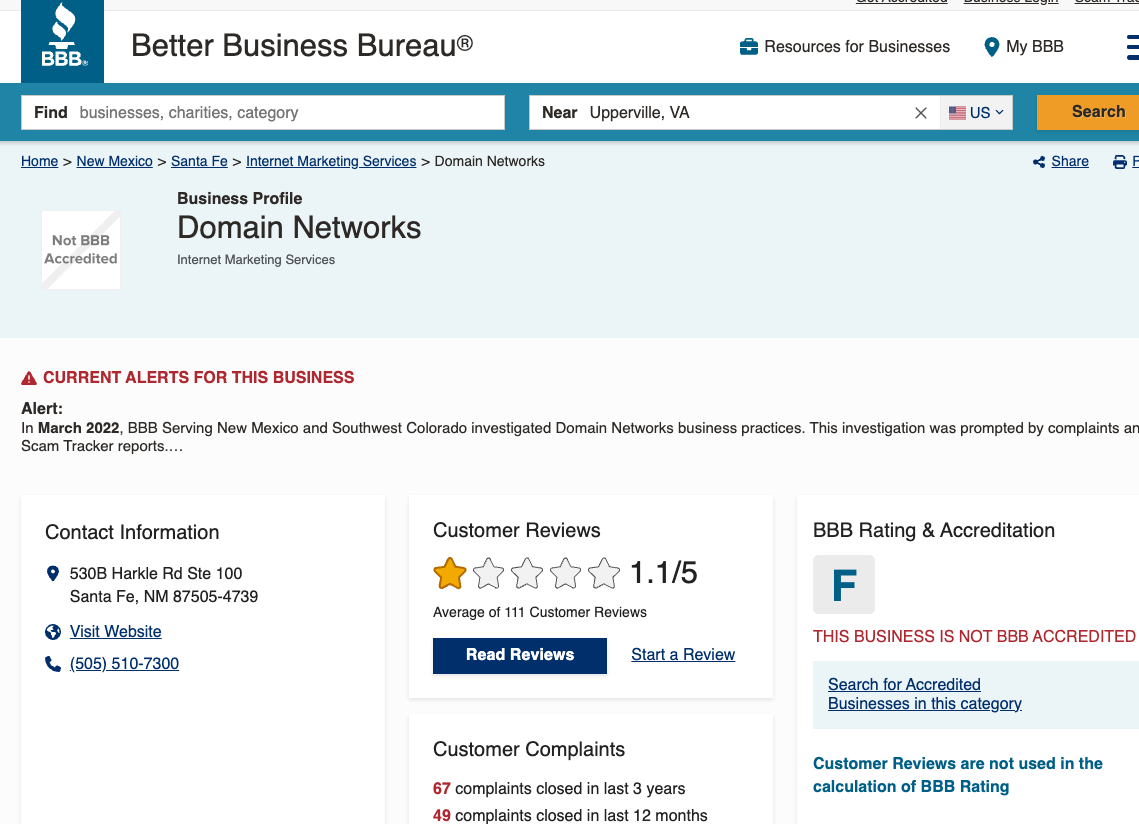
DomainNetworks has an “F” status with the Higher Enterprise Bureau.
Copies of snail mail rip-off letters from US Area Authority posted on-line present that this entity used the area usdomainauthority[.]com, registered in Might 2022. The Usdomainauthority mailer additionally featured a Henderson, NC handle, albeit at a special put up workplace field.
Usdomainauthority[.]com is now not on-line, and the positioning appears to have blocked its pages from being listed by the Wayback Machine at archive.org. However looking out on a protracted snippet of textual content from DomainNetworks[.]com about refund requests reveals that this textual content was discovered on only one different lively web site, in accordance with publicwww.com, a service that indexes the HTML code of current web sites and makes it searchable.
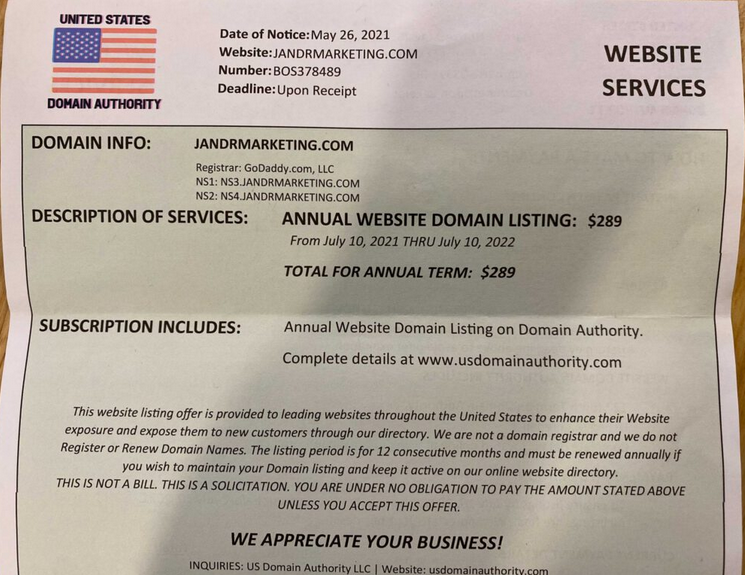
A misleading snail mail solicitation from DomainNetwork’s earlier iteration — US Area Authority. Picture: Joerussori.com
That different web site is a site registered in January 2023 known as thedomainsvault[.]com, and its registration particulars are likewise hidden behind privateness providers. Thedomainsvault’s “Regularly Requested Questions” web page is kind of just like the one on the DomainNetworks web site; each start with the query of why the corporate is sending a mailer that appears like a invoice for area providers.
Thedomainsvault[.]com contains no helpful details about the entity or individuals who function it; clicking the “Contact-us” hyperlink on the positioning brings up a web page with placeholder Lorem Ipsum text, a contact kind, and a cellphone variety of 123456789.
Nonetheless, looking out passive DNS records at DomainTools.com for thedomainsvault[.]com reveals that sooner or later whoever owns the area instructed incoming e mail to be despatched to [email protected].
The primary consequence that at the moment pops up when trying to find “ubsagency” in Google is ubsagency[.]com, which says it belongs to a Las Vegas-based Search Engine Optimization (search engine marketing) and digital advertising and marketing concern generically named each United Enterprise Service and United Enterprise Providers. UBSagency’s web site is hosted on the identical Ann Arbor, Mich. primarily based internet hosting agency (A2 Internet hosting Inc) as thedomainsvault[.]com.
UBSagency’s LinkedIn page says the corporate has places of work in Vegas, Half Moon Bay, Calif., and Renton, Wash. However as soon as once more, not one of the addresses listed for these places of work reveal any apparent clues about who runs UBSagency. And as soon as once more, none of those entities seem to exist as official companies of their claimed state of residence.
Looking on [email protected] in Constella Intelligence reveals the handle was used someday earlier than February 2019 to create an account below the title “SammySam_Alon” on the inside adorning web site Houzz.com. In January 2019, Houzz acknowledged {that a} knowledge breach uncovered account info on an undisclosed variety of clients, together with consumer IDs, one-way encrypted passwords, IP addresses, metropolis and ZIP codes, in addition to Fb info.
SammySam_Alon registered at Houzz utilizing an Web handle in Huntsville, Ala. (68.35.149.206). Constella says this handle was related to the e-mail [email protected], which is also tied to a number of different “Sammy” accounts at totally different shops on-line.
Constella additionally says a extremely distinctive password re-used by [email protected] throughout quite a few websites was utilized in reference to just some different e mail accounts, together with [email protected], and [email protected].
The [email protected] handle was used to register a Twitter account for a Sam Orit Alon in 2013, whose account says they’re affiliated with the Shenhav Group. Based on DomainTools, [email protected] was liable for registering roughly two dozen domains, together with the now-defunct unitedbusinessservice[.]com.
Constella additional finds that the handle [email protected] was used to register an account at whmcs.com, a hosting platform that suffered a breach of its consumer database a number of years again. The title on the WHMCS account was Shmuel Orit Alon, from Kidron, Israel.
UBSagency additionally has a Facebook page, or perhaps “had” is the operative phrase as a result of somebody seems to have defaced it. Loading the Fb web page for UBSagency reveals a number of of the pictures have been overlaid or changed with a message from somebody who’s actually disillusioned with Sam Alon.
“Sam Alon is a LIAR, THIEF, COWARD AND HAS A VERY SMALL D*CK,” reads one of many messages:

The present Fb profile web page for UBSagency features a brand that’s just like the DomainNetworks brand.
The emblem within the UBSagency profile picture features a graphic of what seems to be a magnifying glass with a line that zig-zags by bullet factors inside and out of doors the circle, a singular sample that’s remarkably just like the brand for DomainNetworks:

The logos for DomainNetworks (left) and UBSagency.
Constella additionally discovered that the identical Huntsville IP handle utilized by Sam Alon at Houzz was related to yet one more Houzz account, this one for somebody named “Eliran.”
The UBSagency Fb web page options a number of messages from an Eliran “Dani” Benz, who’s referred to by commenters as an worker or companion with UBSagency. The final check-in on Benz’s profile is from a seaside at Rishon Letziyon in Israel earlier this 12 months.
Neither Mr. Alon nor Mr. Benz responded to a number of requests for remark.
It might be troublesome to imagine that anybody would pay an bill for a site title or search engine marketing service they by no means ordered. Nonetheless, there may be loads of proof that these phony payments typically get processed by administrative personnel at organizations that find yourself paying the requested quantity as a result of they assume it was owed for some providers already offered.
In 2018, KrebsOnSecurity printed How Internet Savvy are Your Leaders?, which examined public information to indicate that dozens of cities, cities, college districts and even political campaigns throughout the US bought snookered into paying these rip-off area invoices from the same rip-off firm known as WebListings Inc.
In 2020, KrebsOnSecurity featured a deep dive into who was likely behind the WebListings scam, which had been sending out these snail mail rip-off letters for over a decade. That investigation revealed the rip-off’s connection to a multi-level advertising and marketing operation run out of the U.Ok., and to 2 brothers residing in Scotland.















